Menace actors are benefiting from when safety professionals are off-duty to stage their ransomware assaults, new analysis has discovered. The ThreatDown 2024 State of Ransomware report from Malwarebytes has revealed most incidents within the final yr occurred between 1 a.m. and 5 a.m.
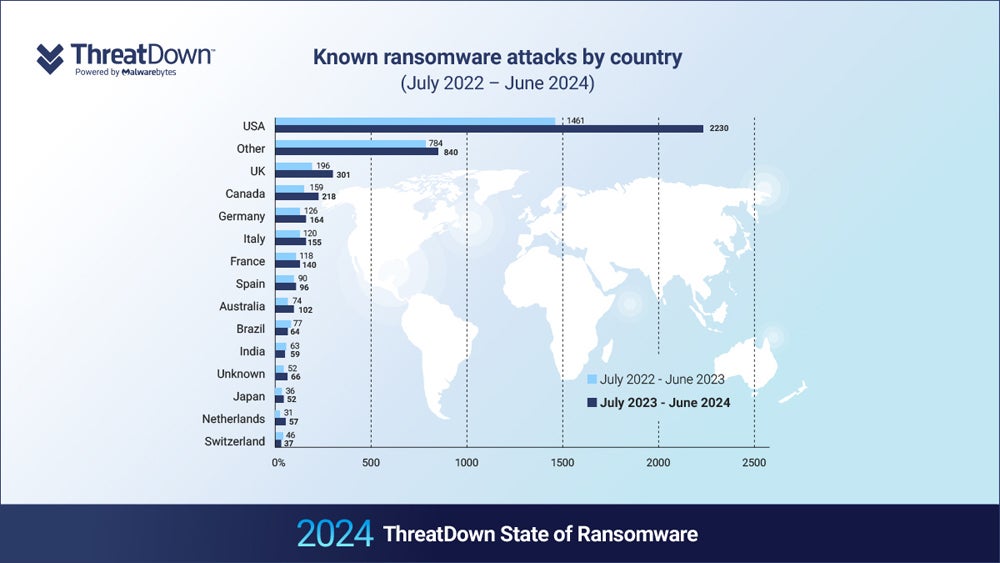
The report’s authors used knowledge from the ThreatDown Managed Detection and Response workforce to conduct their analysis. It discovered that international ransomware assaults elevated by 33% within the final yr, with the top-targeted nations seeing the biggest rises. The U.Ok. skilled a 67% hike in recognized assaults, and the U.S. noticed a 63% enhance.
“The question I ask organizations is ‘do you have someone prepared to stop an attack at 2 a.m. on a Sunday with your existing technology stack and staff resources?’” Chris Kissel, analysis vice chairman at IDC’s Safety & Belief Merchandise group, stated in a press launch.
“They may have a tool to pick up the alert on Monday morning, but by then it will be too late. Threat actors are moving fast to compromise networks, download data and deploy ransomware.”
Marcin Kleczynski, founder and CEO of Malwarebytes, added, “Ransomware gangs have time and motivation on their aspect. They continually evolve to reply to the newest applied sciences chasing at their tails.
“We’ve seen this very distinctly over the past year as widespread adoption of technologies like EDR has helped identify attackers before they launch malware, pushing ransomware gangs to work more quickly and put more effort into hiding themselves. Organizations and MSPs need additional support and continuous coverage to outmaneuver today’s criminals.”
Smaller ransomware teams have gotten extra prolific
The proportion of ransomware assaults being performed by small gangs exterior the highest 15 most lively teams rose from 25% to 31% final yr. This means that staging ransomware assaults is turning into extra accessible to much less skilled attackers.
In January 2024, the U.Ok.’s Nationwide Cyber Security Centre warned that the specter of ransomware was anticipated to rise even additional as a result of new availability of AI applied sciences reducing the barrier to entry. For instance, Google Cloud analysts stated that generative AI could also be utilized in name centres operating ransomware negotiations.
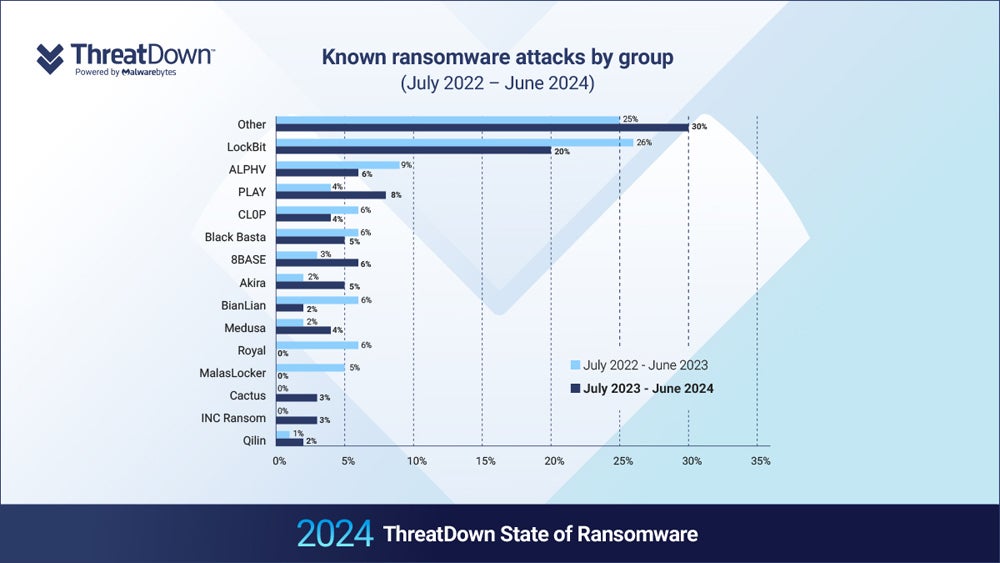
The Malwarebytes report additionally discovered that the proportion of ransomware assaults that dominant ransomware-as-a-service group LockBit claimed accountability for decreased from 26% to twenty% over the previous yr, regardless of finishing up extra particular person assaults.
SEE: 94% of Ransomware Victims Have Their Backups Focused
LockBit’s dominance could have taken a success after the U.Ok. Nationwide Crime Company’s Cyber Division, the FBI, and worldwide companions efficiently minimize off entry to its web site, which had been used as a big ransomware-as-a-service storefront, in February.
Nevertheless, a number of days later, the group resumed operations at a distinct Darkish Net deal with and continues to assert accountability for international ransomware assaults.
ALPHV, the second-most prolific ransomware group, additionally created a emptiness after a sloppily executed cyber assault towards Change Healthcare in February. The group didn’t pay an affiliate their proportion of the $22 million ransom, so the affiliate uncovered them, prompting ALPHV to pretend a legislation enforcement takeover and stop operations.
The authors wrote, “With ALPHV gone and LockBit’s future uncertain, other gangs are certain to be trying to attract their affiliates and supplant them as the dominant forces in ransomware.”
SEE: Report: Impacts of AI on Cyber Security Panorama
Prime focused industries for ransomware within the U.S. and worldwide in 2024
Ransomware is a rising menace all around the world, with the variety of enterprises attacked rising by 27% in 2023 and payouts exceeding $1 billion (£790 million) for the primary time. Globally, ransomware injury prices are predicted to exceed $265 billion by 2031.
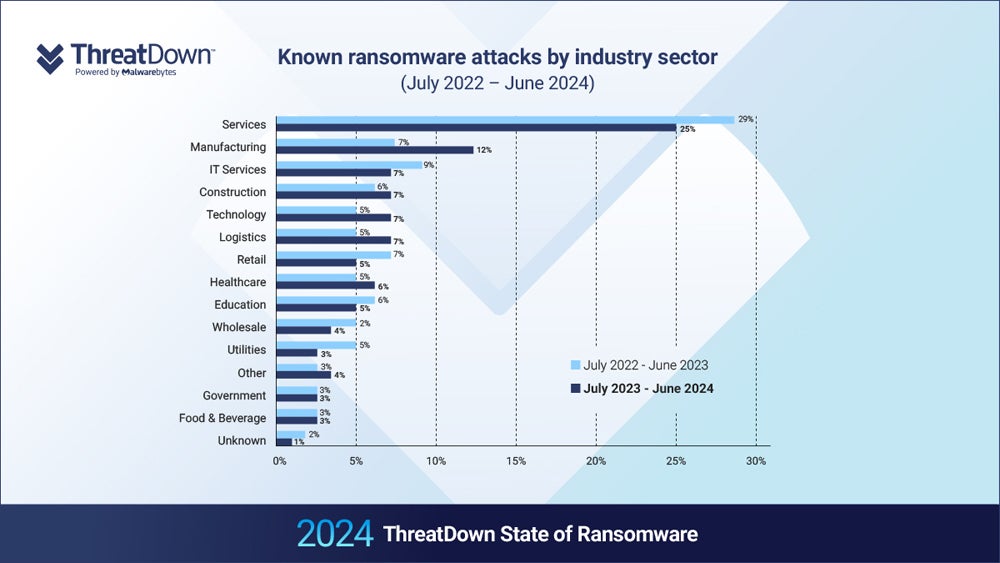
In keeping with the Malwarebytes report, the providers business is the worst affected, accounting for nearly 1 / 4 of worldwide ransomware assaults. Compromising essential nationwide infrastructure can result in widespread disruption, making it a primary goal for ransomware.
In Could, the U.Ok.’s Nationwide Cyber Security Centre and different worldwide cyber authorities, together with the FBI, warned about cyber assaults focusing on suppliers of operational know-how. The advisory got here in gentle of “continued malicious cyber activity” towards water, power, and meals and agriculture companies between 2022 and April 2024.
SEE: How hackers infiltrate essential infrastructure
The report additionally discovered that, whereas the U.S. accounts for almost half of all ransomware assaults worldwide, it takes on 60% of worldwide assaults on the schooling sector and 71% of them on healthcare.
This might be associated to its extremely privatised, and subsequently rich, healthcare system and better schooling establishments, in addition to strict laws reminiscent of HIPAA and FERPA that stress organisations into paying the ransom to keep away from fines.
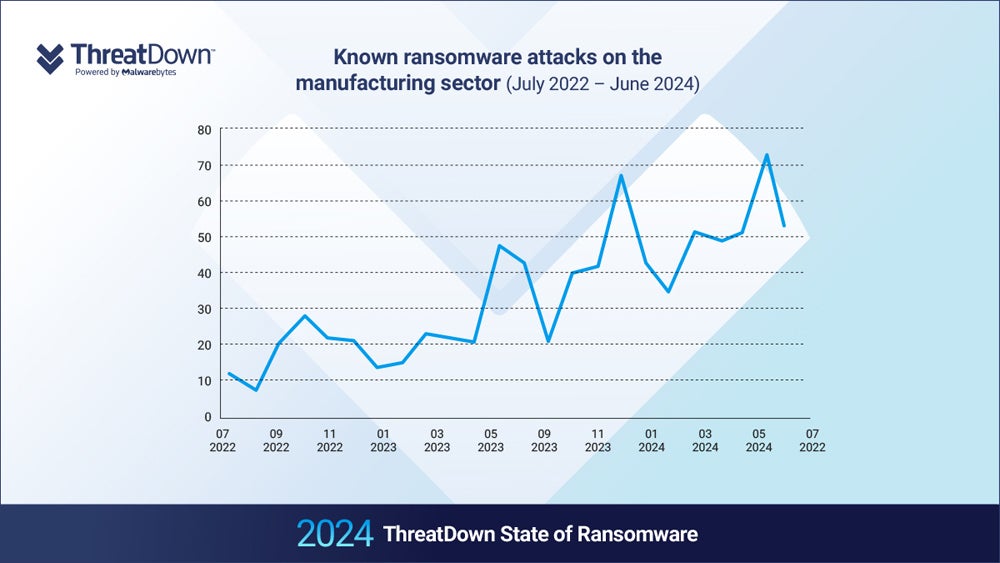
The worldwide manufacturing sector noticed a 71% year-on-year enhance in ransomware assaults, corresponding with rising software program spend within the sector.
“The most likely explanation therefore is that the number of available targets in the manufacturing sector has increased over the last two years, perhaps because of increasing digitization within the sector,” the authors wrote.
Tactical shifts of ransomware attackers in 2024
The ThreatDown MDR workforce famous an increase in living-off-the-land methods being utilized by ransomware gangs, reminiscent of LockBit, Akira, and Medusa. Dwelling-off-the-land is the usage of authentic, pre-installed instruments and software program inside a goal atmosphere throughout an assault to assist evade detection.
This may cut back the general complexity of the malware by permitting the attacker to weaponize present options which have already been safety examined by the organisation, in addition to making detection and prevention tougher. The M-Tendencies 2024 report, from Google subsidiary Mandiant, additionally famous a rise in living-off-the-land assaults again in Could.
The M-Tendencies report additionally discovered that the median dwell time — the period of time attackers stay undetected inside a goal atmosphere — of worldwide organisations fell from 16 days in 2022 to 10 days in 2023.
Malwarebytes’ report signifies this sooner assault timeline too, with ThreatDown Incident Response knowledge exhibiting how your complete ransomware assault chain, from preliminary entry to knowledge encryption, has diminished from weeks to hours.