The infamous Russian cyber-espionage group Turla is hacking different hackers, hijacking the Pakistani risk actor Storm-0156’s infrastructure to launch their very own covert assaults on already compromised networks.
Utilizing this tactic, Turla (aka “Secret Blizzard”) accessed networks Storm-0156 had beforehand breached, like in Afghan and Indian authorities organizations, and deployed their malware instruments.
Based on a report from Lumen’s Black Lotus Labs, which tracked this marketing campaign since January 2023 with the assistance of Microsoft’s Risk Intelligence Staff, the Turla operation has been underway since December 2022.
Turla (aka Secret Blizzard) is a Russian state-sponsored hacking group linked to Middle 16 of Russia’s Federal Safety Service (FSB), the unit accountable for the interception, decoding, and assortment of knowledge from international targets.
The risk actors have a protracted historical past of secretive cyber-espionage campaigns concentrating on governments, organizations, and analysis amenities worldwide since not less than 1996.
They’re the suspects behind cyberattacks concentrating on the U.S. Central Command, the Pentagon and NASA, a number of Jap European Ministries of International Affairs, in addition to the Finnish International Ministry.
Extra not too long ago, the 5 Eyes disrupted Turla’s “Snake” cyber espionage malware botnet, used to compromise units, steal knowledge, and conceal on breached networks.
Breaching Storm-0156 for stealthy knowledge theft
Lumen had been monitoring Storm-0156’s campaigns for years because the risk actor targeted their assaults on India and Afghanistan.
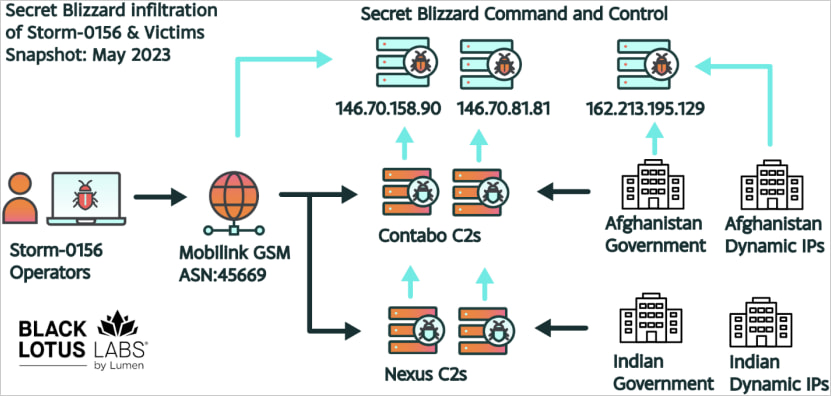
Throughout this monitoring, the researchers discovered a command and management server (C2) that displayed a “hak5 Cloud C2” banner. This C2 indicated that the risk actors had been someway capable of set up a bodily implant, like a Wi-Fi pineapple, on an Indian authorities community.
Whereas monitoring additional campaigns, Lumen found Turla inside Storm-0156’s community by observing unusual community conduct, like C2 interacting with three VPS IP addresses that had been identified to be linked to the Russian hackers.
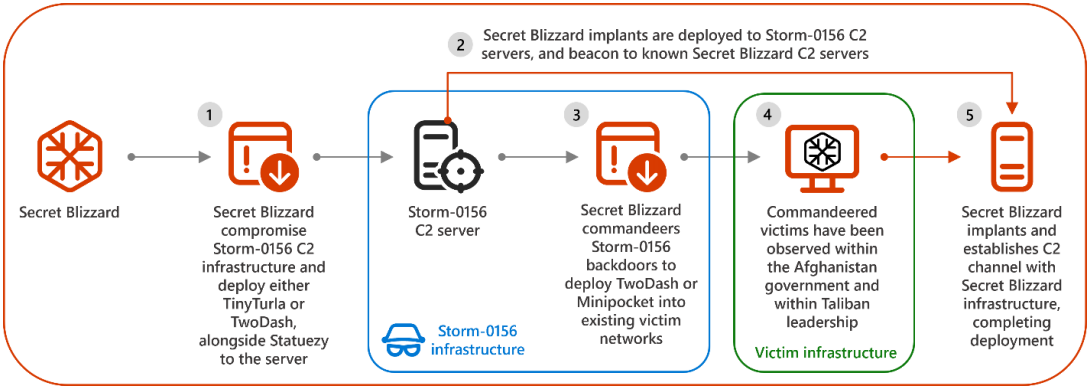
It was decided that in late 2022, Turla had breached a number of C2 nodes of the Storm-0156 risk actor and deployed their very own malware payloads, together with a TinyTurla backdoor variant, the TwoDash backdoor, the Statuezy clipboard monitor, and the MiniPocket downloader.
Aside from the malware households related to Turla, Lumen additionally famous beaconing patterns and knowledge transfers that didn’t align with the Pakistani risk actor’s earlier ways.
Supply: Microsoft
Microsoft says this entry was primarily used to deploy backdoors on Afghan authorities entities, together with the Ministry of International Affairs, the Common Directorate of Intelligence (GDI), and international consulates of the federal government of Afghanistan.
Turla did not cease at Storm-0156’s command and management servers and their already compromised targets however took it a step additional by concentrating on the Pakistani risk actors themselves.
By mid-2023, the Russian risk actors had moved laterally into Storm-0156’s personal workstations, getting access to worthwhile knowledge equivalent to malware instruments and stolen credentials and knowledge. The malware instruments embrace Storm-0156’s CrimsonRAT malware and a Go-based distant entry trojan named Wainscot.
Lumen feedback that that is significantly simple to carry out in risk actor environments as nation-state teams can not defend themselves utilizing state-of-the-art safety instruments.
“We believe that nation-state and cybercriminal endpoints and malware are especially vulnerable to exploitation since they are unable to use modern security stacks for monitoring access and protecting against exploitation,” explains Lumen.
“When threat actors have installed security products, it has resulted in the disclosure of their previously unknown exploits and tools.”
Microsoft experiences that Turla solely used a Storm-0156 backdoor as soon as to deploy malware on a single desktop in India. As a substitute, the risk actors deployed backdoors on Storm-0156’s servers used to host knowledge stolen by the Pakistani risk actors from Indian navy and defense-related establishments.
Microsoft believes that this extra cautious method might be linked to political issues.
Supply: Lumen
Lumen advised BleepingComputer that they’re now null-routing all site visitors from the identified command and management infrastructure over the Lumen community.
Turla—the hacker of hackers
Turla’s method to exploiting different actors’ infrastructure permits them to collect intelligence stealthily with out exposing themselves or their toolset, shifting blame and complicating attribution efforts.
The Russian hackers have been identified for using this technique since 2019, once they leveraged the infrastructure and malware of the Iranian state-backed risk group “OilRig,” to launch assaults on a number of nations.
On the similar time, Turla stole knowledge from OilRig’s techniques, together with keylogger logs, listing listings, information, account credentials, and malware builders for personal instruments equivalent to Neuron.
In 2022, Mandiant reported that Turla deployed backdoors to “Andromeda” malware victims in Ukraine, after reregistering three command and management domains belonging to that operation.
A 2023 Kaspersky report gave one other instance of Turla utilizing a backdoor stolen from ‘Storm-0473’ (aka “Tomiris”) in assaults.
