Organisations which have backed up their delicate information could imagine they’re comparatively secure from ransomware assaults; nevertheless, this isn’t the case based mostly on findings from a brand new research from IT safety firm Sophos. The report confirmed that cybercriminals tried to compromise the backups of 94% of firms hit by ransomware previously yr.
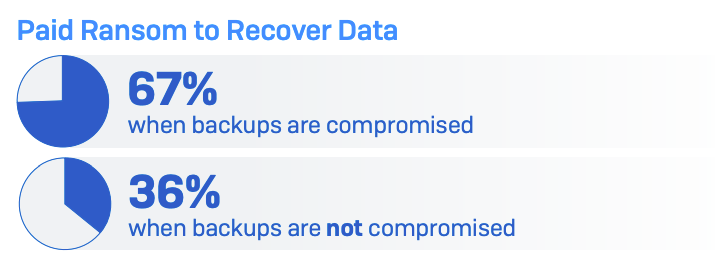
Attackers are conscious that those that fall sufferer to ransomware should select to both pay the ransom or get better their now-encrypted programs from a backup. To place extra strain on decision-makers to pay up, it’s turning into extra widespread for them to focus on the duplicated information in addition to the manufacturing information. Certainly, the report confirmed the sufferer is nearly twice as prone to pay up if their backup is compromised, and restoration from the assault is eight instances costlier.
The Sophos analysis revealed the extent of the recognition and effectiveness of ransomware teams concentrating on company backups (Determine A).
Determine A
SEE: What’s ransomware? Learn this TechRepublic cheat sheet
How a lot does it value to get better from a ransomware assault on the backup?
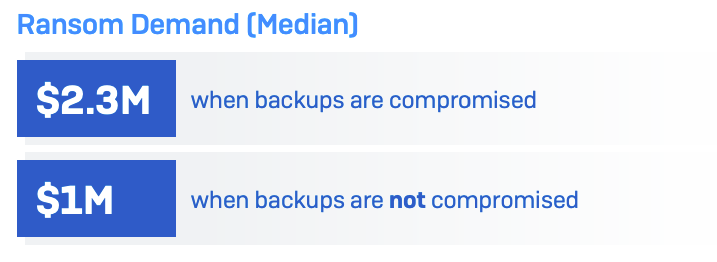
The Sophos analysis discovered that the median ransom demand for organisations whose backups are compromised is $2.3 million (£1.8 million) (Determine B). When the backup will not be compromised, the median ransom demand is $1 million (£790k), because the attacker has much less leverage.
Determine B
“Ransomware-led outages frequently have a considerable impact on day-to-day business transactions while the task of restoring IT systems is often complex and expensive,” Sally Adam, the senior director of promoting at Sophos, wrote within the report.
Firms with out compromised backups are additionally extra doubtless to have the ability to negotiate the ransom fee down, paying out a mean of 82% of the preliminary demand. These whose backups are compromised can pay 98% of the demanded sum, on common.
The full value of a ransomware assault is commonly extra than simply the ransom, because it incorporates the restoration of any impacted programs and the losses incurred by any downtime. Firms with compromised backups paid eight instances extra on the whole restoration effort than these whose backups remained untouched.
Moreover, solely 26% of firms with compromised backups had been totally recovered inside every week, in comparison with 46% of these with out compromised backups. Sophos analysts predicted that is due to the extra work needed to revive programs from decrypted backup information, and organisations with weak backups are much less prone to have a powerful restoration plan in place.
Which industries are most prone to having their backups focused throughout ransomware assaults?
State and native governments and the media, leisure and leisure sectors are probably the most prone to having their backups compromised throughout a ransomware assault; the research discovered that 99% of the organisations in these industries that had been hit by ransomware within the final 12 months had their backups focused by cybercriminals (Determine C).
Determine C
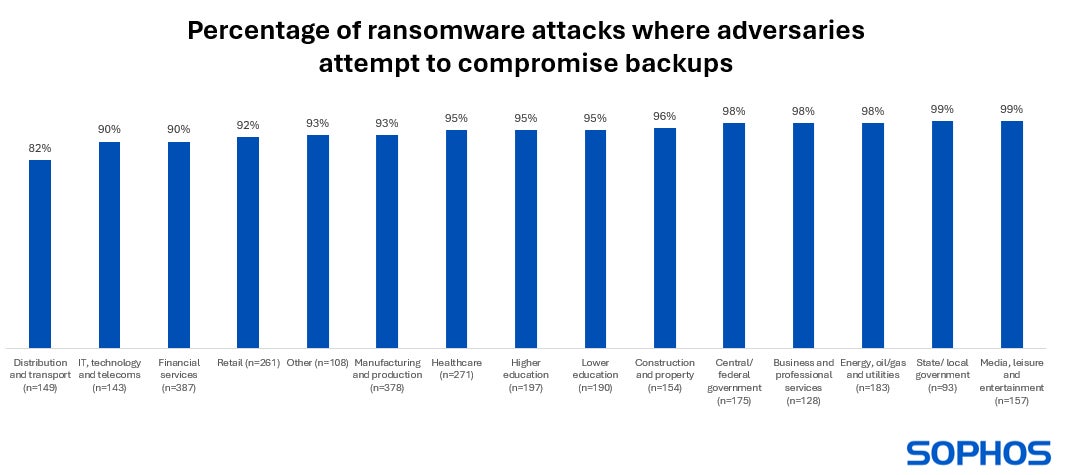
Regardless of the distribution and transport sector experiencing the bottom price of tried backup compromise throughout a ransomware assault, 82% of organisations had been nonetheless affected. A September 2023 report from the U.Okay.’s Nationwide Cyber Security Centre and Nationwide Crime Company highlighted that the logistics sector is a selected goal for ransomware as a result of it depends closely on information.
What are the success charges of backup compromise makes an attempt?
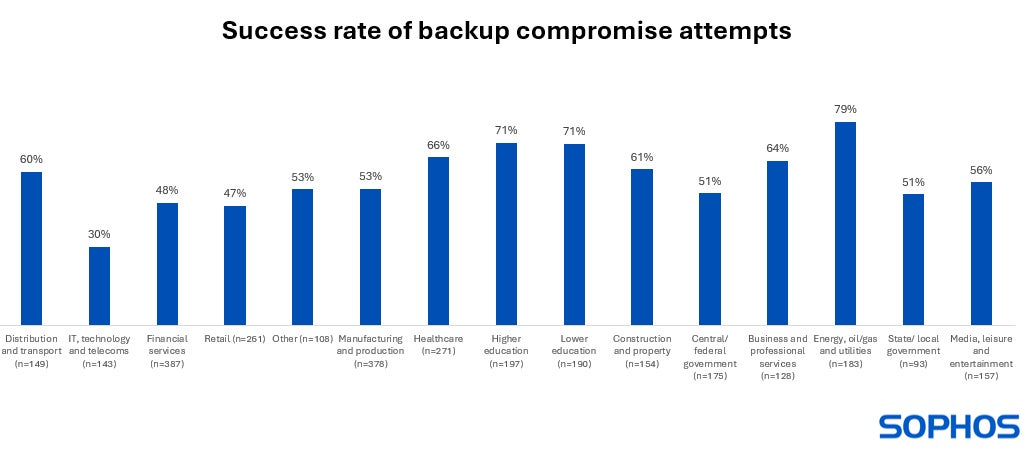
The common success price of backup compromise makes an attempt was 57%, although this diverse considerably by sector (Determine D). The power, oil/fuel and utilities sector and the training sector had been the simplest targets, with success charges of 79% and 71%, respectively.
Determine D
Sophos analysts suspected that the previous could have skilled a bigger proportion of refined cyber assaults on condition that compromising crucial nationwide infrastructure can result in widespread disruption, making it a main goal for ransomware. The NCSC said that it’s “highly likely” the cyber menace to the U.Okay.’s CNI elevated in 2023, partially because of its reliance on legacy know-how.
Schooling amenities are inclined to harbour plenty of delicate information about workers and college students, which will be invaluable to attackers, whereas having a restricted finances for preventative cyber safety measures. Their networks are sometimes accessible to numerous folks and units, and this openness makes them tougher to guard. In keeping with the U.Okay. authorities, 85% of universities within the nation recognized safety breaches or assaults in 2023.
The bottom price of profitable backup compromise was reported by the IT, know-how and telecoms sector, with a 30% success price. Sophos said that that is doubtless a results of stronger backup safety by advantage of its experience and assets.
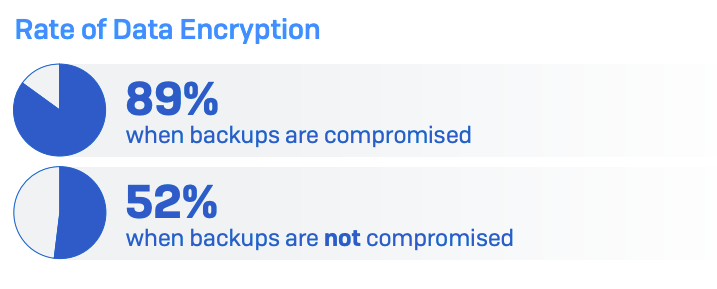
As well as, the Sophos report discovered that organisations whose backups had been compromised throughout the ransomware assault had been 63% extra prone to have their information encrypted by the cyber criminals (Determine E). Sophos analysts speculated that having weak backups is indicative of a weaker total safety posture, so organisations that do have them compromised usually tend to fall sufferer at different levels of the ransomware assault.
Determine E
The rising menace of ransomware
Ransomware is a rising menace all around the world, with the variety of enterprises attacked rising by 27% final yr and payouts exceeding $1 billion (£790 million). In January 2024, the U.Okay.’s Nationwide Cyber Security Centre warned that this menace was anticipated to rise even additional because of the new availability of AI applied sciences, lowering the barrier to entry.
Ransomware-as-a-service can also be turning into extra widespread, because it permits novice cyber criminals to utilize malware developed by one other group. The results of ransomware assaults can transcend monetary, impacting the psychological and bodily well being of workers.
How companies can defend their backups towards ransomware assaults
The fact is that nearly all of U.Okay. companies are weak to cyberattacks. Nonetheless, there are measures that may be taken to guard manufacturing and backup information from ransomware, particularly because the latter usually doesn’t profit from the identical stage of safety as the previous.
3-2-1 technique and offline backups
“The 3-2-1 strategy involves keeping three copies of (production) data on two different media types, with one copy stored offsite,” defined Shawn Loveland, the chief working officer at cyber safety firm Resecurity, in an electronic mail to TechRepublic. Offsite storage may very well be via cloud providers or on a tape or disc.
It’s also vital to contemplate an offline backup, in response to Sam Kirkman, the EMEA director at IT safety providers agency NetSPI. He instructed TechRepublic in an electronic mail: “Though these are more difficult to handle and combine inside enterprise operations, offline backups are impervious to hacking since they’re disconnected from dwell programs. This makes offline backups — when carried out appropriately — the only strongest defence towards ransomware assaults.
“The NCSC recommends specific practices for effective offline backups, such as limiting connections to live systems to only essential periods and ensuring that not all backups are online simultaneously. However, it’s also critical to validate each offline backup before reconnecting it for data updates to prevent potential corruption by attackers.”
Immutable storage and snapshots
Immutable storage refers to a knowledge storage technique the place, as soon as information is written, it can’t be altered or deleted, defending it towards tampering or ransomware. “Ideally, each backup should be immutable to prevent modification and simply expire when it is no longer relevant,” mentioned Kirkman.
Immutable snapshots — a read-only copy of information taken at a selected cut-off date — will be taken from immutable storage. Don Foster, the chief buyer officer at cloud information administration platform supplier Panzura, instructed TechRepublic in an electronic mail: “With the flexibility to revive a pristine information set within the occasion of a ransomware assault, you may make a full restoration to a selected cut-off date with out shedding information.
“Reverting to a previous snapshot takes a fraction of the time to restore from a backup, and it allows you to get precise about which files and folders to revert. The average time it takes for organisations to recover from a ransomware attack and get back to business as usual is 21 days, but it can often take much longer.”
Common backup testing
“Regular (backup) testing ensures functional and complete backups and various types of restores,” Loveland instructed TechRepublic.
Practising restoration from backups may also make the method simpler whether it is ever needed to take action after a ransomware incident. Kirkman added: “Backup testing is crucial to make sure effectiveness in restoring programs post-attack. Testing each backup confirms its functionality to facilitate restoration from a ransomware incident.
“However, it is imperative to conduct these tests securely, ensuring that backup environments remain protected from direct attack during recovery attempts. Otherwise, your initial attempts to recover from an attack may enable an attacker to render further recovery impossible.”
Entry controls and backup utilization insurance policies
Loveland instructed TechRepublic: “Access controls limit access to backup data and reduce the risk of ransomware spreading to backup systems.” They embody organising person permissions and authentication mechanisms to make sure solely authorised people and programs can entry backup recordsdata.
Kirkman added: “Privileged Access Management (PAM) is vital in preventing unauthorised access to online backups, a common initial target for ransomware groups. Effective PAM involves granting time-limited and independently authorised access, where requests must be verified by another person within the organisation through a trusted communication channel. This approach significantly raises the bar for attackers attempting to breach backup environments.”
SEE: 6 Greatest Open Supply IAM Instruments in 2024
However it isn’t sufficient to simply have entry controls in place, because the credentials that unlock them may nonetheless simply fall into the incorrect arms. Foster mentioned: “Closely guard the keys to backend storage — especially when that sits in the cloud. While attacks on file systems and backup files are common, ransomware attacks can include accessing cloud storage using stolen admin credentials.”
Strong insurance policies governing backup utilization are additionally important to making sure the entry controls’ power towards ransomware attackers. Kirkman mentioned: “A good backup implementation cannot be achieved with technology alone. The practices surrounding backup usage influence both their effectiveness and security, and should be given as much, if not greater, attention than the technology itself.”
Backup encryption and real-time monitoring
Superior encryption of the backup information and guaranteeing the backup software program is up-to-date and patched are probably the most basic steps companies can take to guard it from attackers. Monitoring for suspicious actions which may point out a compromise try was additionally highlighted by the specialists TechRepublic spoke to.
Foster instructed TechRepublic: “Deploy a product with near real-time ransomware detection to minimise data impact and speed up recovery by identifying the earliest signs of suspicious file activity, which often takes place well before the main attack.”
Examine methodology
Sophos commissioned the impartial analysis company Vanson Bourne to survey 2,974 IT/cyber safety professionals whose organisations had been hit by ransomware within the final yr. Contributors had been surveyed in early 2024, and their responses are reflective of their experiences within the 12 months prior.