The digital ocean on which many people together with the world’s largest firms depend on, is crammed with hidden risks, significantly within the open-source ecosystem. One such peril that usually doesn’t get the eye it deserves is the menace posed by deserted digital property. These forgotten or ignored parts of our digital infrastructure, removed from being innocent relics of the previous, are enticing targets for cybercriminals. They remodel these property into Trojan horses, infiltrating and compromising the integrity of open-source ecosystems. This weblog delves into a number of current case research that spotlight the severity and prevalence of those threats
Key Factors
- Deserted digital property are usually not relics of the previous; they’re ticking time bombs and attackers have been more and more making the most of them, remodeling them into trojan horses inside the open-source ecosystems.
- MavenGate and CocoaPods case research spotlight how deserted domains and subdomains may very well be hijacked to mislead customers and unfold malicious intent.
- Hijacking deserted Rubygems bundle identify case research emphasizes how deserted bundle names may very well be hijacked and doubtlessly used for malicious actions.
- Hijacking deserted S3 buckets case research: The NPM bundle “bignum” is compromised by an deserted S3 bucket, illustrating how attackers can stealthily change crucial binaries with malicious ones.
- Electronic mail area hijacking case research: Particulars the favored ‘ctx’ and ‘PHPass’ packages’ compromise resulting from reclaimed expired e-mail domains.
- RepoJacking assault: Highlights a GitHub vulnerability the place attackers hijack repositories by exploiting renamed usernames.
Mavengate: Hacker’s Potential to Leverage Deserted Libraries to Hijack Java and Android Purposes
An assault vector known as MavenGate, revealed in January 2024, revealed a important flaw in the way in which Maven-based applied sciences, together with Gradle, handle dependencies.
This methodology permits attackers to hijack deserted Java and Android libraries by buying expired domains linked to those libraries.
By these hijacked deserted libraries, attackers might inject malicious code and doubtlessly compromise your entire construct means of initiatives that use these deserted libraries as dependencies. This menace prolonged to all Maven-based applied sciences, together with Gradle, impacts a broad vary of functions and companies. And because the default construct configurations of many initiatives don’t account for this risk. It leaves them open to undetected assaults.
Many Android and Java initiatives had been discovered to be affected by the described drawback together with Firms like Google, Fb, Amazon, Microsoft, Adobe, LinkedIn, Netflix, and over 200 different corporations.
Upon being notified of the problem, Sonatype, the proprietor of the mavenCentral repository, took motion to handle the issue. They blocked weak dependencies and improved safety within the Java ecosystem by implementing public key verification for uploaded artifacts. These actions will contribute to creating the Java ecosystem a safer place.
Subdomain Hijacking: The CocoaPods Incident
In a notable cybersecurity incident, CocoaPods, a broadly used dependency supervisor for iOS and Mac initiatives, confronted a subdomain hijacking assault in 2023. Within the CocoaPods incident, the attackers took management of the deserted subdomain ‘cdn2[.]cocoapods[.]org,’ which nonetheless had DNS information pointing to GitHub Pages, and used it to host malicious content material. One of these hijacking exploits forgotten settings on internet hosting platforms, with attackers utilizing the status of authentic domains to mislead customers.
The next brief demo video demonstrates this incident in motion:
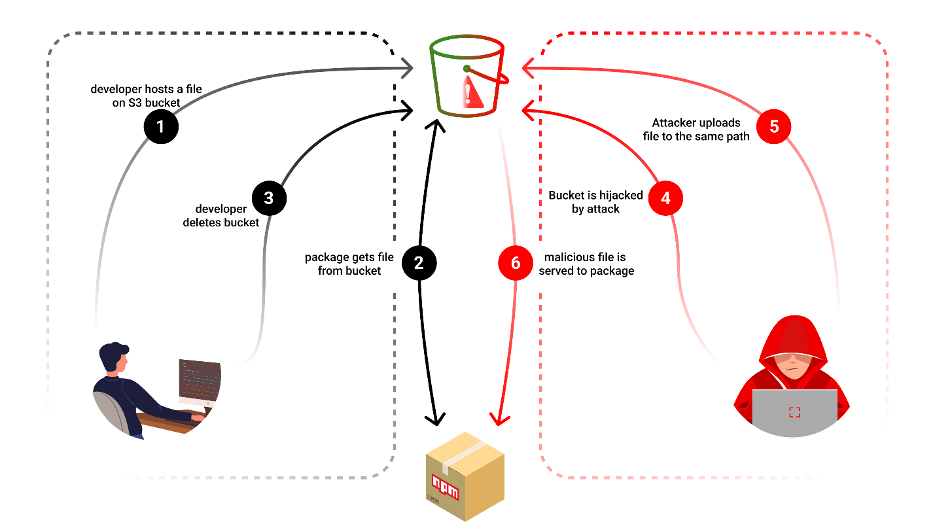
Hijacking Deserted S3 Buckets
In a current case of the NPM bundle “bignum,” in mid-2023, a major safety breach occurred by the hijacking of an S3 bucket. The attackers took management of an deserted AWS S3 bucket beforehand utilized by the npm bundle, “bignum,” for storing binaries. They then changed these binaries with malicious ones, successfully poisoning the bundle.
When customers put in or re-installed “bignum,” they unknowingly downloaded these malicious binaries, which might finally steal the person IDs, passwords, native machine surroundings variables, and native hostname after which exfiltrate the stolen knowledge to the hijacked S3 bucket.
Hijacking Deserted Electronic mail Domains: The Case of ‘cox’ and ‘PHPass’
In Might of 2022, the Python bundle ‘ctx’ and the PHP bundle ‘PHPass’ had been compromised in a complicated cyber assault, leveraging a vulnerability in repository upkeep. Attackers recognized well-liked open-source repositories managed by e-mail addresses linked to expired domains. By re-registering these domains, they gained management over the e-mail accounts, enabling them to reset passwords and assume possession of the repositories. They then injected malicious code designed to steal surroundings variables, significantly focusing on AWS credentials. This technique led to a major breach, with roughly 2,000 each day downloads of those packages for days earlier than their removing.
RepoJacking: Hijacking Retired GitHub Namespaces
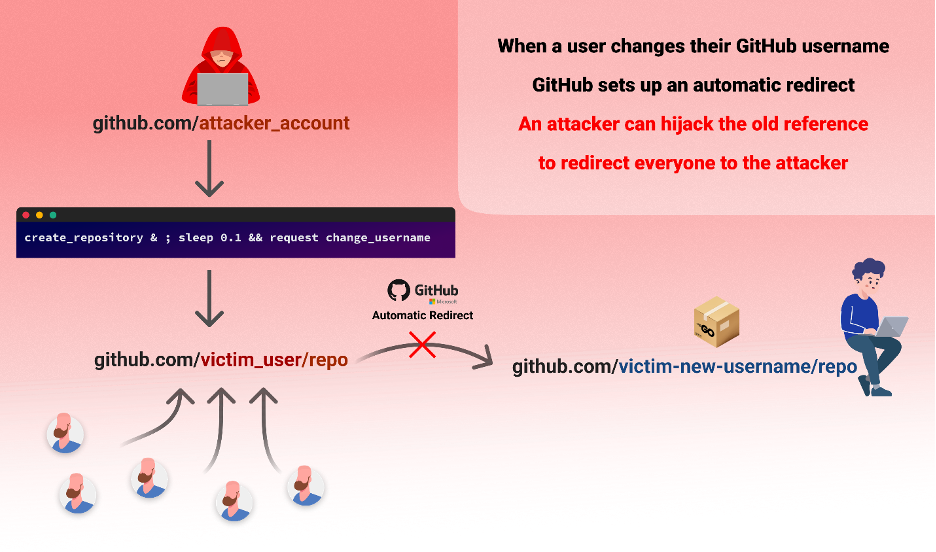
RepoJacking is a cybersecurity menace exploiting GitHub’s repository administration system. This assault targets repositories whose usernames have been modified, a typical prevalence when maintainers replace their GitHub profiles. Attackers seize this chance by claiming the outdated, well-liked usernames and creating repositories with the identical names. Customers unknowingly obtain from these hijacked repositories, considering they’re accessing trusted sources. This vulnerability permits attackers to distribute malicious code by seemingly respected repositories.
The next brief video demonstrates this case in additional element:
Hijacking Deserted Open-Supply Bundle Names: A RubyGems Bundle Takeover
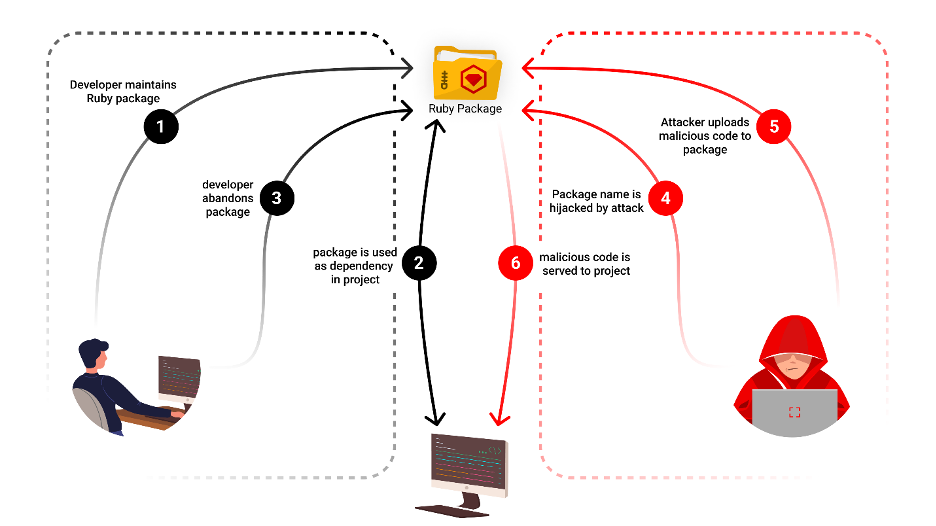
A current case within the RubyGems ecosystem highlights the danger of attackers exploiting deserted open-source bundle names to inject malicious content material into software program initiatives that rely upon them.
The ‘gemnasium-gitlab-service’ gem bundle, which was initially created and maintained by Gemnasium and later by GitLab, was ultimately deserted. An unknown entity observed this abandonment and claimed the identify of the gem. This act posed a severe menace as a result of initiatives that had been utilizing the gem, with out updating their dependencies, may unknowingly incorporate this new model, mistaking it for a authentic replace from the unique gem.
So, What Can Be Achieved About All This?
To deal with the dangers related to deserted digital property, it’s important for all stakeholders within the open-source neighborhood to take proactive steps to guard the integrity of software program provide chains.
Builders and organizations are inspired to stay vigilant and repeatedly monitor their initiatives for deserted dependencies, each direct and transitive, particularly inside open-source ecosystems.
For maintainers, training diligent area and e-mail administration in software program upkeep is essential to stop comparable assaults inside the open-source neighborhood.
Conclusion
These case research spotlight the dangers related to deserted digital property and illustrate not solely the creativity of attackers but additionally the fragility of our software program provide chains.
For builders and organizations, these incidents underscore the important want for vigilant monitoring and stringent safety practices in dependency administration.
Because the open-source ecosystem continues to develop, so does the duty to safeguard it from such insidious threats.
Deserted digital property are usually not simply dormant items of our digital previous however ticking time bombs that would detonate with far-reaching penalties. The collective effort within the cybersecurity neighborhood in direction of consciousness, proactive measures, and strong defensive methods is the important thing to mitigating these hidden risks and sustaining the integrity of the open-source ecosystem.