Whereas disclosure of software program vulnerabilities and knowledge breaches has grow to be extra accepted over the previous three a long time, researchers and whistleblowers proceed to danger lawsuits and legal prices relying on the nation wherein they stay.
In April 2022, for instance, police in Istanbul arrested unbiased Turkish journalist İbrahim Haskoloğlu after he revealed particulars of a breach of presidency knowledge in Turkey. The nation’s ruling get together has since proposed a regulation to make the false reporting of a knowledge breach against the law punishable by two to 5 years in jail — a regulation that critics say will stop disclosure of actual knowledge breaches.
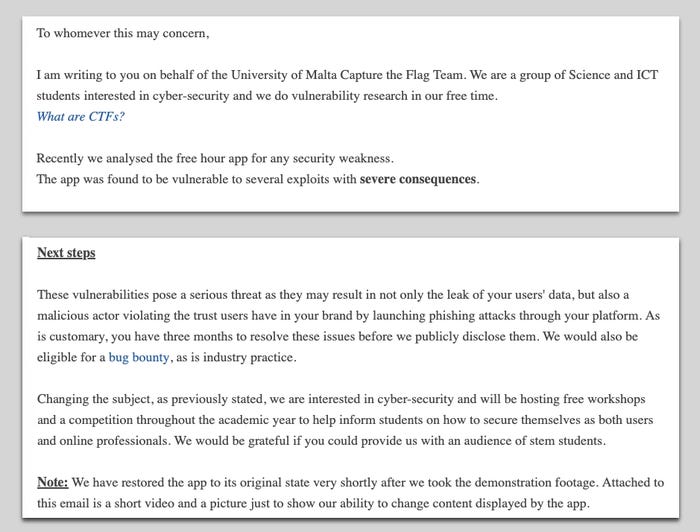
And within the island nation of Malta, three computer-science college students and their lecturer on the College of Malta will probably be charged in March, two years after they discovered vulnerabilities in scheduling service FreeHour and notified the corporate. FreeHour claimed the disclosure gave the impression to be a ransom demand and reported the scholars to the police — though, since then the agency has criticized the nation’s lack of clear exemptions for researchers.
The scholars proceed to face prices, nonetheless.
“I hope that at the end of this case, it results in a better climate for cybersecurity, but I’m genuinely exhausted from this whole situation,” Michael Debono, one of many college students, said in a submit on Fb. “It’s crazy that I’ve had to spend almost two years now dealing with the fallout of an incident that should have been resolved over a table in a day with FreeHour and the police.”
Turkey and Malta are usually not the one international locations to crack down individuals who report knowledge breaches and software program vulnerabilities. In Poland, a prepare producer threatened to sue three moral hackers who circumvented a kill code that the cybersecurity professionals declare disabled trains that had been parked in a third-party restore facility. In China, vulnerability researchers who don’t first report software program points to the federal government danger jail time.
Even within the US, the place vulnerability-disclosure points have been debated for many years, firms and authorities companies nonetheless sometimes resort to authorized assaults reasonably than civil engagement. In September 2024, the town authorities of Columbus, Ohio, filed a lawsuit towards whistleblower David L. Ross after he disputed the importance of a knowledge breach, claiming that Ross colluded with the ransomware gang behind the breach. Two months later, the town settled the lawsuit.
Defensive Driving and Disclosure
Worldwide, vulnerability researchers must take care when disclosing software program safety points. Erring on the aspect of security, like defensive driving, needs to be the default for cybersecurity researchers and whistleblowers, says Trey Ford, chief data safety officer at San Francisco-based Bugcrowd, who connects its secure of unbiased penetration testers with shoppers.
The October 2022 electronic mail that resulted in three college students and their lecturer dealing with prices. Supply: Lecturer Luke Collins’ web site
In one of the best case, researchers ought to receive permission from the focused group to conduct analysis and disclose findings, he says.
“The reality now is: If you see something, and you’re not absolutely sure — and don’t have receipts and proof — maybe don’t say anything, or you risk going to jail,” Ford says, declaring that defensive or vindictive organizations may cause hassle. Any danger might be “further amplified by the misaligned incentives of companies that would prefer not to address an issue. These companies have the power to almost completely silence the reporter.”
As well as, working with the group reasonably than instantly adopting an adversarial method can assist decrease potential misinformation about what constitutes a breach or vulnerability, says Ilona Cohen, chief authorized and coverage officer at HackerOne, a hacking-services platform.
Researchers also needs to at all times be cognizant of native regulation, she says.
“Whether a data breach has occurred or a vulnerability is present are not always clear-cut,” Cohen says. “It’s not uncommon for countries to have laws against fraudulent misrepresentation, but lawmakers must take care not to target individuals that do not intend to deceive or to cause harm.”
Benign Intent or Hostile Actions
To this point, the researchers and whistleblowers are paying the worth of the shortage of readability. Turkish journalist Haskoloğlu, for instance, claimed he notified the Turkish authorities two months earlier than his disclosure, after being contacted by the hackers that the info had been stolen. Final month, he introduced he would depart Turkey following escalating dying threats.
In December, Newag — the prepare producer in Poland that allegedly bricked trains not repaired in its workshops — filed a lawsuit towards the three hackers who found and publicized their workaround for the kill code. Whereas the European Union adopted a right-to-repair regulation for client items in 2024, it is unclear whether or not industrial tools, reminiscent of trains and equipment, are coated.
The incidents spotlight that organizations are aiming to silence researchers, reasonably than interact publicly with them, says Dustin Childs, the pinnacle of risk consciousness and the Zero Day Initiative at Development Micro, which maintains a third-party bug bounty program.
“It’s a disturbing trend I hope reverses soon,” he says. “We need to offer safe harbor to researchers who are willing to report vulnerabilities in a coordinated manner. Unfortunately, this trend is unlikely to change without either litigation or legislation.”
Globally, nonetheless, laws seems to be shifting in a unique route. In August 2024, the UN Normal Meeting adopted the Conference Towards Cybercrime, which makes it against the law to “access … an information or communications technology (ICT) system without right” or to intercept knowledge or communications. Digital-rights teams fear that the treaty will result in extra legal guidelines that penalize authentic safety analysis.
Whereas Turkey seems to be the primary nation since August to go a extra strict cybercrime statue, harder laws appear more and more doubtless, Childs says.
“Overall, we are currently in a climate where governments favor businesses over individual researchers,” he says. “It would not surprise me to see similar measures in other countries.”