A brand new Android malware named SpyAgent makes use of optical character recognition (OCR) know-how to steal cryptocurrency pockets restoration phrases from screenshots saved on the cellular machine.
A cryptocurrency restoration phrase, or seed phrase, is a collection of 12-24 phrases that acts as a backup key for a cryptocurrency pockets. These phrases are used to revive entry to your cryptocurrency pockets and all of its funds within the occasion you lose a tool, information is corrupted, otherwise you want to switch your pockets to a brand new machine.
These secret phrases are extremely wanted by risk actors, as if they’ll achieve entry to it, they’ll use it to revive your pockets on their very own units and steal all the funds saved inside it.
As restoration phrases are 12-24 phrases, they’re arduous to recollect, so cryptocurrency wallets inform individuals to avoid wasting or print the phrases and retailer them in a secure place. To make it simpler, some individuals take a screenshot of the restoration phrase and reserve it as a picture of their cellular machine.
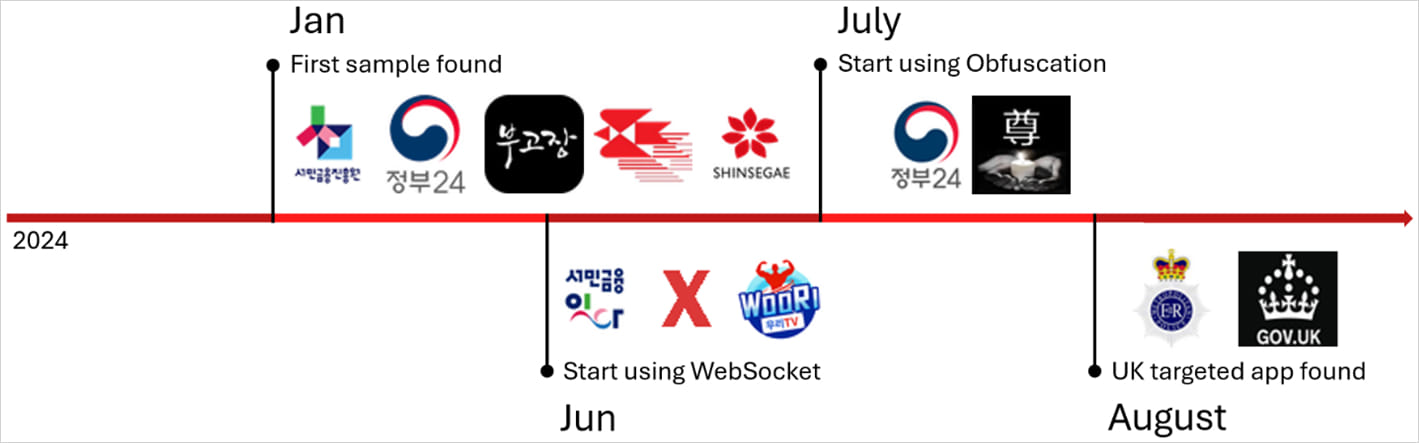
A malware operation found by McAfee was traced again to at the least 280 APKs distributed outdoors of Google Play utilizing SMS or malicious social media posts. This malware can use OCR to get better cryptocurrency restoration phrases from photos saved on an Android machine, making it a big risk.
A number of the Android functions faux to be for South Korean and UK authorities companies, courting websites, and pornography websites.
Although the exercise primarily focused South Korea, McAfee has noticed a tentative enlargement to the UK and indicators that an iOS variant is likely to be in early improvement.
Supply: McAfee
In July 2023, Development Micro revealed two Android malware households named CherryBlos and FakeTrade, unfold through Google Play, that additionally used OCR to steal cryptocurrency information from extracted photos, so this tactic seems to be gaining traction.
SpyAgent information extraction
As soon as it infects a brand new machine, SpyAgent begins sending the next delicate info to its command and management (C2) server:
- Sufferer’s contact listing, possible for distributing the malware through SMS originating from trusted contacts.
- Incoming SMS messages, together with these containing one-time passwords (OTPs).
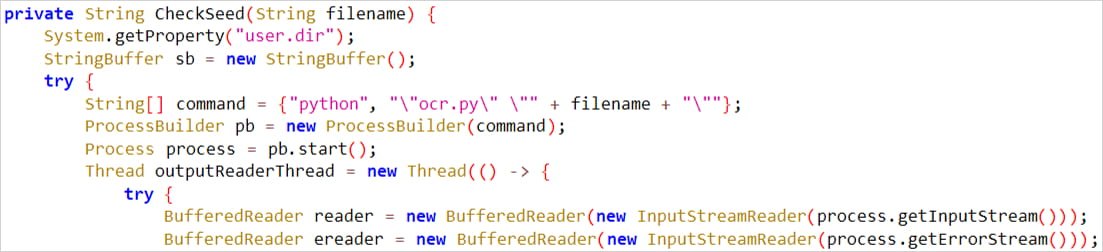
- Photos saved on the machine to make use of for OCR scanning.
- Generic machine info, possible for optimizing the assaults.
SpyAgent may also obtain instructions from the C2 to alter the sound settings or ship SMS messages, possible used to ship phishing texts to distribute the malware.
Supply: McAfee
Uncovered infrastructure
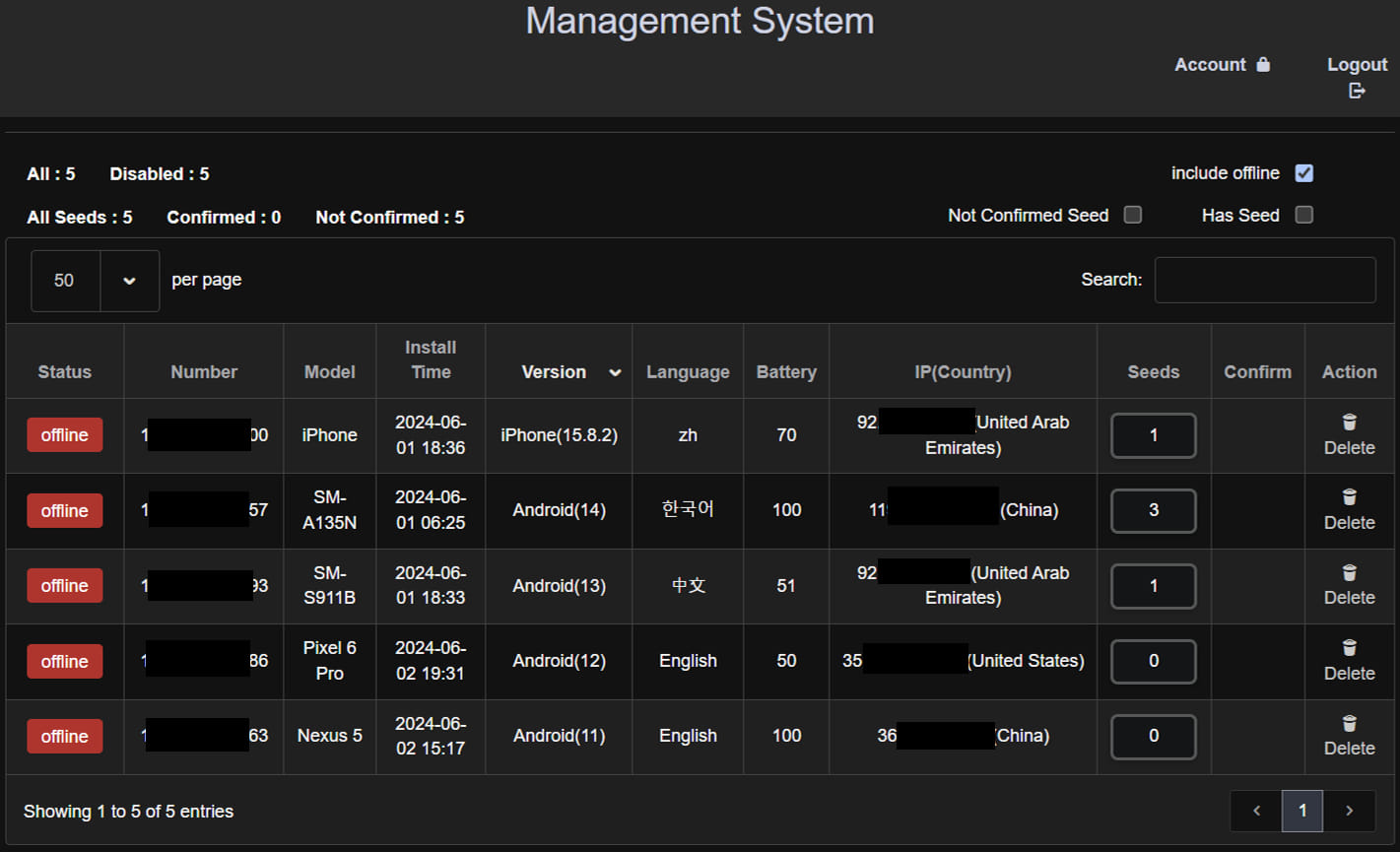
McAfee discovered that the operators of the SpyAgent marketing campaign didn’t comply with correct safety practices in configuring their servers, permitting the researchers to realize entry to them.
Admin panel pages, in addition to information and information stolen from victims, had been simply accessible, permitting McAfee to verify that the malware had claimed a number of victims.
Supply: McAfee
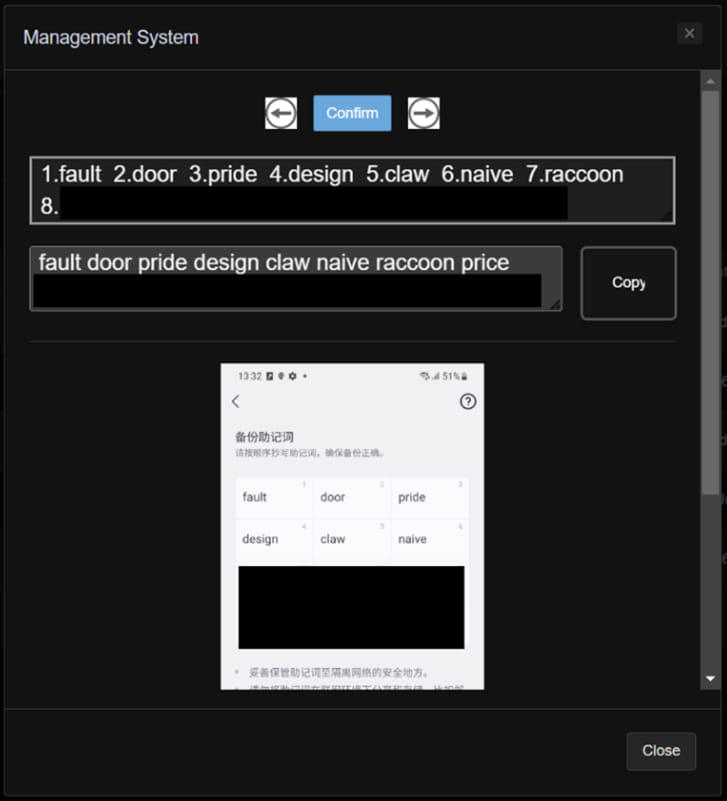
The stolen photos are processed and OCR-scanned on the server facet after which organized on the admin panel accordingly to permit simple administration and instant utilization in pockets hijack assaults.
Supply: McAfee
To mitigate this threat on Android, it will be important to not set up Android apps outdoors of Google Play, as they’re generally used to distribute malware.
Moreover, customers ought to disregard SMS messages pointing to APK obtain URLs and revoke harmful permissions that appear unrelated to the app’s core performance.
Lastly, Google Play Defend scans must be carried out periodically to test for apps which were detected as malware.
