Safety researchers analyzing the comparatively new RansomHub ransomware-as-a-service imagine that it has evoloved from the at present defunct Knight ransomware challenge.
RansomHub has a brief historical past and operated primarily as a knowledge theft and extortion group that sells stolen information to the very best bidder.
The gang grabbed consideration in mid-April when it leaked stolen knowledge from United Well being subsidiary Change Healthcare following a BlackCat/ALPHV assault, suggesting some type of collaboration between the 2.
Extra lately, on Could 28, the worldwide public sale home Christie’s admitted it had suffered a safety incident after RansomHub threatened to leak stolen knowledge.
Knight ransomware launched in late July 2023 as a re-brand of the Cyclops operation and began breaching Home windows, macOS, Linux/ESXi machines to steal knowledge and demand a ransom.
One of many peculiarities of Knight was that it additionally provided associates an info-stealer part that would make the assaults extra impactful.
In February 2024, the supply code for model 3.0 of Knight ransomware put up on the market on hacker boards, the victims extortion portal went offline, and the RaaS operation went silent.
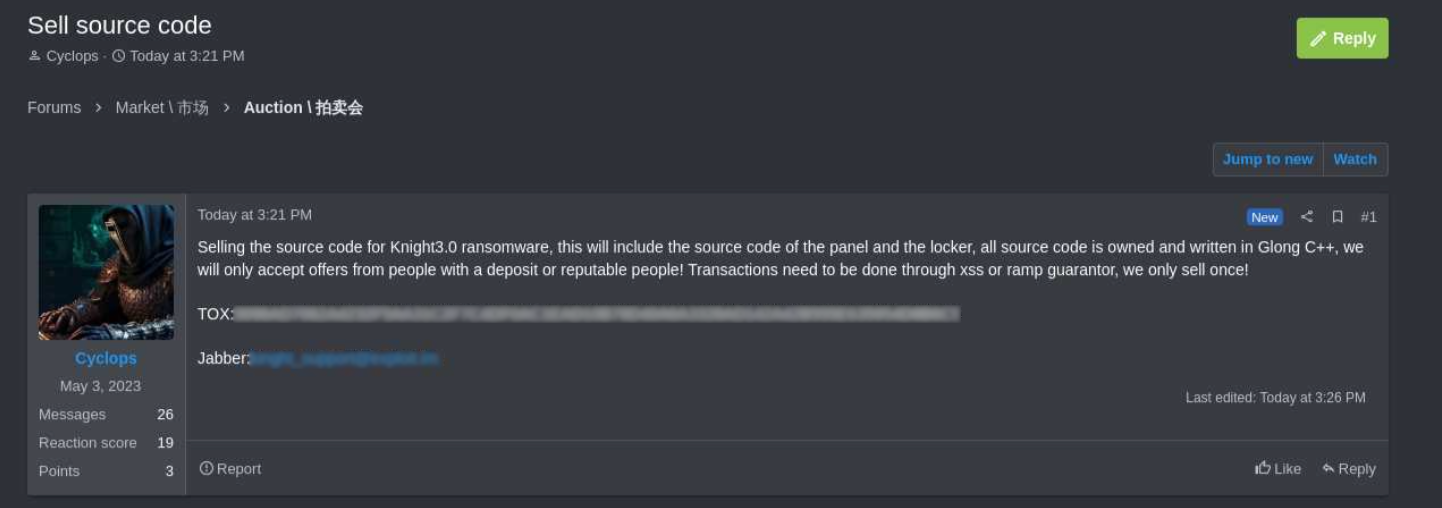
supply: KELA
RansomHub’s Knight origin
Malware analysts at Symantec, a part of Broadcom, discovered a number of similarities between the 2 ransomware households that time to a typical origin:
- Each ransomware households are written in Go and use Gobfuscate for obfuscation.
- There are intensive code overlaps within the two malware payloads.
- Each use a novel obfuscation method the place necessary strings are encoded with distinctive keys.
- The ransom notes utilized by the 2 ransomware households are comparable, with minor updates added on RansomHub.
- Each ransomware households restart endpoints in secure mode earlier than encryption.
- The command-line assist menus on the 2 households are an identical, with the one distinction being a ‘sleep’ command on RansomHub.
- The sequence and technique of command execution operations are the identical, although RansomHub now executes them by way of cmd.exe.
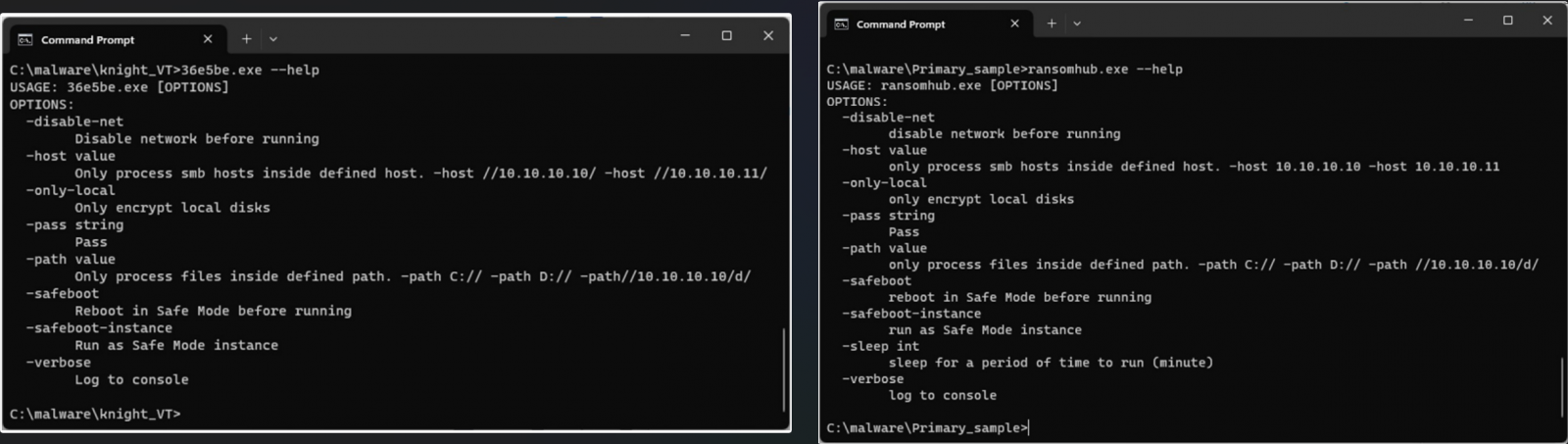
Supply: Symantec
The above means that RansomHub was seemingly derived from Knight, and confirms that the extortion group certainly makes use of a knowledge encryptor.
Additionally, the time RansomHub first appeared within the cybercrime house, in February 2024, matches the Knight supply code sale.
In response to the researchers, it’s unlikely that RansomHub is run by Knight ransomware creators. They imagine that one other actor bought the Knight supply code and began utilizing it in assaults.
Because it emerged, RansomHub has grown to grow to be one of the vital prolific RaaS operations, which Symantec attributes to the gang attracting former associates of the ALPHV operation, resembling Notchy and Scattered Spider.
