Menace actors are using an assault referred to as “Revival Hijack,” the place they register new PyPi initiatives utilizing the names of beforehand deleted packages to conduct provide chain assaults.
The method “could be used to hijack 22K existing PyPI packages and subsequently lead to hundreds of thousands of malicious package downloads,” the researchers say.
Hijacking fashionable initiatives
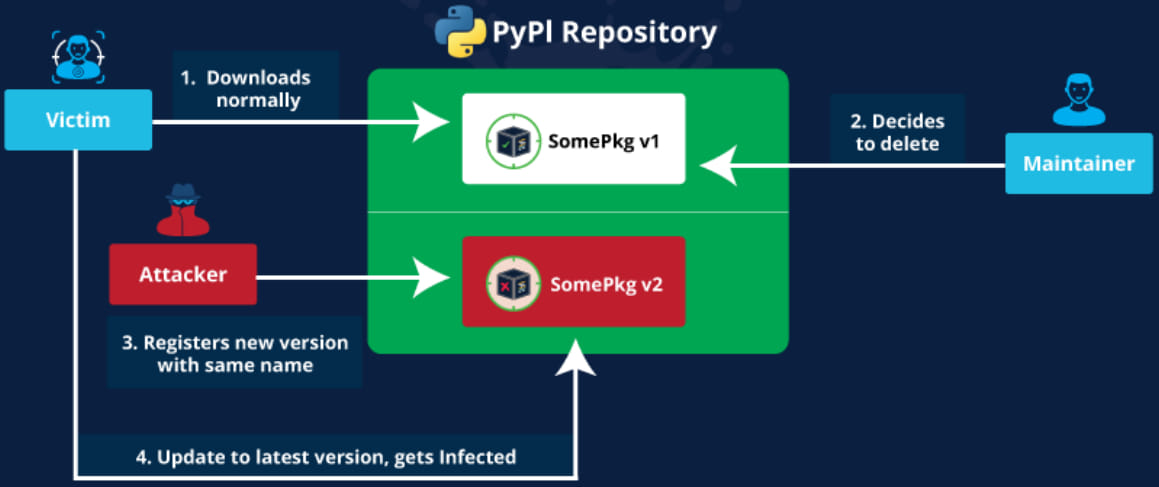
“Revival Hijack” is an assault vector that includes registering a brand new undertaking with the identify of a bundle that has been faraway from the PyPI platform. By doing so, a menace actor may push malicious code to builders pulling updates.
The assault is feasible as a result of PyPI makes instantly obtainable for registration the names of deleted Python initiatives.
Supply: JFrog
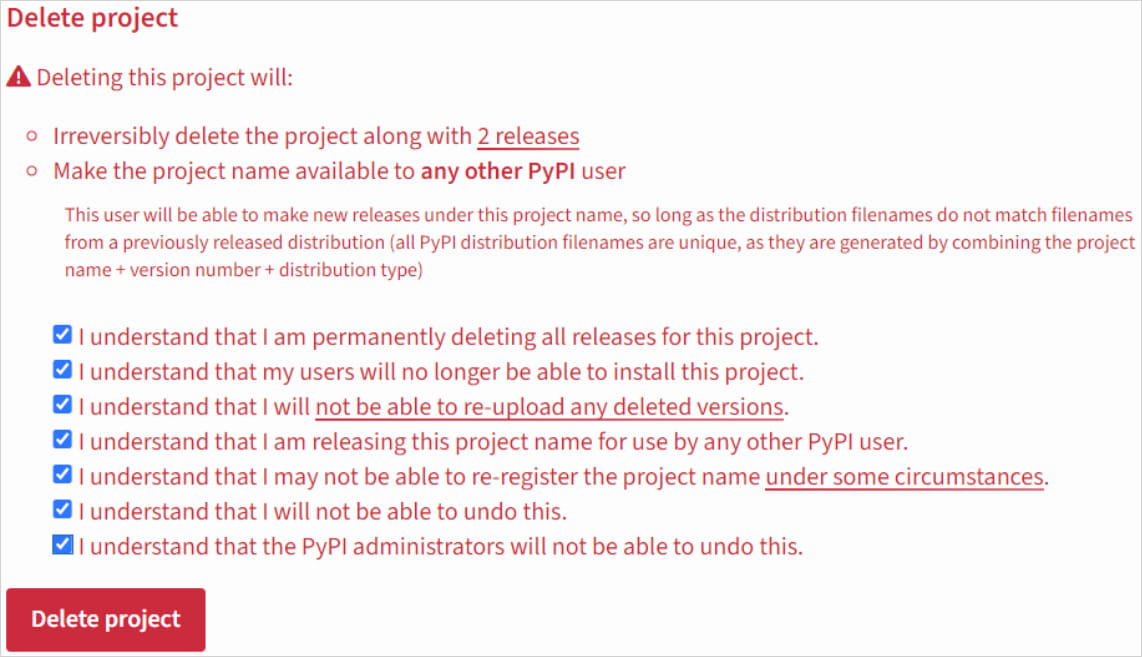
Builders who determine to delete a undertaking from PyPI solely obtain a warning in regards to the potential penalties, together with the Revival Hijack assault situation.
“Deleting this project will make the project name available to any other PyPI user,” cautions the dialog.
“This user will be able to make new releases under this project name, so long as the distribution filenames do not match filenames from a previously released distribution.”
Supply: JFrog
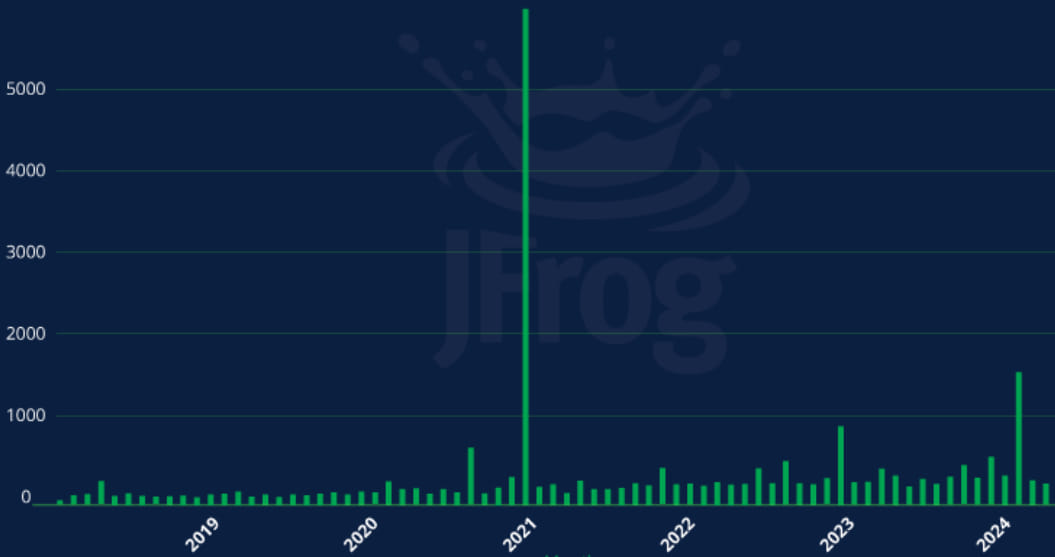
In line with researchers at JFrog, a software program provide chain platform, there are greater than 22,000 deleted packages on PyPI which are weak to the Revival Hijack assault, and a few of them fairly fashionable.
The researchers say that the month-to-month common of packages deleted on PyPI is 309, indicating a gradual stream of recent alternatives for attackers.
Supply: JFrog
JFrog says {that a} developer could determine to take away their bundle for quite a lot of causes that vary from the script not being wanted to re-writing a instrument and publishing it beneath a brand new identify.
In some instances, the bundle turns into redundant as a result of its performance is launched in official libraries or built-in APIs.
The case of “pingdomv3”
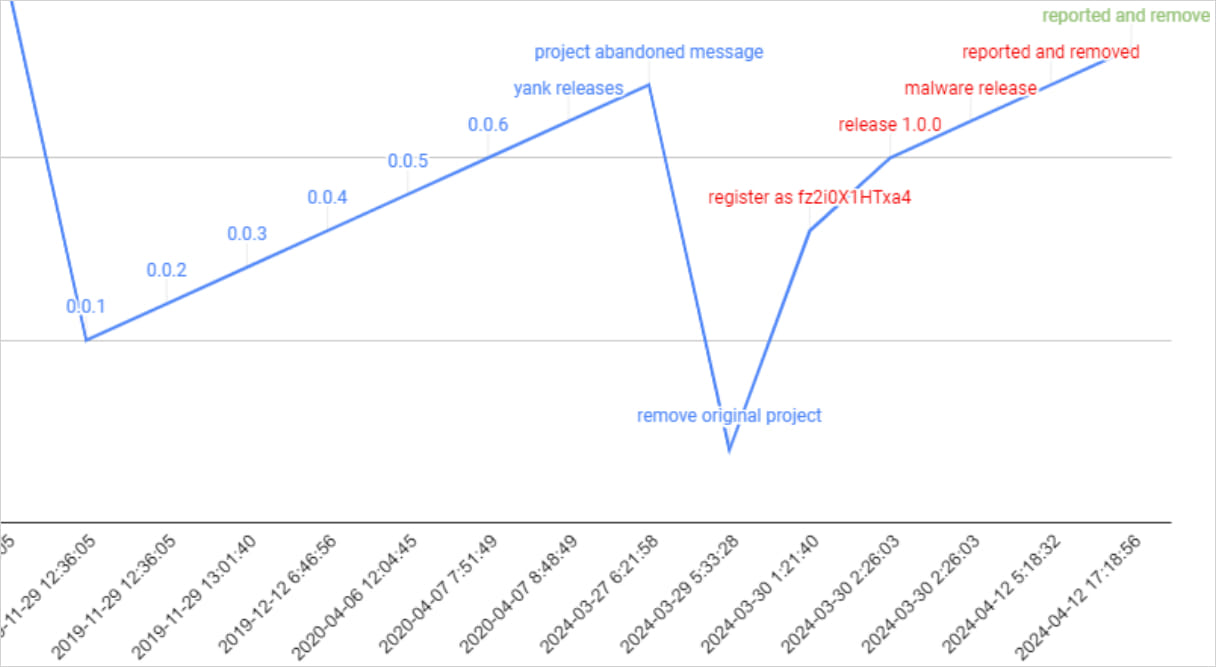
In mid-April, JFrog noticed Revival Hijack leveraged within the wild, when a menace actor focused the “pingdomv3” – an implementation of the Pingdom API web site monitoring service.
The bundle was deleted on March 30 however a brand new developer hijacked the identify and revealed an replace on the identical day, indicating that the attackers knew in regards to the situation.
In a subsequent replace, the bundle included a Python trojan that was obfuscated utilizing Base64 and focused Jenkins CI/CD environments.
Supply: JFrog
JFrog leaps to the rescue
JFrog researchers took motion to mitigate the chance of Revival Hijack assaults by creating new Python initiatives with the names of hottest already deleted packages.
JFrog explains that PyPI maintains a private blocklist that forestalls sure names from being registered on new initiatives, however most deleted packages don’t make it on that record.
This led the safety agency to take oblique motion to mitigate the “Revival Hijack” menace and registered the most well-liked of the deleted/weak packages beneath an account named security_holding.
The deserted packages are empty, and the researchers modified the model numbers to 0.0.0.1, to be sure that lively customers don’t pull an replace.
This motion basically reserves the bundle names and prevents malicious actors from hijacking them for nefarious functions.
Three months later, JFrog observed that the packages of their repository had near 200,000 downloads from automated scripts and person mistypes.
The case of “Revival Hijack” is much extra harmful than the usual typosquatting assaults on PyPI, as customers pulling an replace for his or her chosen initiatives do not make a mistake.
To mitigate the menace, customers and organizations can use bundle pinning to remain on specified, identified to be reliable variations, confirm bundle integrity, audit its contents, and look out for modifications in bundle possession or atypical replace exercise.
