The Russian state-sponsored APT29 hacking group has been noticed utilizing the identical iOS and Android exploits created by business adware distributors in a sequence of cyberattacks between November 2023 and July 2024.
The exercise was found by Google’s Menace Evaluation Group (TAG), who stated the n-day flaws have already been patched however stay efficient on units that haven’t been up to date.
APT29, also called “Midnight Blizzard”, focused a number of web sites of the Mongolian authorities and employed “watering hole” ways.
A watering gap is a cyberattack the place a respectable web site is compromised with malicious code designed to ship payloads to guests that meet particular standards, like gadget structure or location (IP-based).
Curiously, TAG notes that APT29 used exploits that had been virtually similar to these utilized by business surveillance-ware distributors like NSO Group and Intellexa, who created and leveraged the issues as zero days when no repair was accessible.
Timeline of assaults
Google’s menace analysts be aware that APT29 has an extended historical past of exploiting zero-day and n-day vulnerabilities.
In 2021, the Russian cyber-operatives exploited CVE-2021-1879 as a zero-day, focusing on authorities officers in Japanese Europe, making an attempt to ship a cookie-stealing framework that snatched LinkedIn, Gmail, and Fb accounts.
In November 2023, APT29 compromised Mongolian authorities websites ‘mfa.gov[.]mn’ and ‘cupboard.gov[.]mn’ so as to add a malicious iframe that delivered an exploit for CVE-2023-41993.
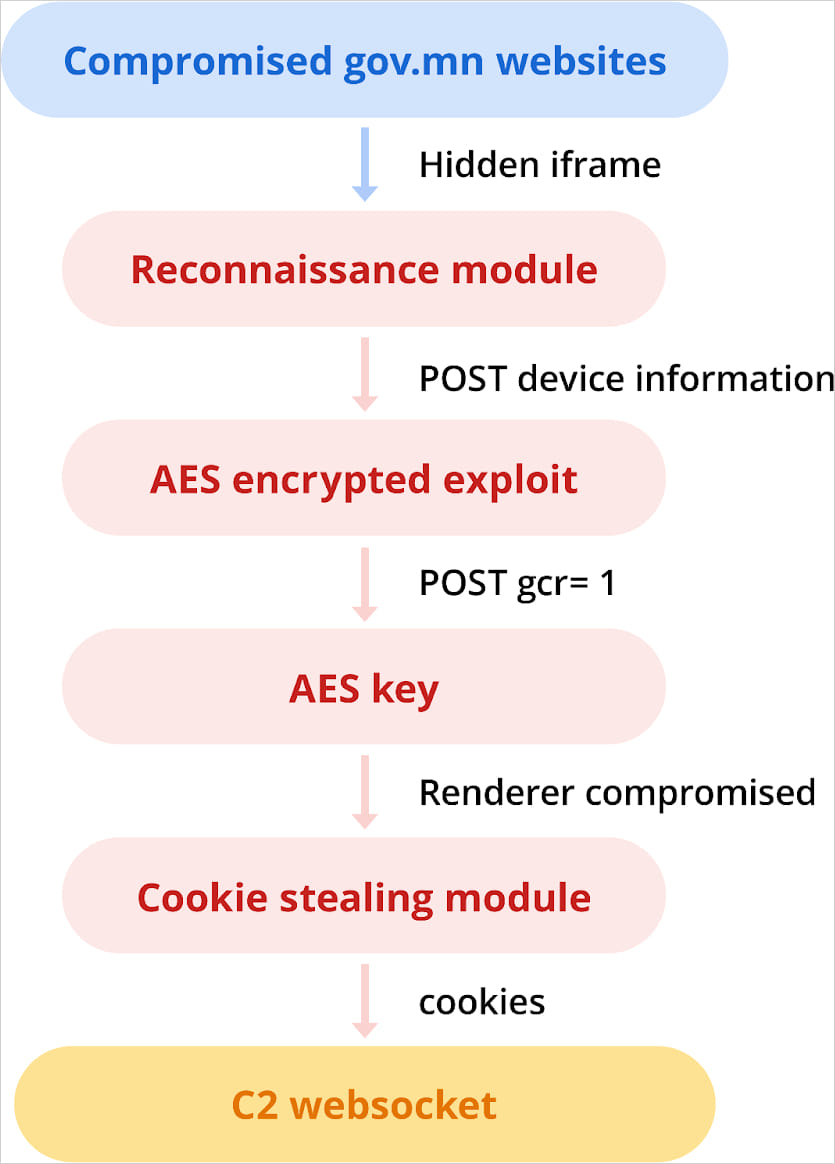
Supply: Google
That is an iOS WebKit flaw that APT29 leveraged for stealing browser cookies from iPhone customers working iOS 16.6.1 and older.
TAG studies that this exploit was precisely the identical because the one Intellexa utilized in September 2023, leveraging CVE-2023-41993 as a zero-day vulnerability on the time.
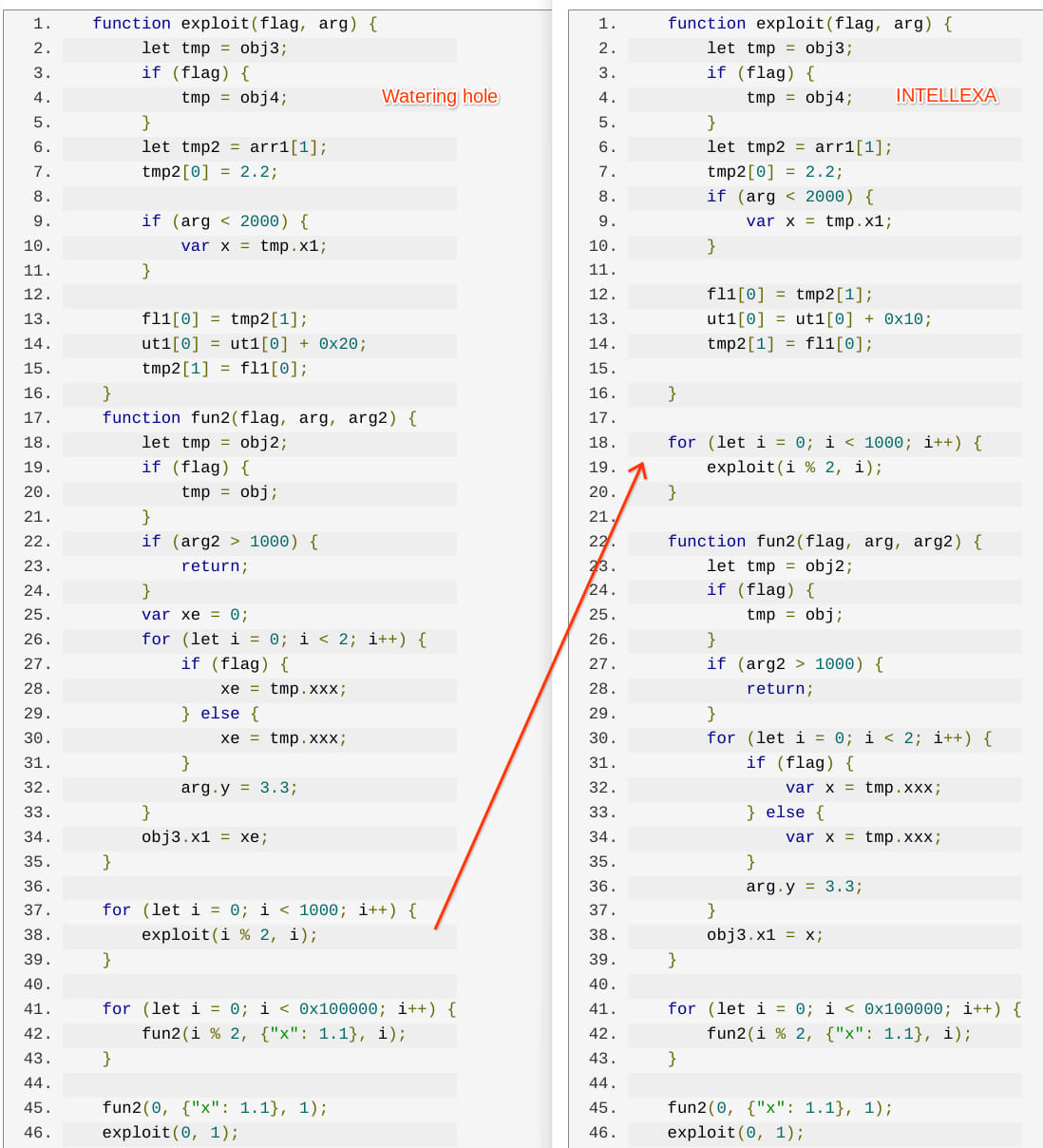
supply: Google
In February 2024, APT29 compromised one other Mongolian authorities web site, ‘mga.gov[.]mn,’ to inject a brand new iframe delivering the identical exploit.
On July 2024, APT leveraged exploits for CVE-2024-5274 and CVE-2024-4671, impacting Google Chrome, to assault Android customers visiting ‘mga.gov[.]mn’.
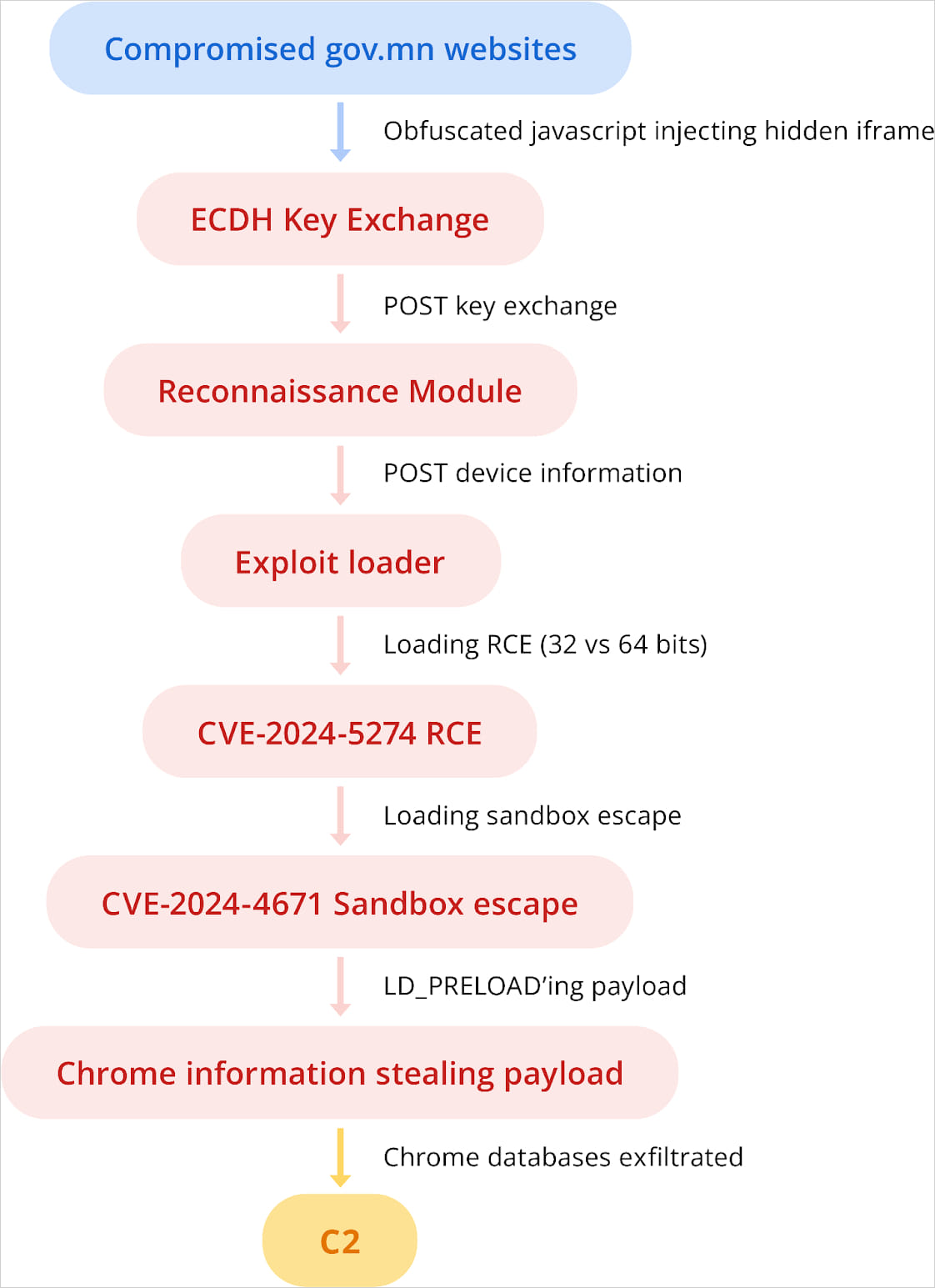
supply: Google
The aim was to steal cookies, passwords, and different delicate information saved on the victims’ Chrome browser.
The exploit used for CVE-2024-5274 is a barely modified model of that NSO Group used for zero-day exploitation in Might 2024, whereas the exploit for CVE-2024-4671 featured many similarities to Intellexa’s earlier exploits.
supply: Google
Beforehand recognized solely to adware distributors
It’s unknown how the APT29 hackers gained entry to the exploits beforehand recognized solely to NSO Group and Intellexa. Nevertheless, independently creating their very own exploits with the restricted data appears unlikely.
Attainable explanations embrace APT29 hacking adware distributors, recruiting or bribing rogue insiders working at these companies or sustaining a collaboration both straight or by way of an middleman.
One other chance is their buy from a vulnerability dealer who beforehand bought them to surveillance firms as zero-days.
Irrespective of how these exploits attain refined state-backed menace teams, the important thing subject is that they do. This makes it much more important to promptly handle zero-day vulnerabilities labeled as ‘underneath restricted scope exploitation’ in advisories—much more pressing than mainstream customers may understand.