Untracked Vulnerabilities
There’s a frequent assumption that every one open supply vulnerabilities maintain a CVE. Nonetheless, others consider that the Nationwide Vulnerability Database (NVD) has the ultimate phrase when deciding what’s a vulnerability and what’s not. Nevertheless, can a vulnerability exist that isn’t tracked by a CVE, or just isn’t within the NVD?
NVD is the highest reference, that’s irrefutable. It’s why these of us on the Checkmarx SCA analysis staff use NVD as our important supply of vulnerability data. Nevertheless, we’ve additionally defined beforehand how NVD’s knowledge is commonly not sufficient. Furthermore, NVD depends on varied AppSec authorities and maintainers to keep up a complete database of vulnerabilities.
In that sense, we should pursue different sources to extend the magnitude of the vulnerability protection inside our SCA answer. To each vulnerability that isn’t current within the NVD, and therefore, doesn’t have a CVE, we name them an “Untracked Vulnerability.”
Our Challenges
Tracked or not, an exploitable vulnerability in your code can turn out to be a gateway to your utility being compromised. And just like the darkish aspect of the moon that we are able to’t see, we merely comprehend it’s there. These two assumptions are the place the true danger resides.
Nevertheless, researching untracked vulnerabilities is a course of that include some challenges that we have to sort out. Essentially the most distinguished are:
- Untracked vulnerabilities normally have much less data accessible than ones which are tracked. Which implies it requires harder analysis to cowl the vulnerability.
- The truth that they aren’t validated by a trusted authority requires extra work on our half to measure and validate the danger as effectively. Generally, we even want POCs (Proof of Idea) to show {that a} vulnerability exists.
Each challenges are all the time current, but a 3rd problem arises infrequently. It is not uncommon for Untracked Vulnerabilities to be unfixed and so they might have an effect on the newest variations of fashionable packages. So generally we should exhume vulnerabilities we’ve coated earlier than and make sure if the analysis and details about them remains to be correct.
Not too long ago, we needed to validate two of those vulnerabilities within the NPM package deal “debug.” The “debug” package deal is without doubt one of the hottest packages on NPM with a whole bunch of thousands and thousands of weekly downloads—another reason to carry out our analysis as completely as doable.
Reminiscence Leak in “debug”
Confirming the vulnerability
One of many vulnerabilities was a Reminiscence Leak, and the place to begin was this subject. It wasn’t talked about anyplace else, and there was no CVE nor any information about this on NVD. So, we knew we must analysis this subject as an Untracked Vulnerability.
The place might the problem lead us?
When the details about a problem is proscribed, we should analyze every thing from the start, and each crumb of knowledge can add as much as one thing. There are references to different points, commits, and so forth., along with feedback that may maintain important data. We should additionally search for leads on the outdated evaluation that might point out a misunderstanding or something that went unnoticed.
A vigilant journey via the feedback confirmed us how the vulnerability went from being uncovered to fastened, and alongside the best way, we gathered sufficient data to belief the validity of the vulnerability and its repair. There was proof within the feedback (together with solutions from the maintainer) and a repair commit. Nonetheless, we analyzed the code completely and ran our instruments to substantiate this.
However at this level, it wouldn’t suffice to utterly belief the problem was fastened. We must reproduce the vulnerability and eventually extinguish any doubt.
Proof of Idea (POC)
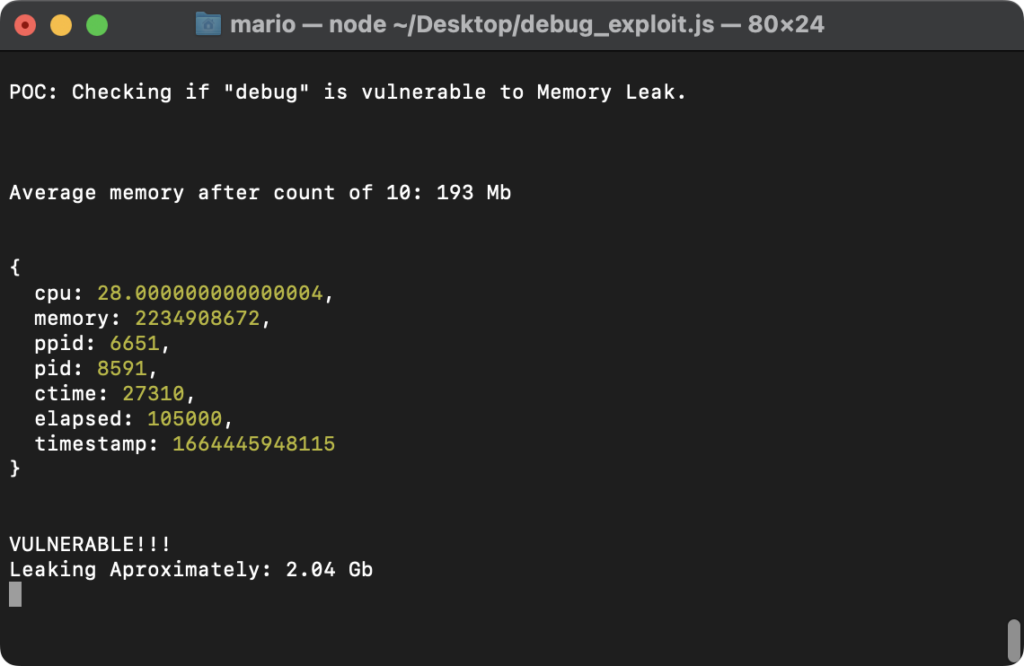
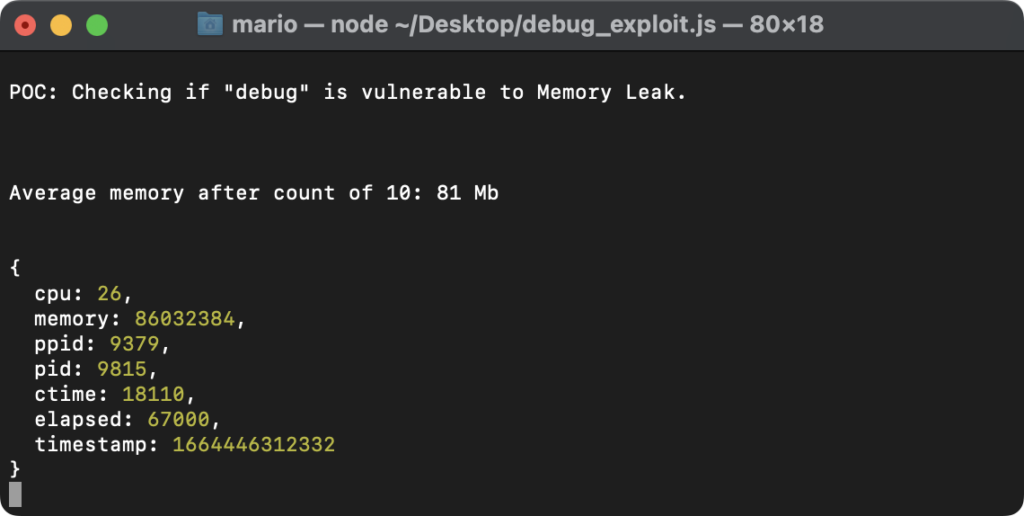
We all know {that a} reminiscence leak implies that reminiscence that’s not wanted isn’t being freed accurately. Within the cybersecurity jargon, it implies that the reminiscence will carry on accumulating till one thing crashes, thus, if intentional, resulting in a Denial of Service (DoS).
That was exactly the state of affairs right here, and all it required was to instantiate “debug” in a loop.
That’s what we did utilizing a public POC. One take a look at the CPU utilization and the image was clear. We might see the reminiscence rising, little by little, and it was even clearer after operating extra situations of the POC. However we would have liked to make it higher to showcase, so we made our personal POC. Every thing went the identical, besides that we made it simpler to visualise the vulnerability and its outcomes.
The one factor that was left was to substantiate our earlier conclusions relating to the variations. So, we ran the POC for the newest susceptible model and a number of the older ones, solely to substantiate what we already knew. Finally, operating it for the primary fastened variations and the newest one confirmed that the vulnerability was certainly fastened.
ReDoS in “debug”
Confirming the vulnerability
The opposite vulnerability was a Common Expression Denial of Service, aka, ReDoS. We discovered it via this subject.
We noticed that the problem was open and there was no repair but. And from the feedback we confirmed it was certainly a vulnerability. Hum… an unfixed vulnerability? The individual reporting the problem had neatly described the issue and affected code, and the maintainer agreed that it needs to be dealt with. Nevertheless, it was deliberate to be fastened in a later model.
Nonetheless, we needed to reproduce it and create proof that the vulnerability exists.
Proof of Idea (POC)
To start with, the POC was additionally simple as a result of we already had information concerning the affected parts. We wanted to name the `allow()` operate and provides it the regex. Nevertheless, there was a problem.
To summarize, a ReDoS occurs when an utility accepts common expressions as enter, however it doesn’t validate catastrophic exponential-time common expressions. Thus, we needed to craft a selected malicious regex that will break it and trigger the Denial of Service within the utility. So that’s what we did.
We used the regex `(a+)+`, which searches for the letter “a” and its repetition, and checks if your complete expression is repeating. If we then equipped one thing like `aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaX` as enter, we might see the appliance hanging and operating for an undetermined period of time. It’s because every “a” causes the regex operate to verify for the repetition of an extra expression, thus doubling the quantity of processing time, after which, by having one thing aside from an “a” in the long run, it causes catastrophic backtracking. Mission completed!
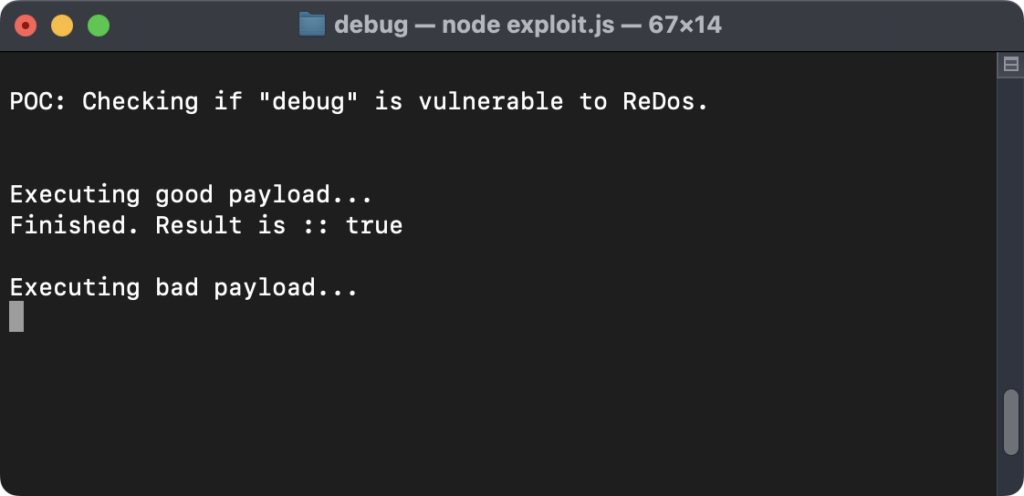
Lastly, we ran the POC for some earlier variations and for the newest launched model, to substantiate that the vulnerability was certainly not fastened – all of the variations have been susceptible and will simply be exploited.
Final phrases
As we’ve proven on this weblog, Untracked Vulnerabilities are vulnerabilities however, and so they mustn’t ever be underestimated. We are going to hold working in the direction of rising our protection of those Untracked Vulnerabilities since they’re a surplus to our prospects, and are as essential to safety, if not generally extra essential, than the tracked vulnerabilities.
The SCA analysis staff continues to cowl each tracked and untracked vulnerabilities with the identical due care. You’ll be able to be taught extra about Checkmarx SCA right here.