Taiwanese {hardware} vendor QNAP has added a Safety Heart with ransomware safety capabilities to the newest model of its QTS working system for network-attached storage (NAS) gadgets.
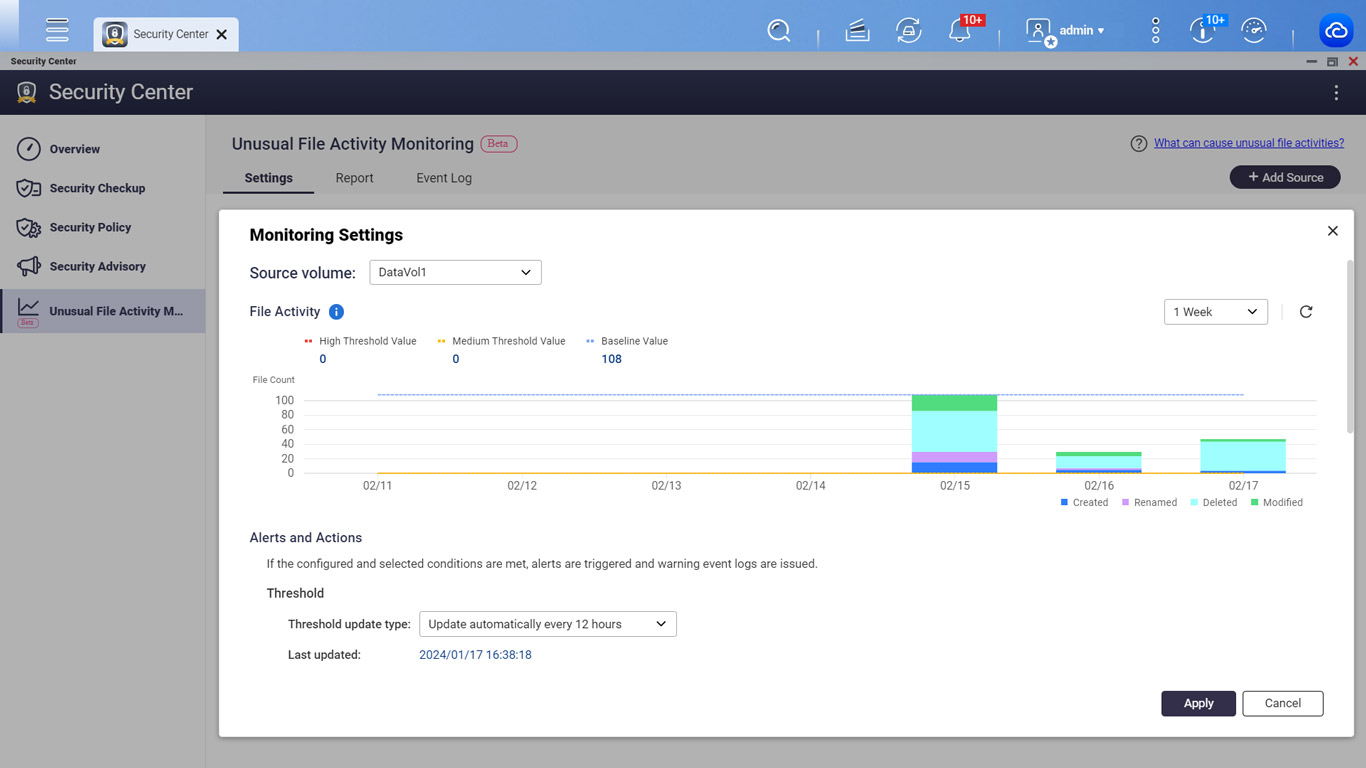
The brand new Safety Heart in QTS 5.2 screens for suspicious file operations to detect and block ransomware threats.
If any uncommon exercise is detected, clients can select to have volumes mechanically set to read-only mode to forestall recordsdata from being modified, create quantity snapshots to revive your complete quantity when wanted, and pause quantity snapshot scheduling to keep away from crowding out the space for storing with irregular snapshot recordsdata.
“This feature actively monitors file activities to preemptively protect data security,” the corporate revealed in a press launch on Tuesday.
“Upon detecting suspicious file behavior, the system swiftly implements protective measures (such as backup or blocking) to mitigate risks and prevent data loss from ransomware threats, attacks, or human error.”
The newest QTS model additionally provides quicker NAS startup and shutdown speeds (by as much as 30%), help for TCG-Ruby self-encrypting drives (SED), in addition to speedier backup and restoration of Home windows techniques, disks, folders, and recordsdata to their QNAP NAS by way of the NetBak PC Agent utility.
NAS gadgets are sometimes used for backing up and sharing delicate recordsdata, which makes them beneficial targets for attackers who steadily goal them to steal or encrypt beneficial paperwork or deploy information-stealing malware.
In recent times, malicious actors have focused QNAP gadgets in DeadBolt, Checkmate, and eCh0raix ransomware campaigns, abusing safety vulnerabilities to encrypt information on Web-exposed and weak NAS gadgets.
QNAP often warns clients about brute-force assaults in opposition to NAS gadgets uncovered on-line, which steadily result in ransomware assaults [1, 2, 3].
The NAS maker has additionally beforehand shared mitigation measures for patrons with Web-exposed gadgets, asking them to:
- Disable the router’s Port Forwarding operate by going to the router’s administration interface, checking the Digital Server, NAT, or Port Forwarding settings, and turning off the port forwarding setting of the NAS administration service port (ports 8080 and 433 by default).
- Disable the QNAP NAS’ UPnP operate by going to myQNAPcloud on the QTS menu, clicking “Auto Router Configuration,” and unselecting “Enable UPnP Port forwarding.”
QNAP clients must also use this step-by-step process to vary the system port quantity, toggle off SSH and Telnet connections, allow IP and account entry safety, and alter default machine passwords.
