Stay Nation has confirmed that Ticketmaster suffered an information breach after its information was stolen from a third-party cloud database supplier, which is believed to be Snowflake.
“On May 20, 2024, Live Nation Entertainment, Inc. (the “Firm” or “we”) identified unauthorized activity within a third-party cloud database environment containing Company data (primarily from its Ticketmaster LLC subsidiary) and launched an investigation with industry-leading forensic investigators to understand what happened,” Stay Nation shared in a Friday evening SEC submitting.
“On May 27, 2024, a criminal threat actor offered what it alleged to be Company user data for sale via the dark web.”
“We are working to mitigate risk to our users and the Company, and have notified and are cooperating with law enforcement. As appropriate, we are also notifying regulatory authorities and users with respect to unauthorized access to personal information.”
Whereas the breach has allegedly uncovered the information of over 560 million Ticketmaster customers, the corporate states that they don’t imagine that the breach can have a cloth impression on the general enterprise operations or its monetary situation.
This admission comes after a risk actor often called Shiny Hunters has been trying to promote the Ticketmaster information on a hacking discussion board for $500,000.
The allegedly stolen databases supposedly comprise 1.3TB of knowledge, together with prospects’ full particulars (i.e., names, dwelling and e-mail addresses, and telephone numbers), in addition to ticket gross sales, order, and occasion data for 560 million prospects.
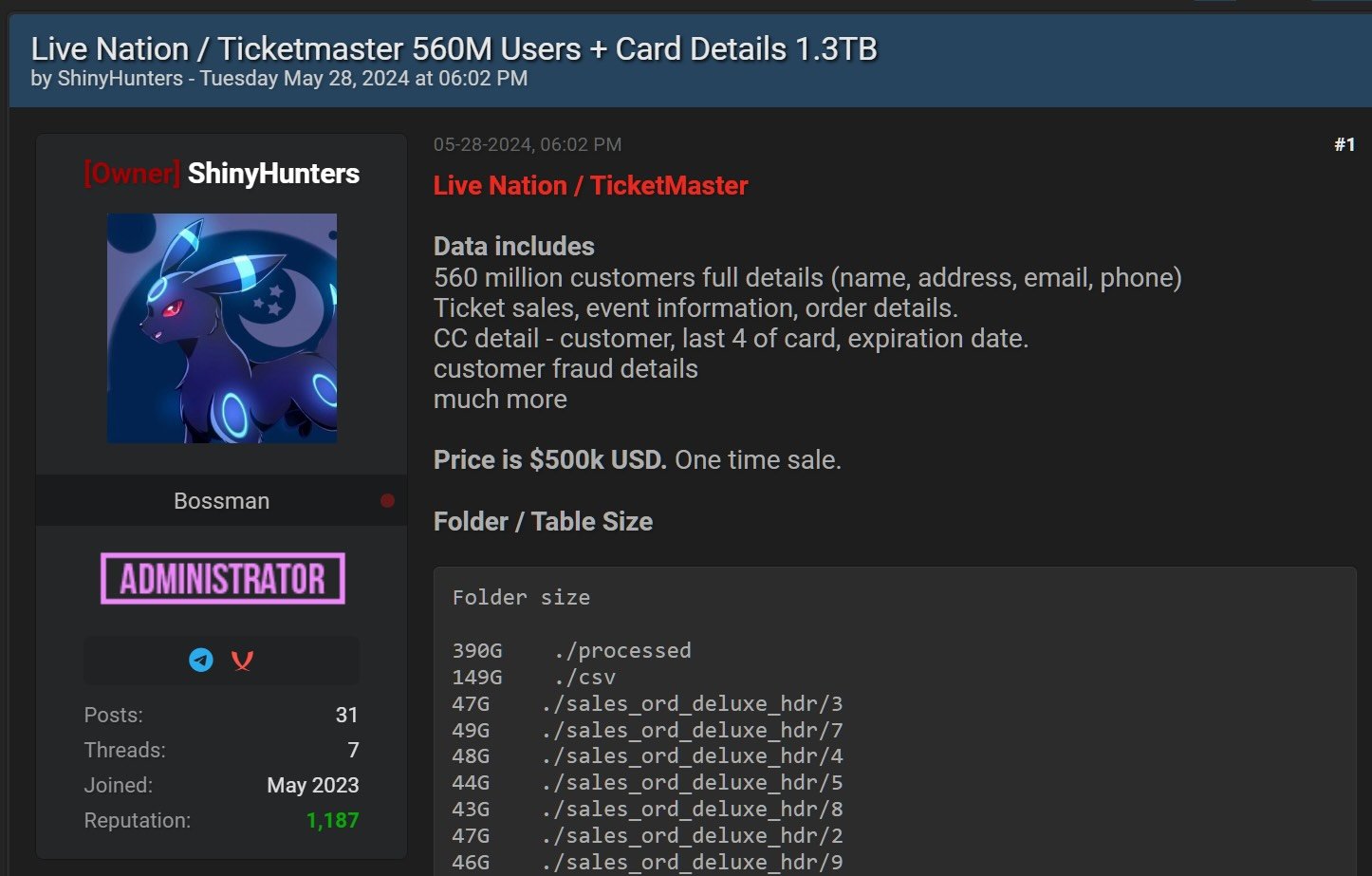
Supply: BleepingComputer
In a dialog with the risk actor, ShinyHunters instructed BleepingComputer that there have been patrons within the information. They believed that one of many patrons that approached them was Ticketmaster themselves.
When requested how they stole the information, the risk actor mentioned they “can’t say anything about this.”
Nonetheless, as we speak, extra data was revealed on how the risk actors gained entry to the Ticketmaster database and probably the information of many different prospects.
Alon Gal of Hudson Rock spoke to one of many risk actors behind the assault, who claimed they have been answerable for latest Santander and Ticketmaster information breaches and mentioned they stole the information from cloud storage firm Snowflake.
Based on the risk actor, they used credentials stolen utilizing information-stealing malware to breach a Snowflake worker’s ServiceNow account, which they used to exfiltrate data from the corporate. This data included unexpired auth tokens that may very well be used to create session tokens and entry buyer accounts to obtain information.
The risk actor claims that they used this methodology to steal information from different corporations, together with Anheuser-Busch, State Farm, Mitsubishi, Progressive, Neiman Marcus, Allstate, and Advance Auto Components.
Progressive and Mistubishi disputed the risk actor’s claims, telling BleepingComputer that there isn’t a indication of any breach of their techniques or information.
Snowflake says the latest breaches have been attributable to poorly secured buyer accounts whose credentials have been stolen and didn’t have multi-factor authentication enabled.
The corporate added that the assaults started in mid-April, with prospects’ information first being stolen on Might 23. Snowflake has shared IOCs from the assaults in order that prospects can question logs to find out in the event that they have been breached.
Mandiant Consulting CTO Charles Carmakal instructed BleepingComputer that Mandiant has been investigating compromised Snowflake shoppers over the previous few weeks and believes their Snowflake tenants have been breached utilizing stolen credentials.
Once we contacted Snowflake to substantiate the risk actor’s claims that they hacked an worker’s account, as an alternative of disputing them, they mentioned that they had nothing additional to share.
This can be a growing story.
