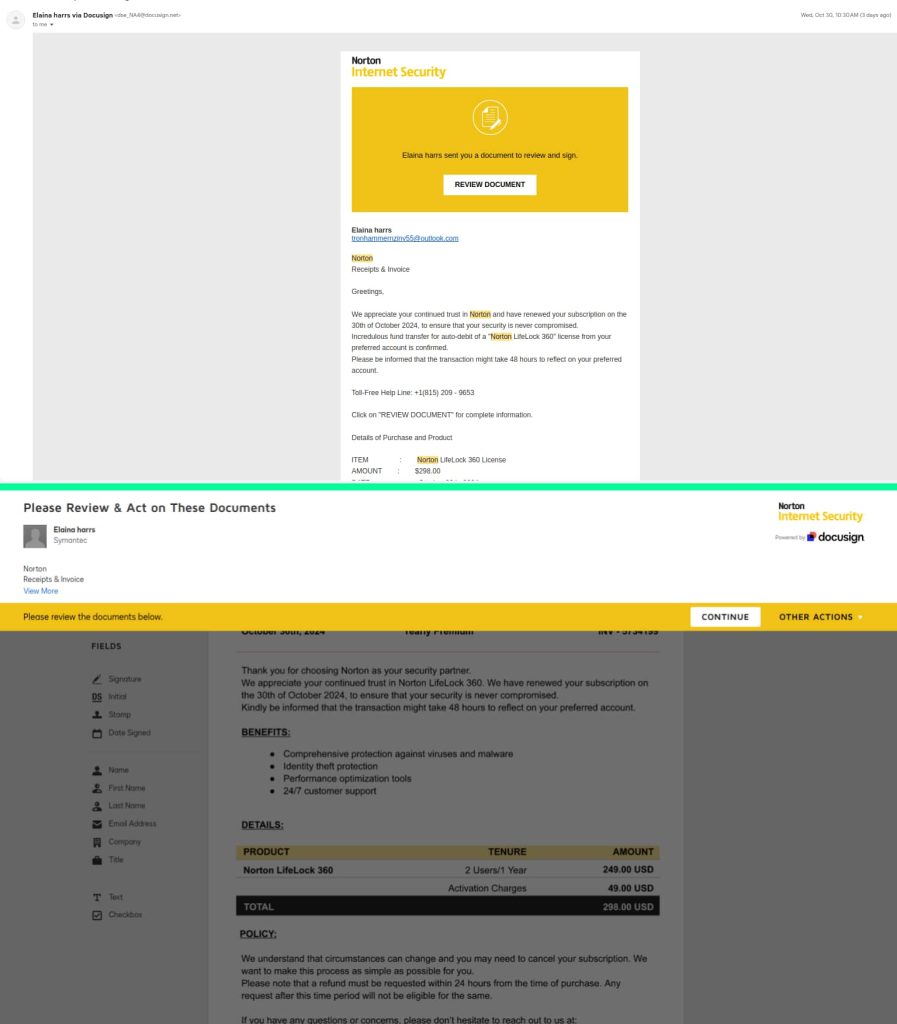
Scammers are exploiting DocuSign’s APIs to ship reasonable pretend invoices, primarily concentrating on safety software program like Norton. This phishing approach bypasses conventional e-mail spam filters by originating from legit DocuSign accounts and templates, making detection difficult.
Cybersecurity researchers at automated API safety options supplier, Wallarm, have revealed a brand new menace exploiting DocuSign APIs to ship phishing invoices. The corporate experiences that cybercriminals are using a brand new phishing approach that leverages the legitimacy of DocuSign’s platform. By exploiting DocuSign’s APIs, attackers ship extremely authentic-looking pretend invoices that evade conventional e-mail filters.
This intelligent method will increase the danger for organizations and unsuspecting customers, because it capitalizes on the belief related to respected platforms, making detection fairly difficult.
In its newest weblog submit shared completely with Hackread.com forward of its publishing on Monday, the modus operandi of those assaults entails the creation of paid DocuSign accounts. These accounts grant attackers the flexibility to change templates and make the most of APIs for automated doc era and distribution.
By customizing official DocuSign templates to imitate well-known manufacturers, akin to cybersecurity large Norton, cybercriminals can create convincing invoices which are troublesome to tell apart from legit communications. The automation capabilities supplied by DocuSign’s APIs allow attackers to effectively distribute these fraudulent invoices at scale, maximizing their potential impression. It occurs as a result of DocuSign’s API-friendly setting permits attackers to customise invoices to match firm branding.
“These fake invoices may contain accurate pricing for the products to make them appear authentic, along with additional charges, like a $50 activation fee. Other scenarios include direct wire instructions or purchase orders,” the weblog submit learn.
The results of those assaults are main. Victims might e-sign fraudulent invoices, authorizing unauthorized funds. Moreover, the legitimacy of DocuSign’s platform permits phishing emails to bypass conventional spam filters, growing the prospect of profitable supply.
Mitigating and Safety
To mitigate the dangers related to these assaults, organizations should undertake a multi-faceted method. Firstly, you will need to confirm the authenticity of sender credentials, together with e-mail addresses and sender accounts. Implementing strict inner approval processes for monetary transactions may also assist stop unauthorized funds.
Moreover, organizations ought to prioritize worker consciousness coaching to teach employees about this growing menace. By frequently monitoring for irregularities in invoices, akin to surprising expenses or uncommon requests, organizations can establish and reply to potential threats. Lastly, following DocuSign’s anti-phishing tips can present further safety.