A ransomware operation targets Home windows system directors by taking out Google advertisements to advertise faux obtain websites for Putty and WinSCP.
WinSCP and Putty are in style Home windows utilities, with WinSCP being an SFTP consumer and FTP consumer and Putty an SSH consumer.
System directors generally have greater privileges on a Home windows community, making them precious targets for menace actors who need to rapidly unfold by means of a community, steal knowledge, and acquire entry to a community’s area controller to deploy ransomware.
A latest report by Rapid7 says {that a} search engine marketing campaign displayed advertisements for faux Putty and WinSCP websites when looking for obtain winscp or obtain putty. It’s unclear if this marketing campaign passed off on Google or Bing.
These advertisements used typosquatting domains like puutty.org, puutty[.]org, wnscp[.]internet, and vvinscp[.]internet.
Whereas these websites impersonated the professional website for WinSCP (winscp.internet), the menace actors imitated an unaffiliated website for PuTTY (putty.org), which many individuals consider is the actual website. The official website for PuTTY is truly https://www.chiark.greenend.org.uk/~sgtatham/putty/.
These websites embrace obtain hyperlinks that, when clicked, will both redirect you to professional websites or obtain a ZIP archive from the menace actor’s servers primarily based on whether or not you had been referred by a search engine or one other website within the marketing campaign.
Supply: Rapid7
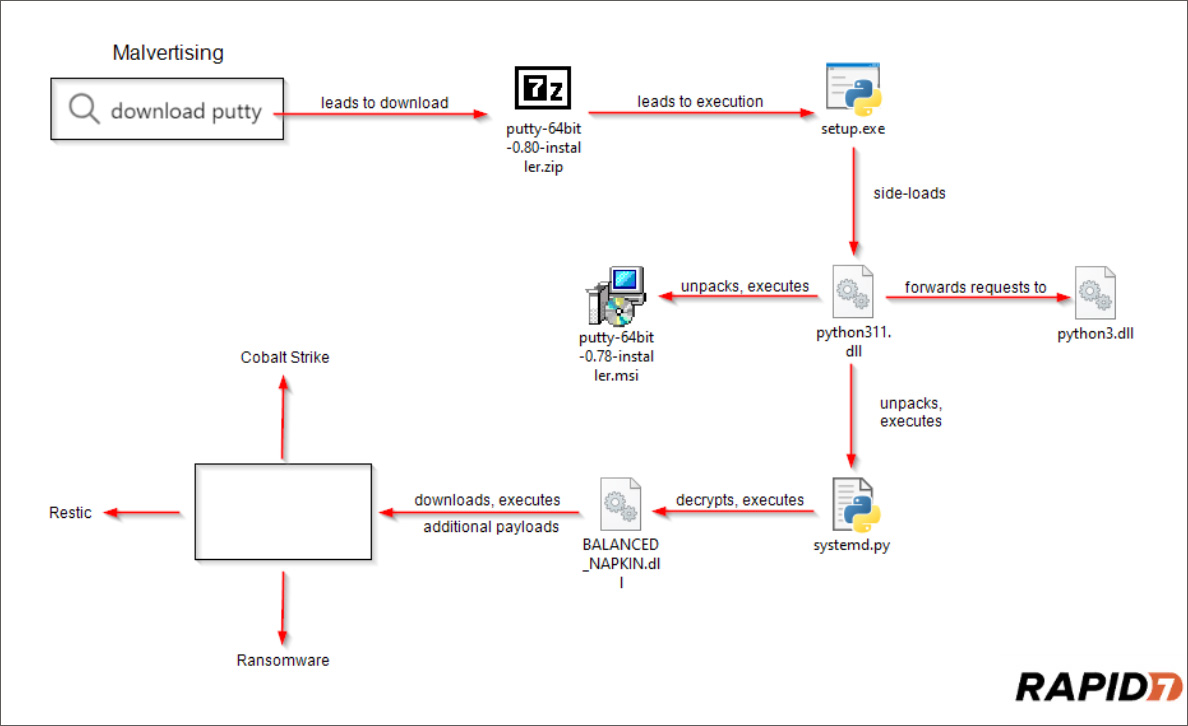
The downloaded ZIP archives include a Setup.exe executable, which is a renamed and bonafide executable for Python for Home windows (pythonw.exe) , and a malicious python311.dll file.
When the pythonw.exe executable is launched, it’ll try to launch a professional python311.dll file. Nevertheless, the menace actors changed this DLL with a malicious model loaded as an alternative utilizing DLL Sideloading.
When a consumer runs the Setup.exe, considering it is putting in PuTTY or WinSCP, it masses the malicious DLL, which extracts and executes an encrypted Python script.
This script will finally set up the Sliver post-exploitation toolkit, a preferred software used for preliminary entry to company networks.
Rapid7 says the menace actor used Sliver to remotely drop additional payloads, together with Cobalt Strike beacons. The hacker used this entry to exfiltrate knowledge and try to deploy a ransomware encryptor.
Supply: Rapid7
Whereas Rapid7 shared restricted particulars concerning the ransomware, the researchers say the marketing campaign is just like these seen by Malwarebytes and Pattern Micro, which deployed the now-shutdown BlackCat/ALPHV ransomware.
“In a recent incident, Rapid7 observed the threat actor attempt to exfiltrate data using the backup utility Restic, and then deploy ransomware, an attempt which was ultimately blocked during execution,” explains Rapid7’s Tyler McGraw.
“The associated methods, ways, and procedures (TTP) noticed by Rapid7 are harking back to previous BlackCat/ALPHV campaigns as reported by Pattern Micro final 12 months.”
Search engine ads have turn out to be an enormous drawback over the previous couple of years, with quite a few menace actors using them to push malware and phishing websites.
These ads had been for in style applications, together with Keepass, CPU-Z, Notepad++, Grammarly, MSI Afterburner, Slack, Dashlane, 7-Zip, CCleaner, VLC, Malwarebytes, Audacity, μTorrent, OBS, Ring, AnyDesk, Libre Workplace, Teamviewer, Thunderbird, and Courageous.
Extra lately, a menace actor took out Google advertisements that included the professional URL for the crypto buying and selling platform Whales Market. Nevertheless, the advert led to a phishing website containing a cryptodrainer to steal guests’ cryptocurrency.