Safety researchers are warning that China-linked state-backed hackers are more and more counting on an unlimited proxy server community created from digital non-public servers and compromised on-line gadgets for cyberespionage operations.
Referred to as operational relay field (ORBs) networks, these proxy meshes are administered by unbiased cybercriminals that present entry to a number of state-sponsored actors (APTs).
ORBs are much like botnets however they could also be a hybrid of commercially leased VPS providers and compromised gadgets, together with end-of-life routers and different IoT merchandise.
The rising use of ORBs by adversaries comes with challenges in each detection and attribution as the assault infrastructure is not managed by the risk actor, who can cycle by way of nodes distributed over a broad geography.
Malicious proxy networks
Cybersecurity agency Mandiant has been monitoring a number of ORBs, two of them utilized by superior risk actors identified for espionage and mental theft operations linked to China.
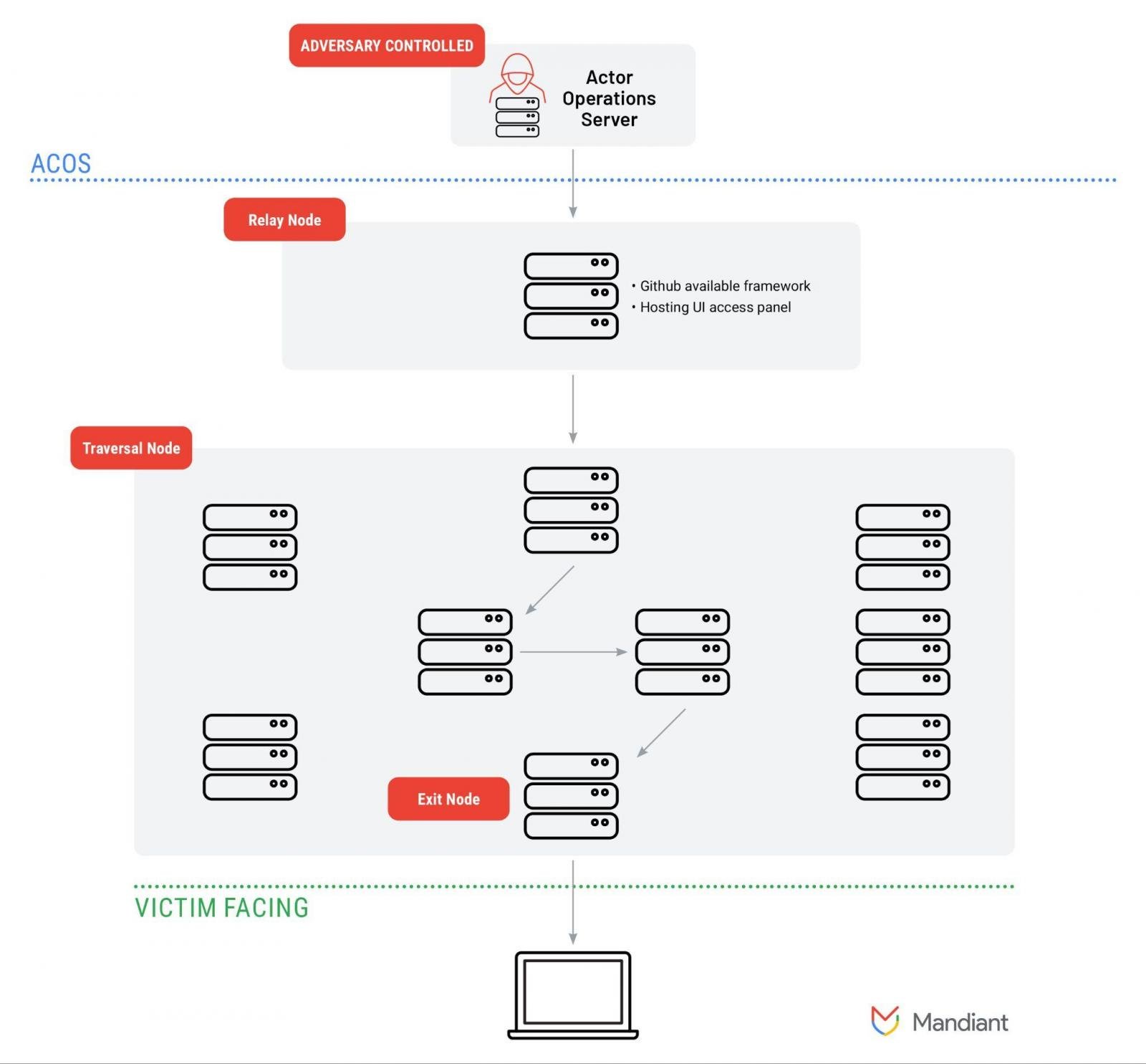
One of them known as ORB3/SPACEHOP is described as “a very active network leveraged by multiple China-nexus threat actors, including APT5 and APT15” for reconnaissance and vulnerability exploitation.
As an illustration, SPACEHOP was utilized in December 2022 to exploit CVE-2022-27518, a essential vulnerability in Citrix ADC and Gateway, which the Nationwide Safety Company (NSA) linked to APT5 (a.okay.a. Manganese, Mulberry Hurricane, Bronze Fleetwood, Keyhole Panda, and UNC2630).
Mandiant researchers say that SPACEHOP is a provisioned community that makes use of a relay server hosted in Hong Kong or China by a cloud supplier. It installs an open-source command and management (C2) framework that permits managing downstream nodes.
The relay nodes are usually cloned Linux-based photos and their function is to proxy malicious visitors to an exit node that communicates with focused sufferer environments.
supply: Mandiant
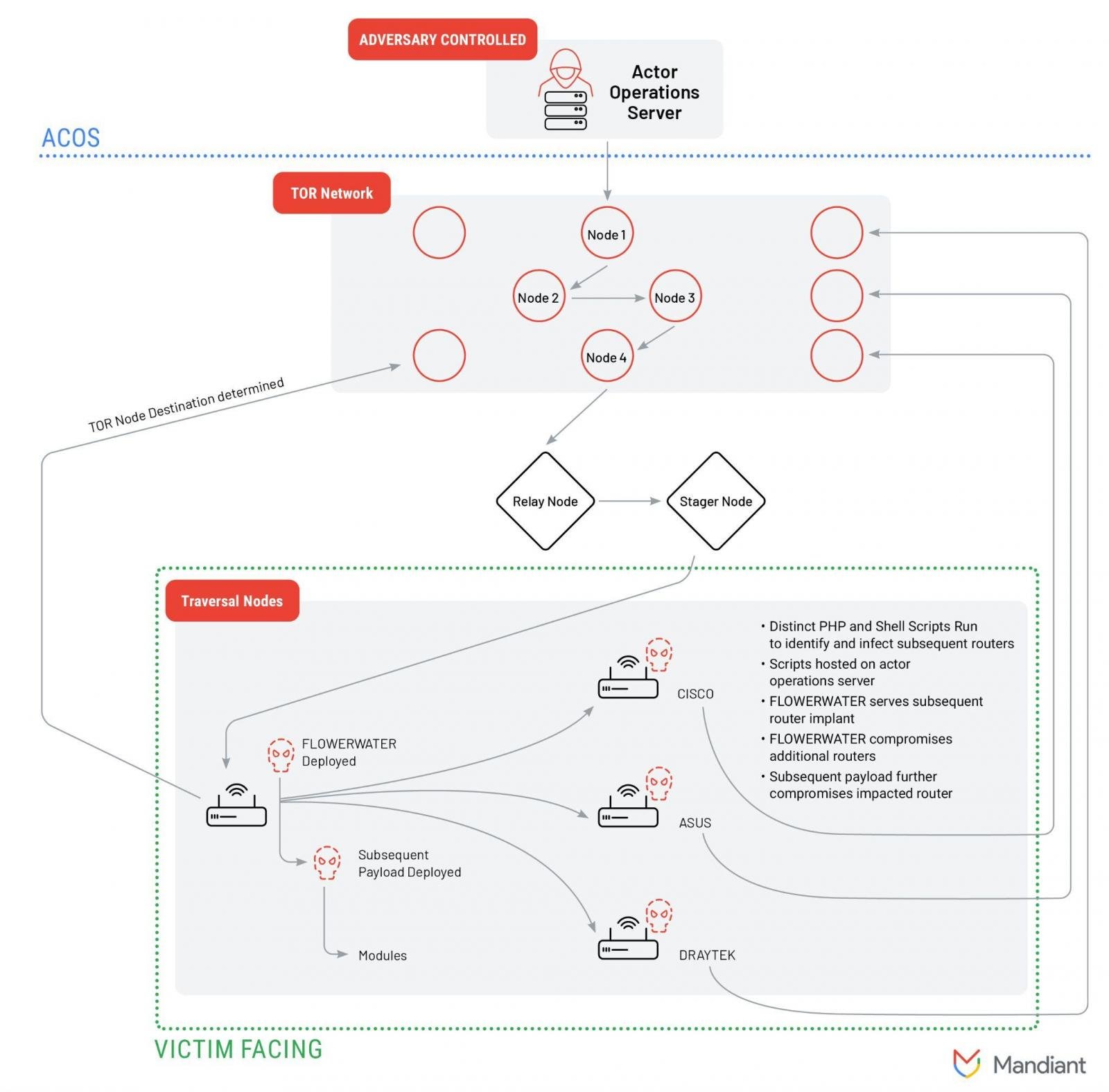
In contrast, ORB2/FLORAHOX is a hybrid community that consists of an Adversary Managed Operations Server (ACOS), compromised linked gadgets (routers and IoT), and VPS providers that run the visitors by way of TOR and a number of hacked routers.
The researchers consider that this mesh is “used in cyber espionage campaigns by a diverse set of China-nexus threat actors” to obfuscate the visitors from the supply.
The community seems to comprise a number of subnetworks composed of compromised gadgets recruited by the router implant FLOWERWATER as nicely as different router-based payloads.
supply: Mandiant
Though ORB2/FLORAHOX is utilized by a number of risk actors, Mandiant says that trusted third-party sources have reported clusters of exercise attributed to China-linked adversaries APT31/Zirconium that concentrate on mental property theft.
“ORB2 represents a more complicated design including the relay of traffic through TOR nodes, provisioned VPS servers, and different types of compromised routers including CISCO, ASUS, and Draytek end-of-life devices” – Mandiant
Aside from FLOWERWATER, the researchers say that extra payloads and instruments (MIPS router tunneler PETALTOWER, SHIMMERPICK bash scripts) are used to navigate the ORB2 community and pre-existing nodes based mostly on command-line inputs.
No matter the kind of gadgets used, an ORB community has a set of important elements that permit it to work correctly:
- Adversary Managed Operations Server (ACOS) – server for administering nodes in an ORB community
- Relay node – lets customers authenticate to the community and relay visitors by way of the bigger traversal pool on ORB nodes
- Traversal nodes – the fundamental nodes composing an ORB community, obfuscate the origin of the visitors
- Exit/Staging nodes – used to launch assaults on targets
- Sufferer server: sufferer infrastructure speaking with the node on the ORB community
Enterprise protection challenges
The usage of ORBs has been noticed previously, probably the most distinguished current instance being the Volt Hurricane assaults on US essential infrastructure organizations utilizing SOHO community gear (e.g. routers, firewalls, and VPN home equipment).
Due to how malicious ORBs perform, they supply stealth, resilience, and independence from the web infrastructure in a rustic.
A number of risk actors use these community infrastructures for restricted intervals, which impacts monitoring them and attribution.
In response to Mandiant, the lifespan of an IPv4 deal with of an ORB node might be as quick as 31 days. This seems to be a function of ORB community contractors in China, who can “cycle significant percentages of their compromised or leased infrastructure on a monthly basis.”
Defenders can miss malicious visitors from these networks as a result of ORB directors use Autonomous System Quantity (ASN) suppliers in varied components of the world.
Aside from making them extra dependable, this additionally permits adversaries to focus on enterprises from gadgets in shut geographic proximity, which raises much less suspicions when analyzing visitors.
“One such example would be traffic from a residential ISP that is in the same geographic location as the target that is regularly used by employees and would be less likely to get picked up for manual review” – Mandiant
With attackers more and more utilizing ORBs, defending enterprise environments turns into much more tough since detection turns into extra complicated, attribution is extra difficult, and indicators for adversary infrastructure are much less helpful for defenders.
