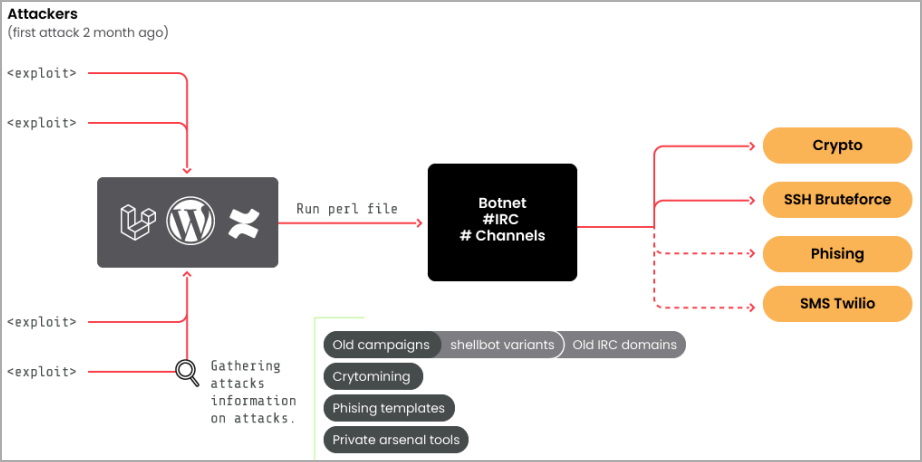
A Romanian botnet group named ‘RUBYCARP’ is leveraging recognized vulnerabilities and performing brute power assaults to breach company networks and compromise servers for monetary acquire.
In accordance with a brand new report by Sysdig, RUBYCARP at present operates a botnet managed by way of non-public IRC channels comprising over 600 compromised servers.
Sysdig has discovered 39 variants of the RUBYCARP botnet’s Perl-based payload (shellbot), with solely eight showing on VirusTotal, illustrating low detection charges for the exercise.
“The Sysdig Threat Research Team (Sysdig TRT) recently discovered a long-running botnet operated by a Romanian threat actor group, which we are calling RUBYCARP,” explains the researchers.
“Evidence suggests that this threat actor has been active for at least 10 years.”
The researchers have famous some associations with the Outlaw APT risk group, although the hyperlink is free and based mostly on widespread ways used throughout botnets.
RUBYCARP assaults
Sysdig stories that it has been detecting RUBYCARP’s probes to its honeypots for a number of months, focusing on Laravel functions by way of CVE-2021-3129, a distant code execution vulnerability.
Extra not too long ago, the analysts noticed RUBYCARP performing brute-forcing SSH servers and focusing on WordPress websites utilizing credential dumps.
Supply: Sysdig
As soon as the shellbot payload is put in on a compromised server, it connects to the IRC-based command and management (C2) server and turns into a part of the botnet.
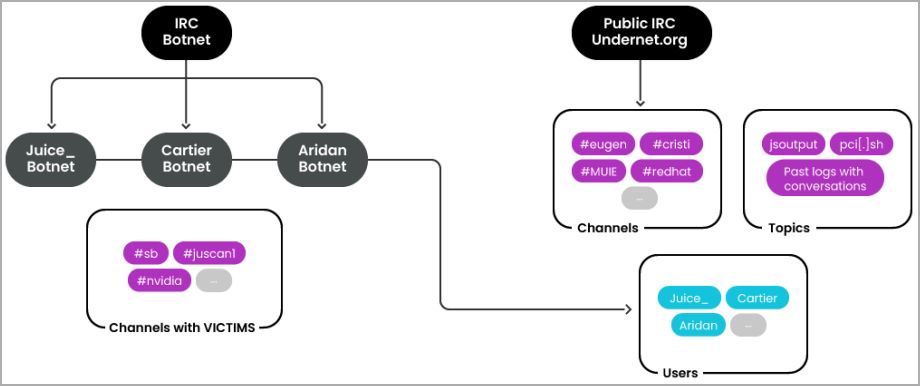
The researchers have found three distinct botnet clusters, particularly ‘Juice,’ ‘Cartier,’ and ‘Aridan,’ that are probably used for various functions.
If the consumer fails to configure its connection correctly, it will get kicked out, and its IP is blocked in an effort to safeguard the infrastructure from safety analysts making an attempt unauthorized probes.
Sysdig additionally notes that the attackers rotate their infrastructure often to evade detection and blocks, with a listing of the mapped infrastructure discovered on this GitHub web page
Supply: Sysdig
Hacked servers abused in assaults
Newly contaminated units can be utilized to launch distributed denial of service (DDoS) assaults, phishing and monetary fraud, and to mine cryptocurrency.
RUBYCARP makes use of the NanoMiner, XMrig, and a customized miner named C2Bash to mine cryptocurrencies like Monero, Ethereum, and Ravencoin, utilizing the sufferer’s computational sources.
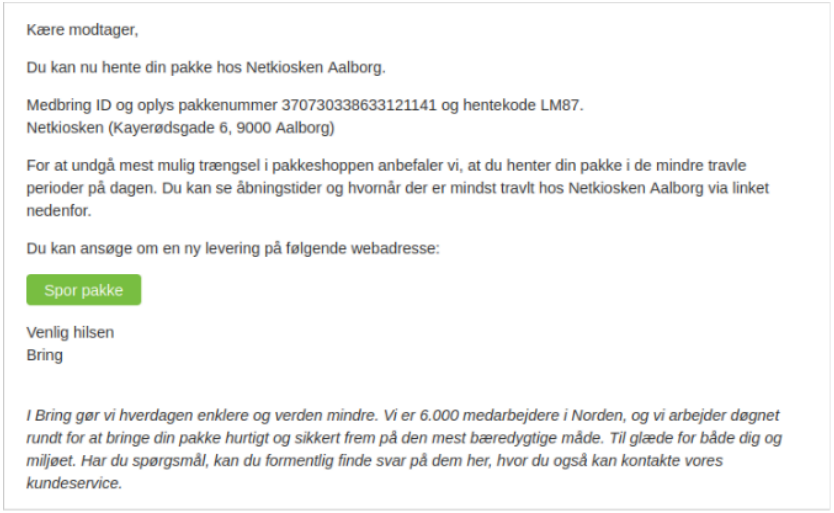
The risk group additionally makes use of phishing to steal monetary info equivalent to bank card numbers.
They obtain this by deploying phishing templates on compromised servers or sending phishing emails from them, focusing on people or organizations with misleading messages.
The phishing templates used within the newest marketing campaign point out a European focusing on scope, together with the Swiss Financial institution, Nets Financial institution, and Deliver Logistics.
Supply: Sysdig
Although RUBYCARP is just not among the many largest botnet operators on the market, the truth that they’ve managed to function largely undetected for over a decade exhibits a level of stealth and operational safety.
Along with working a botnet, SYSDIG says that also they are concerned in creating and promoting “cyber weapons,” indicating a big arsenal of instruments at their disposal.
