SUMMARY
- RomCom Exploits Double Zero-Day: RomCom, a Russia-linked group used beforehand unknown vulnerabilities in Firefox and Home windows in a classy assault marketing campaign.
- Assault Chain: Visiting a malicious webpage triggered a Firefox flaw, after which a Home windows bug allowed the set up of RomCom’s backdoor.
- Focused Sectors: RomCom focused authorities, pharmaceutical, authorized, and different sectors in Europe and North America for espionage and cybercrime.
- Fast Patches: Mozilla and Microsoft quickly launched updates to repair the vulnerabilities, highlighting the significance of software program updates.
- Refined Menace: The assault reveals the superior capabilities of state-sponsored cyber teams and the necessity for robust cybersecurity measures.
Cyber safety researchers at ESET have uncovered a malicious marketing campaign by the Russia-linked RomCom group, which mixed two beforehand unknown (zero-day) vulnerabilities to compromise focused methods together with Home windows and Firefox.
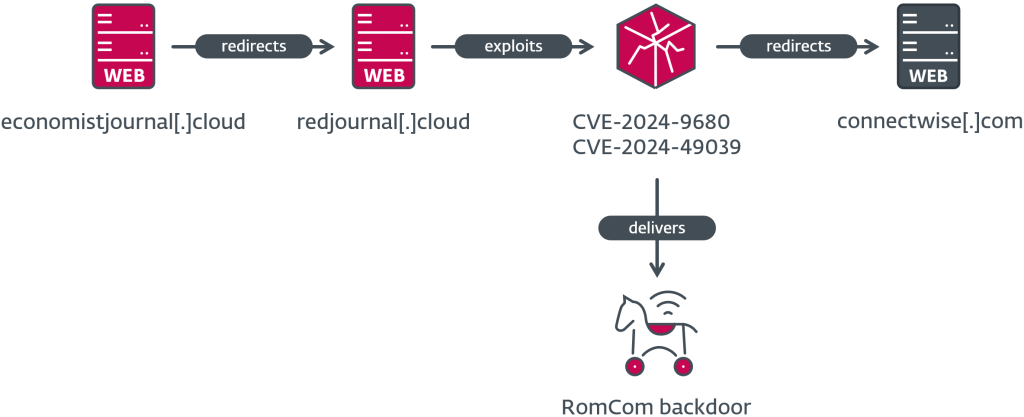
The assault chain, first detected on October eighth, began with a vulnerability in Mozilla Firefox, Thunderbird, and Tor Browser (CVE-2024-9680, CVSS rating 9.8). If a person with a weak browser visited a personalized webpage, malicious code might run inside the browser’s restricted setting with none person interplay. This vulnerability, a “use-after-free” bug within the animation function of Firefox, was rapidly addressed by Mozilla inside 24 hours of being notified by ESET.
Nevertheless, the assault didn’t cease there. RomCom chained this browser vulnerability with one other zero-day flaw in Home windows (CVE-2024-49039, CVSS rating 8.8) to bypass the browser’s safety “sandbox.” This second vulnerability allowed the attackers to run code with the privileges of the logged-in person, taking management of the system. Microsoft launched a repair for this concern on November twelfth.
The exploit chain labored by first redirecting customers to faux web sites, which used domains designed to look reliable and included the names of different organizations, earlier than sending them to a server internet hosting the exploit code.
These faux websites typically used the prefix or suffix “redir” or “red” to a reliable area, and the redirection on the finish of the assault took the victims to the reliable web site, hiding the assault. As soon as the exploit efficiently ran, it put in RomCom’s customized backdoor, giving the attackers distant entry and management over the contaminated machine.
ESET’s investigation reveals that RomCom focused varied sectors, together with authorities entities in Ukraine, the pharmaceutical trade within the US, and the authorized sector in Germany, for each espionage and cybercrime functions. The group, often known as Storm-0978, Tropical Scorpius, or UNC2596, is understood for each opportunistic assaults and focused espionage.
From October tenth to November 4th, ESET’s information confirmed that customers visiting these malicious web sites had been primarily positioned in Europe and North America, with the variety of victims starting from one to as many as 250 in some nations.
This cyberattack marketing campaign goes on to indicate the significance of fast vulnerability disclosure and patching. It additionally emphasises the necessity for customers to stay alert and maintain their software program updated to stop exploitation of zero-day vulnerabilities.
RELATED TOPICS
- Russian Cyber Offensive Shifts Focus to Ukraine’s Army
- Russian APT29 Use NSO Group-Fashion Exploits in Assaults, Google
- Russian Malware Targets Ukrainian Army Recruits through Telegram
- Russian Hackers Phish Essential Sectors with Microsoft, AWS Lures
- Russian Midnight Blizzard Breached UK Residence Workplace through Microsoft