Mandiant has recognized a novel technique to bypass browser isolation expertise and obtain command-and-control operations by means of QR codes.
Browser isolation is an more and more fashionable safety expertise that routes all native net browser requests by means of distant net browsers hosted in a cloud setting or digital machines.
Any scripts or content material on the visited net web page is executed on the distant browser fairly than the native one. The rendered pixel stream of the web page is then despatched again to the native browser that made the unique request, solely displaying what the web page seems to be like and defending the native system from any malicious code.
Many command and management servers make the most of HTTP for communication, inflicting distant browser isolation to filter the malicious site visitors and making these communication fashions ineffective.
The brand new approach by Mandiant makes an attempt to bypass these restrictions, and although it has some sensible limitations, it demonstrates that current safety protections in browsers are removed from excellent, calling for “defense in depth” methods that mix extra measures.
Background on C2s and browser isolation
C2 channels allow malicious communications between attackers and compromised techniques, giving distant actors management over the breached system and the flexibility to execute instructions, exfiltrate information, and extra.
As a result of browsers always work together with exterior servers by design, isolation measures are activated to forestall attackers from accessing delicate information on the underlying system in security-critical environments.
That is achieved by operating the browser in a separate sandboxed setting hosted on the cloud, an area digital machine, or on-premises.
When isolation is energetic, the remoted browser handles incoming HTTP requests, and solely the visible content material of the web page is streamed to the native browser, which means that scripts or instructions within the HTTP response by no means attain the goal.
This blocks attackers from instantly accessing the HTTP responses or injecting malicious instructions into the browser, making covert C2 communications tougher.
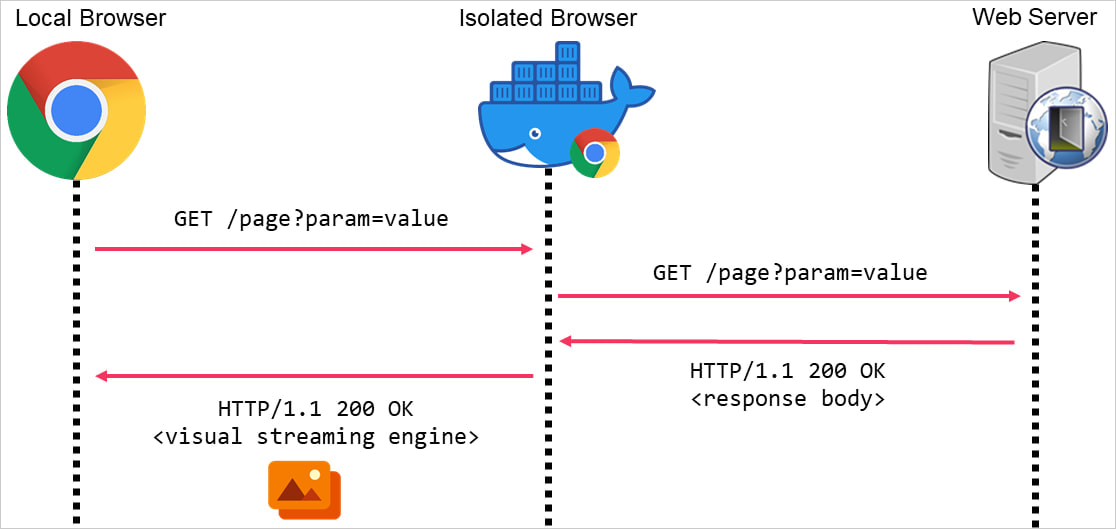
Supply: Mandiant
Mandiant’s bypass trick
Mandiant researchers have devised a brand new approach that may bypass current isolation mechanisms in trendy browsers.
As an alternative of embedding instructions in HTTP responses, the attacker encodes them in a QR code displayed visually on a webpage. Because the visible rendering of a webpage just isn’t stripped throughout browser isolation requests, the QR codes are capable of make it again to the consumer initiating the request.
In Mandiant’s examine, the “victim’s” native browser is a headless consumer managed by malware that has beforehand contaminated the system, which captures the retrieved QR code and decodes it to get the directions.
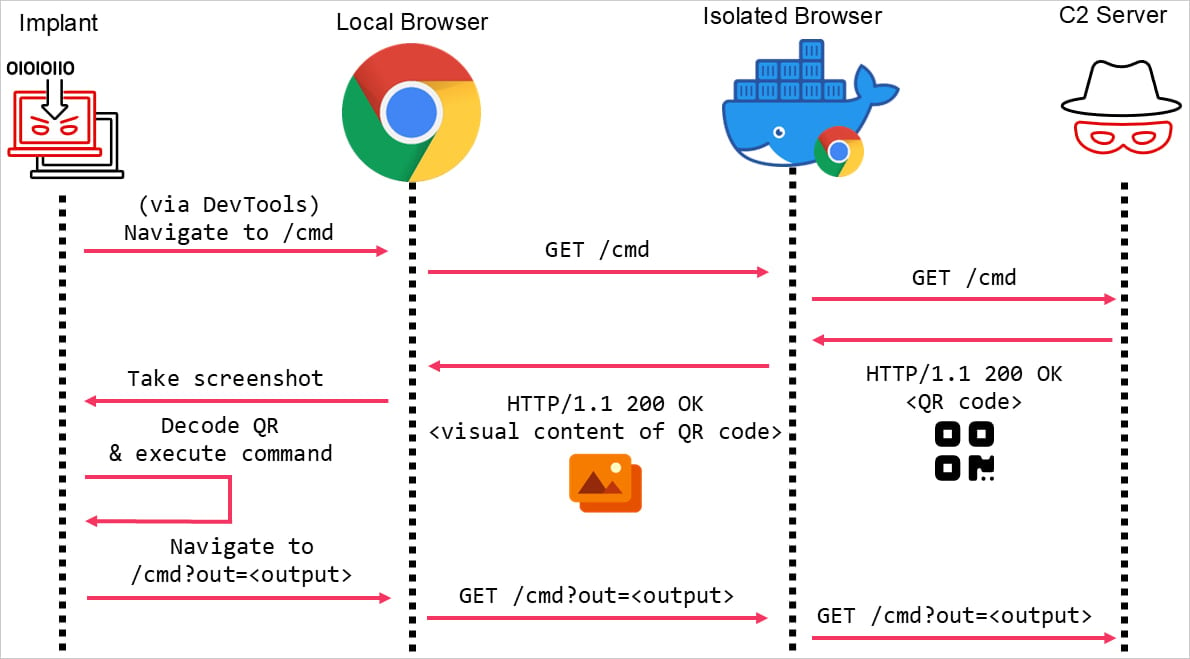
Supply: Mandiant
Mandiant’s proof-of-concept demonstrates the assault on the most recent Google Chrome net browser, integrating the implant by means of Cobalt Strike’s Exterior C2 characteristic, a broadly abused pen-testing package.

Not excellent
Whereas the PoC exhibits the assault is possible, the approach is not flawless, particularly contemplating real-world applicability.
First, the info stream is restricted to a most of two,189 bytes, which is roughly 74% of the utmost information QR codes can carry, and the packets must drop in dimension much more if there are points studying the QR codes on the malware’s interpreter.
Second, latency must be taken under consideration, as every request takes roughly 5 seconds. This limits the info switch charges to about 438 bytes/sec, so the approach just isn’t appropriate for sending giant payloads or facilitating SOCKS proxying.
Lastly, Mandiant says its examine didn’t contemplate extra safety measures like area fame, URL scanning, information loss prevention, and request heuristics, that will, in some circumstances, block this assault or render it ineffective.
Though Mandiant’s QR-code-based C2 approach is low bandwidth, it may nonetheless be harmful if not blocked. Subsequently, admins in crucial environments are really helpful to watch for irregular site visitors and headless browsers working in automation mode.
