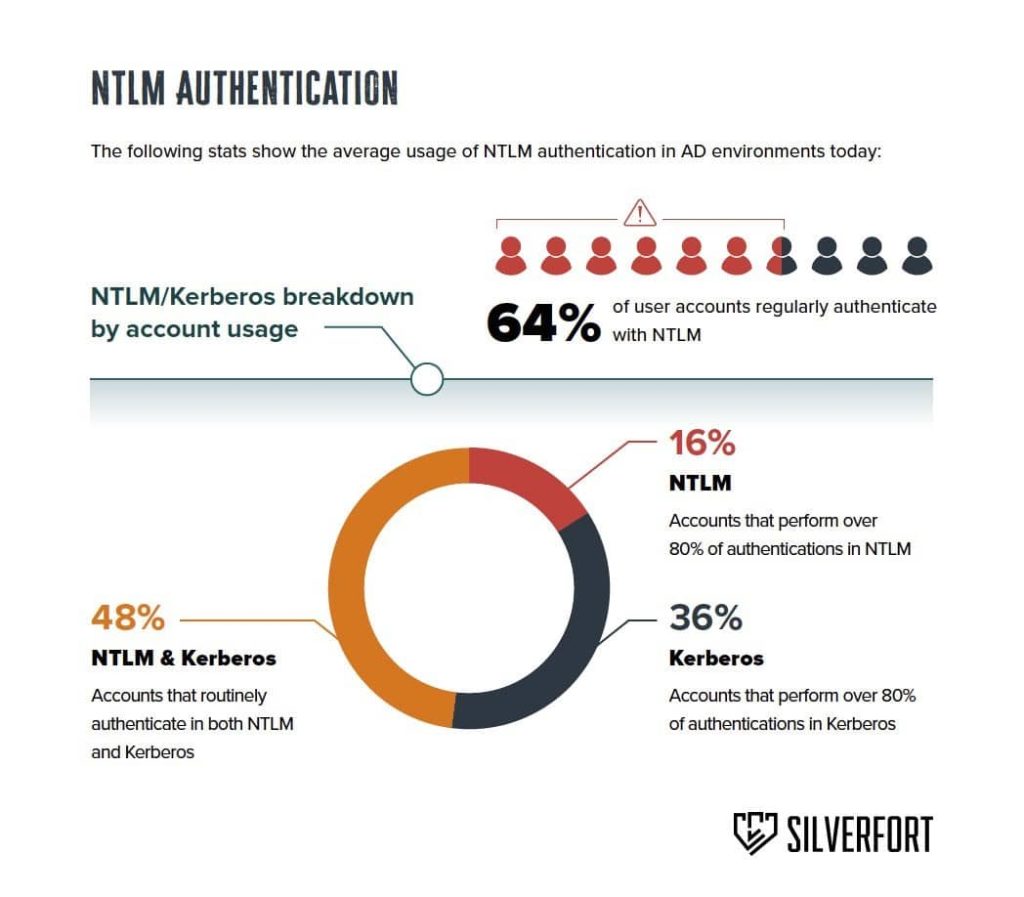
Silverfort has found {that a} misconfiguration can bypass an Lively Listing Group Coverage designed to disable NTLMv1, permitting NTLMv1 authentications to persist. Microsoft introduced the complete decommission of NTLMv1 from Home windows 2025.
Unified Identification Safety firm Silverfort has found a safety vulnerability involving a misconfiguration in Lively Listing. This vulnerability permits NTLMv1 authentication to persist regardless of makes an attempt to disable it by means of Group Coverage.
NTLMv1 is an outdated authentication protocol with recognized safety weaknesses, making it a main goal for attackers. The flaw, found by senior safety researcher Dor Segal, uncovered that even groups implementing this coverage stay uncovered to NTLMv1 authentications.
The vulnerability arises from a flaw within the implementation of the Group Coverage. Whereas the coverage goals to dam NTLMv1, sure on-premises functions can bypass this restriction by particularly requesting NTLMv1 authentication. This bypass creates a false sense of safety for organizations that imagine they’ve successfully disabled NTLMv1. Attackers can exploit this vulnerability to intercept NTLMv1 site visitors, crack person credentials, and acquire unauthorized system entry.
Attackers can exploit NTLMv1’s weaknesses to maneuver laterally or escalate privileges, exposing organizations to vital threat.
“It is important to note that Windows clients with LMCompatibilityLevel 3 and above will not generate NTLMv1 if requested. However, non-Windows clients are not protected. If an application requests an NTLMv1 message from a non-Windows client, the Domain Controller may approve the authentication and generate a session key,” researchers famous in a weblog put up.
Silverfort’s analysis highlights the safety weaknesses of NTLMv1, corresponding to its susceptibility to relay assaults and the constraints of the Group Coverage mechanism in utterly stopping its use. By understanding the technical intricacies of NTLMv1 and the constraints of current mitigation methods, organizations can higher assess their threat publicity and implement efficient safety measures.
Though Microsoft has acknowledged the problem and introduced plans to utterly take away NTLMv1 assist in future variations of Home windows, organizations nonetheless have to take proactive measures to mitigate the danger. These measures embrace enabling audit logs for NTLM authentication, figuring out functions that make the most of NTLMv1, and implementing trendy authentication strategies corresponding to SSO or Kerberos to interchange NTLMv1.
RELATED TOPICS
- NTLM Credential Theft in Python Apps Threaten Home windows
- Hackers Exploit Jupyter Servers for Unlawful Sports activities Streaming
- 7-Zip Exploit Code Traced to AI-Generated Misinterpretation
- Vital Home windows Zero-Day Alert: No Patch Out there for Customers
- Fabrice Malware on PyPI Stealing AWS Credentials for 3 Years
High/Featured Picture by way of FreePik