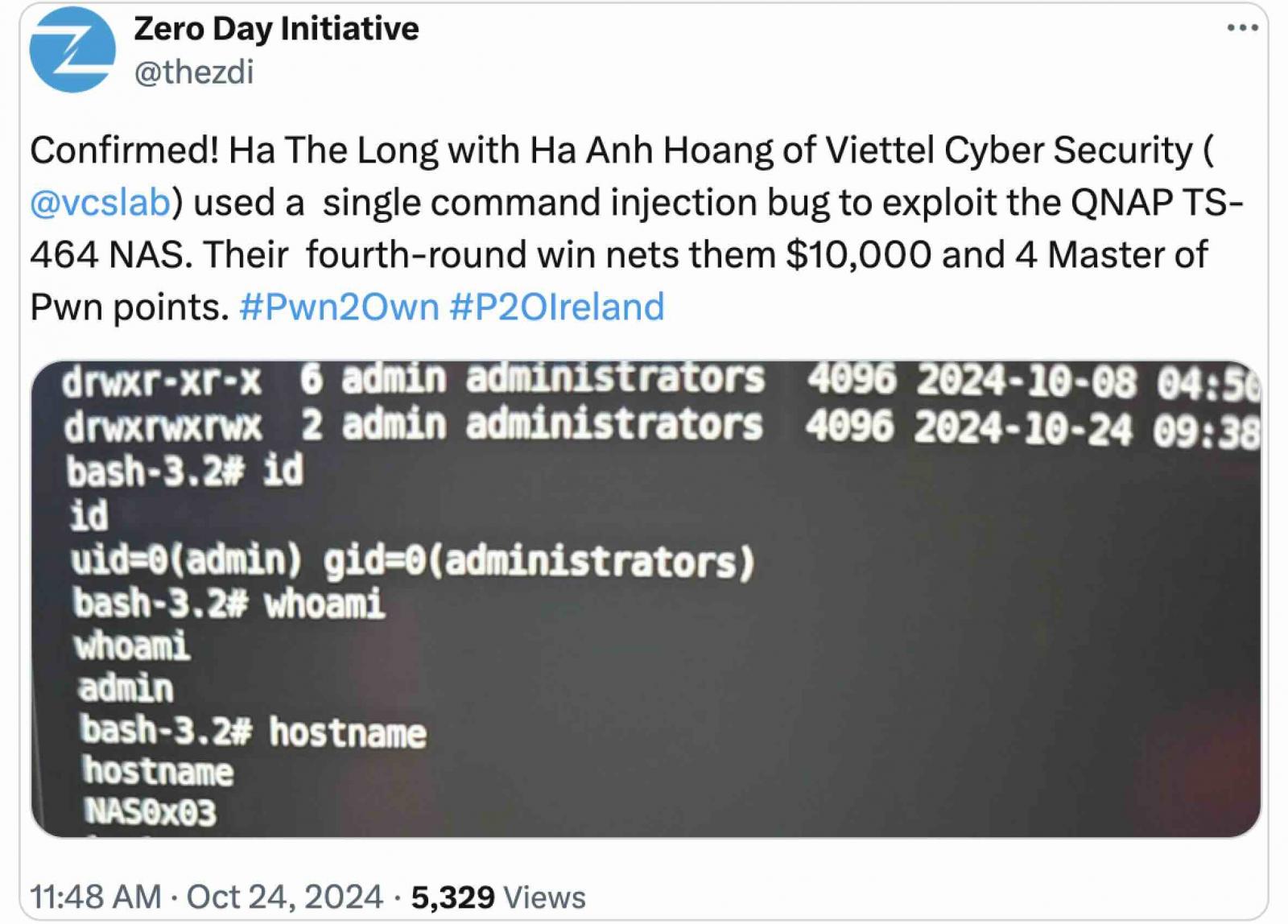
QNAP has mounted a important zero-day vulnerability exploited by safety researchers on Thursday to hack a TS-464 NAS machine through the Pwn2Own Eire 2024 competitors.
Tracked as CVE-2024-50388, the safety flaw is brought on by an OS command injection weak point in HBS 3 Hybrid Backup Sync model 25.1.x, the corporate’s catastrophe restoration and knowledge backup answer.
“An OS command injection vulnerability has been reported to affect HBS 3 Hybrid Backup Sync. If exploited, the vulnerability could allow remote attackers to execute arbitrary commands,” QNAP mentioned in a Tuesday safety advisory.
The corporate has addressed the safety bug in HBS 3 Hybrid Backup Sync 25.1.1.673 and later.
To replace HBS 3 in your NAS machine, log in to QTS or QuTS hero as an administrator, open the App Heart, and seek for “HBS 3 Hybrid Backup Sync”.
If an replace is out there, click on “Update”. Nevertheless, the “Update” button won’t be obtainable in case your HBS 3 Hybrid Backup Sync is already up-to-date.
The zero-day was patched 5 days after enabling Ha The Lengthy and Ha Anh Hoang of Viettel Cyber Security to execute arbitrary code and achieve admin privileges on the third day of Pwn2Own Eire 2024.
Nevertheless, after the Pwn2Own contest, distributors normally take their time to launch safety patches, seeing that they are given 90 days till Development Micro’s Zero Day Initiative publishes particulars on safety bugs demoed and disclosed through the contest.
Group Viettel gained Pwn2Own Eire 2024, which ended after 4 days of competitors, on Friday, October 25. Greater than $1 million in prizes have been awarded to hackers who disclosed over 70 distinctive zero-day vulnerabilities.
Three years in the past, QNAP additionally eliminated a backdoor account in its Hybrid Backup Sync answer (CVE-2021-28799), which was exploited along with an SQL Injection vulnerability in Multimedia Console and the Media Streaming Add-On(CVE-2020-36195) to deploy Qlocker ransomware onto Web-exposed NAS gadgets to encrypt information.
QNAP gadgets are a preferred goal amongst ransomware gangs as a result of they retailer delicate private information, making them good leverage for forcing victims to pay a ransom to decrypt knowledge.
In June 2020, QNAP warned of eCh0raix ransomware assaults exploiting Photograph Station app safety flaws. One yr later, eCh0raix (aka QNAPCrypt) returned in assaults exploiting recognized vulnerabilities and brute-forcing accounts with weak passwords.
QNAP additionally alerted prospects in September 2020 of AgeLocker ransomware assaults focusing on publicly uncovered NAS gadgets working older and weak Photograph Station variations.