Russian cyber-espionage group Turla, aka “Secret Blizzard,” is using different risk actors’ infrastructure to focus on Ukrainian navy units linked through Starlink.
Microsoft and Lumen not too long ago uncovered how the nation-state actor, who’s linked to Russia’s Federal Safety Service (FSB), is hijacking and utilizing malware and servers of the Pakistani risk actor Storm-0156.
Microsoft launched one other report at the moment specializing in separate Turla operations between March and April 2024, focusing on units in Ukraine utilized in navy operations.
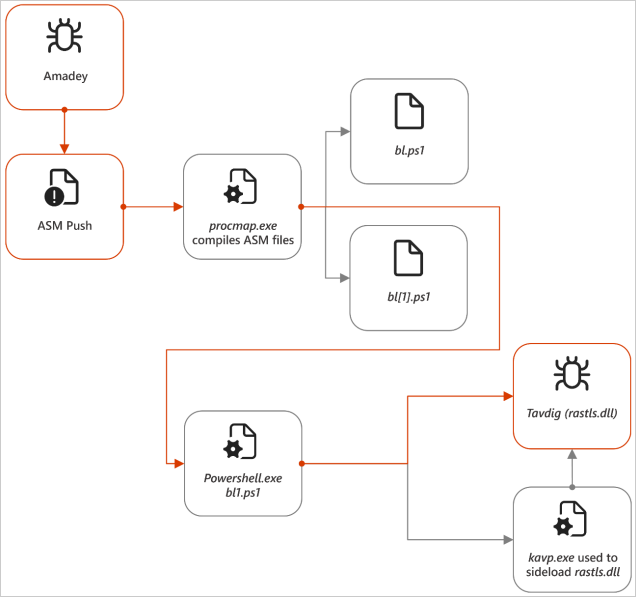
Within the newest marketing campaign, Turla utilized the infrastructure for the Amadey botnet and one other Russian hacking group often called “Storm-1837.” This infrastructure was used to deploy Turla’s customized malware households, together with Tavdig and KazuarV2, on Ukrainian techniques.
Microsoft is not sure whether or not Turla hijacked Amadey or bought entry to the botnet, however the marketing campaign constitutes one other instance of the actual risk actor hiding behind different hacker teams.
“Microsoft assesses that Secret Blizzard either used the Amadey malware as a service (MaaS) or accessed the Amadey command-and-control (C2) panels surreptitiously to download a PowerShell dropper on target devices,” explains Microsoft.
“The PowerShell dropper contained a Base64-encoded Amadey payload appended by code that invoked a request to Secret Blizzard C2 infrastructure.”
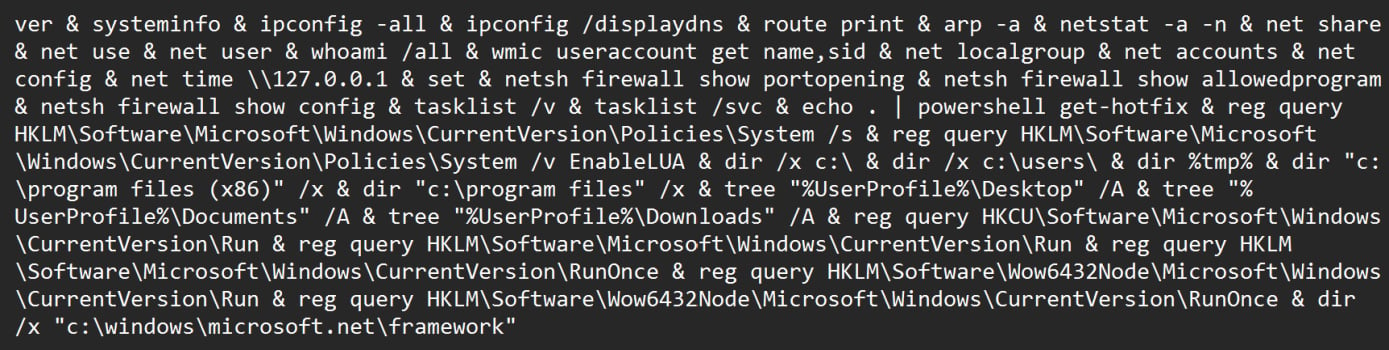
Overview of Turla assaults in Ukraine
Turla assaults in Ukraine start with phishing emails carrying malicious attachments, Storm-1837 backdoors, or the Amadey botnet, used for payload deployment on contaminated units.
Amadey is a malware botnet that has been used for preliminary entry and payload supply since 2018. At one level, it was utilized by LockBit associates as a precursor to encryptors being deployed on networks.
The versatile malware is primarily used to behave as a malware dropped, and within the case of Turla, it is used for deploying customized reconnaissance instruments on compromised units and to obtain PowerShell droppers that load the risk group’s customized malware, Tavdig (“rastls.dll”).
Supply: Microsoft
Microsoft explains that the hackers use the reconnaissance data offered by the dropped batch file to establish high-priority targets akin to navy units linked to Starlink web techniques.
“Microsoft observed Secret Blizzard downloading their custom reconnaissance or survey tool,” Microsoft defined in the report.
“This tool was selectively deployed to devices of further interest by the threat actor—for example, devices egressing from STARLINK IP addresses, a common signature of Ukrainian front-line military devices.”
Presumably, Starlink units have been focused to collect intelligence on front-line navy actions, aligning with Turla’s function on the FSB.
Microsoft’s report additionally hyperlinks Turla with one other Russian risk actor often called Storm-1837, who Redmond says has prior to now centered on units utilized by Ukrainian drone operators
In response to Microsoft, Turla was seen using Storm-1837’s Energy-Shell backdoor named ‘Cookbox,’ which Storm-1837 deployed in Ukraine in January 2024 by exploiting the WinRAR flaw CVE-2023-38831.
Turla’s customized malware households have been later deployed on these techniques, indicating that Storm-1837 was both hijacked or labored with Turla to ship their payloads.
Supply: Microsoft
Tavdig and KazuarV2 malware
Tavdig and KazuarV2 are key elements of Turla’s malware arsenal, taking part in distinct however complementary roles of their newest espionage marketing campaign.
Tavdig is a light-weight, modular backdoor designed to determine an preliminary foothold, conduct surveillance, and deploy further payloads.
It could actually accumulate info like consumer credentials, community configurations, and put in software program, and it might probably additionally carry out registry modifications and create scheduled duties for persistence.
One of many instruments Tavdig hundreds on compromised units is KazuarV2, Turla’s extra superior, stealthy backdoor, designed for long-term intelligence assortment, command execution, and information exfiltration.
KazuarV2 is usually injected into reliable system processes like ‘explorer.exe’ or ‘opera.exe,’ to evade detection after which sends and obtain information and instructions from its command and management (C2).
Microsoft notes that KazuarV2 is a modular malware, so it may be prolonged with further plugins as required, adapting to particular espionage wants.
Defenders are beneficial to examine Microsoft’s proposed mitigations and searching queries within the report, which cowl this specific Turla operation and the group’s broader actions.
