A brand new Android banking malware named ‘SoumniBot’ is utilizing a much less widespread obfuscation strategy by exploiting weaknesses within the Android manifest extraction and parsing process.
The tactic permits SoumniBot to evade customary safety measures present in Android telephones and carry out info-stealing operations.
The malware was found and analyzed by Kaspersky researchers, who present the technical particulars on the strategies the malware makes use of to reap the benefits of the Android routine to parse and extract APK manifests.
Tricking Android’s parser
Manifest recordsdata (‘AndroidManifest.xml’) are current in every app’s root listing and include particulars about parts (providers, broadcast receivers, content material suppliers), permissions, and app knowledge.
Whereas there are Zimperium varied compression methods malicious APKs can use to idiot safety instruments and evade evaluation, Kaspersky analysts discovered that SoumniBot makes use of three completely different strategies that contain manipulation of the manifest file’s compression and measurement, to bypass parser checks.
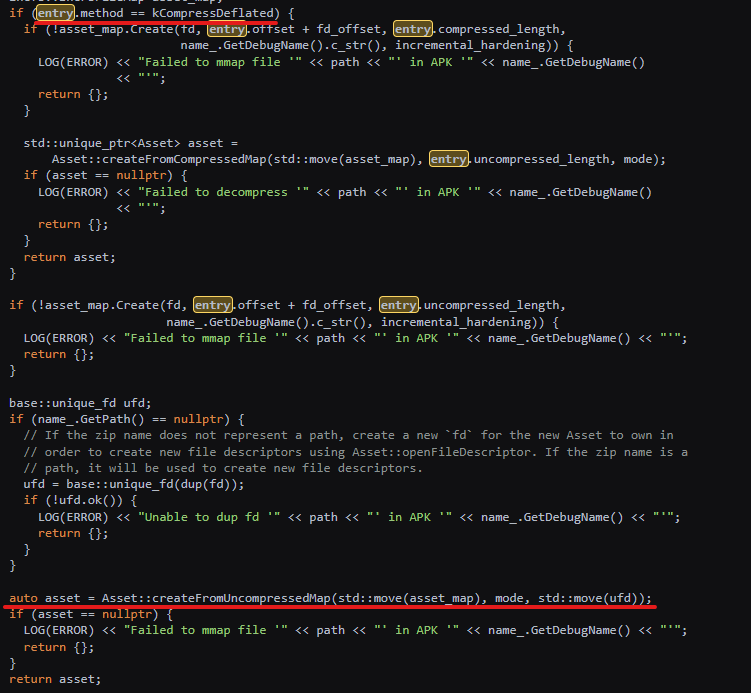
First, SoumniBot makes use of an invalid compression worth when unpacking the APK’s manifest file, which diverges from the usual values (0 or 8) anticipated by the Android ‘libziparchive’ library tasked with the position.
As an alternative of treating these values as unacceptable, the Android APK parser defaults to recognizing the information as uncompressed on account of a bug, permitting the APK to bypass safety checks and proceed execution on the system.
(Kaspersky)
The second methodology entails misreporting the scale of the manifest file within the APK, supplying a price bigger than the precise determine.
Because the file has been marked as uncompressed within the earlier step, it’s copied immediately from the archive, with junk “overlay” knowledge filling the distinction.
Kaspersky explains that whereas this additional knowledge doesn’t immediately hurt the system since Android is ready to disregard it, it performs a vital position in complicated code evaluation instruments.

(Kaspersky)
The third evasion method is to make use of very lengthy strings for the names of XML namespaces within the manifest file, making it very tough for automated evaluation instruments to examine them, which frequently lack sufficient reminiscence to course of them.

(Kaspersky)
Kaspersky has knowledgeable Google concerning the lack of ability of APK Analyzer, Android’s official evaluation utility, to deal with recordsdata utilizing the above evasion strategies.
BleepingComputer has additionally contacted Google for a remark, and we’ll replace this submit as quickly as we hear again.
The SoumniBot risk
Upon launch, SoumniBot requests its configuration parameters from a hardcoded server handle and sends profiling info for the contaminated system, together with quantity, provider, and so forth.
Subsequent, it initiates a malicious service that restarts each 16 minutes if stopped, and transmits stolen knowledge from the sufferer each 15 seconds.
The exfiltrated particulars embrace IP addresses, contact lists, account particulars, SMS messages, images, movies, and on-line banking digital certificates.
The info exfiltration is managed by instructions the malware receives by way of an MQTT server. These instructions additionally order capabilities corresponding to:
- Deleting current or including new contacts
- Sending an SMS message (forwarding)
- Setting ringtone quantity ranges
- Turning silent mode on or off
- Turning the debug mode on the system on or off
It’s unclear how SoumniBot reaches gadgets however strategies might range from distribution over third-party Android shops and unsafe web sites to updating with malicious code respectable apps in trusted repositories.
SoumniBot targets Korean customers and like many malicious Android apps, it hides its icon after set up to make it tougher to take away it. Nonetheless, it stays energetic within the background, importing knowledge from the sufferer.
Kaspersky offers a brief set of indicators of compromise, which incorporates hashes for the malware and two domains that malware operators use for command and management exercise.
