Russian nation-state actor Star Blizzard has been working a brand new spear-phishing marketing campaign to compromise WhatsApp accounts of targets in authorities, diplomacy, protection coverage, worldwide relations, and Ukraine help organizations.
In keeping with a Microsoft Menace Intelligence report, the marketing campaign was noticed in mid-November 2024 and represents a tactical shift for Star Blizzard as a response to the current publicity of the risk actor’s ways, strategies, and procedures.
Malicious WhatsApp invitation
Star Blizzard begins the assault by impersonating a U.S. authorities official in e-mail messages to the goal. The lure is an invite to be part of a WhatsApp group associated to non-governmental initiatives supporting Ukraine.
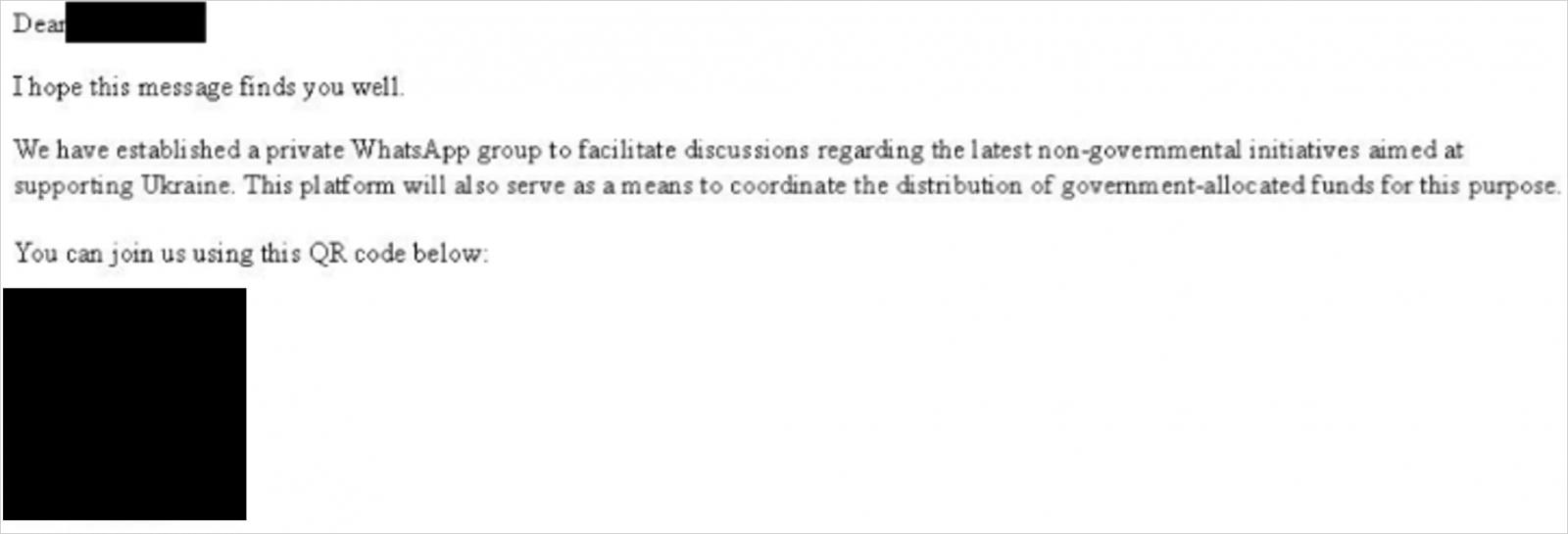
Supply: Microsoft
The e-mail comprises a purposefully damaged QR code, in an try to pressure a reply from the recipient requesting an different hyperlink.
If the sufferer responds, Star Blizzard sends one other e-mail with a ‘t.ly’ quick hyperlink, which directs them to a faux webpage that mimics a official WhatsApp invitation web page with a brand new QR code.
.jpg)
Supply: Microsoft
Nevertheless, the brand new QR code is to hyperlink a brand new gadget, the attacker’s, to the sufferer’s WhatsApp account.
“If the target follows the instructions on this page, the threat actor can gain access to the messages in their WhatsApp account and have the capability to exfiltrate this data using existing browser plugins, which are designed for exporting WhatsApp messages from an account accessed via WhatsApp Web,” explains Microsoft.
Because the assault depends solely on social engineering and there’s no malware concerned for antivirus instruments to detect, customers must be cautious of unsolicited communications and train further warning when receiving invites to affix teams.
It’s also a good suggestion to test the units linked to your WhatsApp account. That is attainable from the “Linked units” choices within the software on the cellular gadget (iPhone or Android) and sign off any gadget you do not acknowledge.
This phishing marketing campaign reveals that Star Blizzard’s exercise disruption in October 2024, when Microsoft and the U.S. Division of Justice seized or took down greater than 180 domains utilized by the Russian risk group, didn’t have a long-term affect and the hackers continued their operations by exploring different assault vectors.
