Schneider Electrical has confirmed a developer platform was breached after a risk actor claimed to steal 40GB of knowledge from the corporate’s JIRA server.
“Schneider Electric is investigating a cybersecurity incident involving unauthorized access to one of our internal project execution tracking platforms which is hosted within an isolated environment,” Schneider Electrical instructed BleepingComputer.
“Our Global Incident Response team has been immediately mobilized to respond to the incident. Schneider Electric’s products and services remain unaffected.”
Schneider Electrical is a French multinational firm that manufactures power and automation merchandise starting from family electrical parts present in large field shops to enterprise-level industrial management and constructing automation merchandise.
Over the weekend, a risk actor referred to as “Grep” taunted the corporate on X, indicating that they had breached its methods.
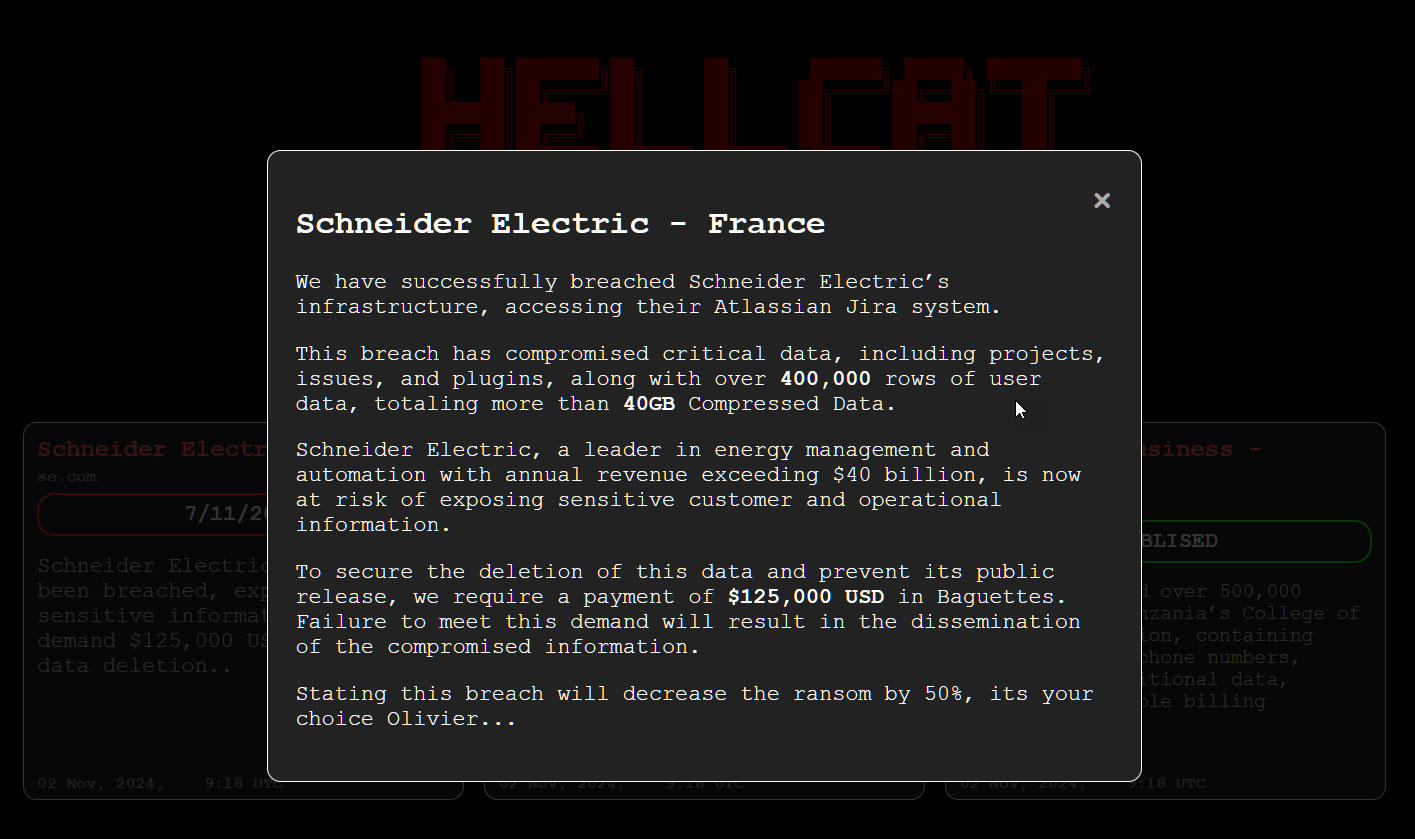
In a dialog with BleepingComputer, Grep mentioned they breached Schneider Electrical’s Jira server utilizing uncovered credentials. As soon as they gained entry, they claimed to make use of a MiniOrange REST API to scrape 400k rows of person information, which Grep says contains 75,000 distinctive e-mail addresses and full names for Schneider Electrical staff and prospects.
In a submit to a darkish web page, the risk actor jokingly calls for $125,000 in “Baguettes” to not leak the information, sharing extra particulars about what was stolen.
“This breach has compromised critical data, including projects, issues, and plugins, along with over 400,000 rows of user data, totally more than 40GB Compressed Data,” reads the risk actor’s submit.
Supply: BleepingComputer
Grep instructed BleepingComputer they just lately fashioned a brand new hacking group, Worldwide Contract Company (ICA), named after Hitman: Codename 47 recreation. The risk actor says this group doesn’t extort the businesses they breach.
As an alternative, if an organization doesn’t acknowledge they had been breached inside 48 hours, they’ll leak any stolen information.
Now that Schneider Electrical has confirmed the breach, we should see if the risk actor will proceed to leak or promote the stolen information.
Earlier this yr, Schneider Electrical’s “Sustainability Business” division was breached in a Cactus ransomware assault, the place the risk actors claimed to have stolen terabytes of knowledge.
