A ransomware assault that hit pathology providers supplier Synnovis on Monday and impacted a number of main NHS hospitals in London has now been linked to the Qilin ransomware operation.
Ciaran Martin, the inaugural CEO of the UK’s Nationwide Cyber Security Centre (NCSC), mentioned immediately that the Qilin gang is probably going accountable for the incident
The assault has resulted in Synnovis being locked out of its techniques and is inflicting ongoing service disruptions at Man’s and St Thomas’ NHS Basis Belief, King’s School Hospital NHS Basis Belief, and varied major care suppliers throughout south east London.
“We believe it is a Russian group of cyber criminals who call themselves Qilin,” Martin instructed BBC Radio 4 on Wednesday.
“They’re simply looking for money. It’s unlikely they would have known that they would have caused such serious primary healthcare disruption when they set out to attack the company.”
An alert on Synnovis’ customer support portal at the moment warns of knowledge middle points and that each one techniques are at the moment inaccessible.
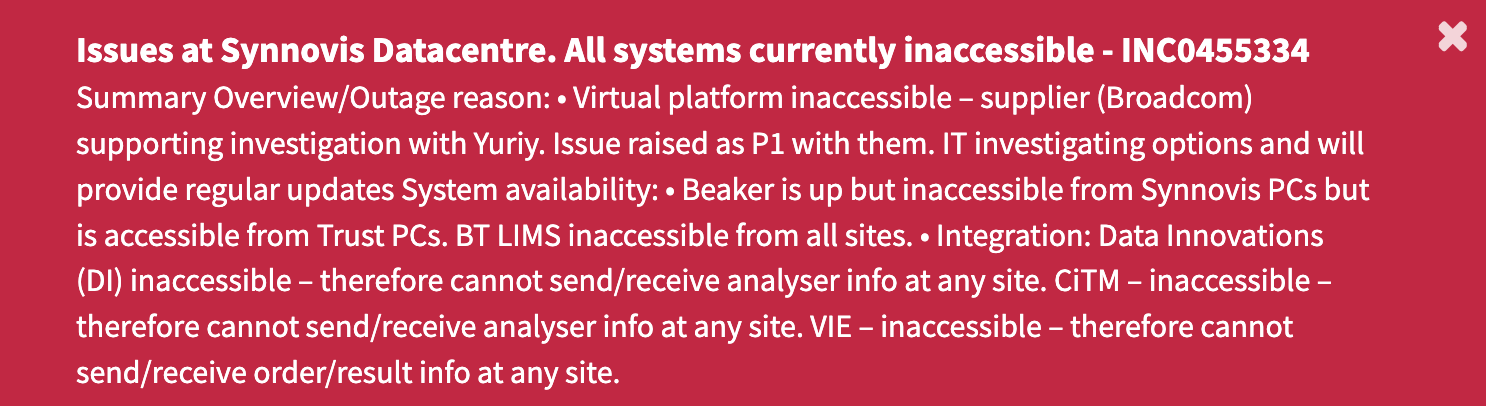
Memos despatched by officers of hospitals affected by the Synnovis ransomware assault revealed on Tuesday that this “ongoing critical incident” has had a “major impact” on their procedures and operations.
Some non-emergency pathology appointments, blood transfusions, and surgical procedures on the impacted London hospitals have been both postponed, canceled, or redirected to different suppliers.
The NHS mentioned on Wednesday that pressing and emergency providers like A&E, pressing care facilities, and maternity departments are open as ordinary. An NHS England cyber incident response group is at the moment assessing the full extent of the assault and its influence on affected person and worker knowledge.
“All urgent and emergency services remain open as usual and the majority of outpatient services continue to operate as normal,” an NHS spokesperson mentioned immediately.
“Unfortunately, some operations and procedures which rely more heavily on pathology services have been postponed, and blood testing is being prioritised for the most urgent cases, meaning some patients have had phlebotomy appointments cancelled.”
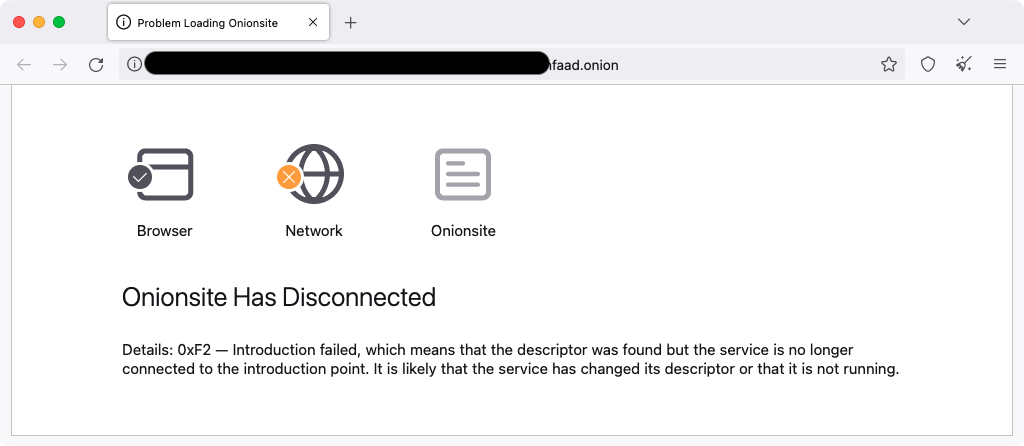
Qilin’s darkish internet leak web site is at the moment down, though there isn’t a proof that this outage is linked to the ransomware assault that hit Synnovis’ techniques on Monday, June 3.
The Qilin ransomware operation surfaced in August 2022 underneath the “Agenda” title however was rebranded as Qilin one month later.
The gang has been linked to or claimed a gradual stream of victims since its launch, with over 130 firms added to its darkish internet leak web site during the last two years. Nevertheless, Qilin operators have not been very lively till assaults picked up in the direction of the tip of 2023.
Since December 2023, these cybercriminals have additionally been creating probably the most superior and customizable Linux encryptors seen thus far, particularly designed to focus on VMware ESXi digital machines favored by enterprise organizations for his or her gentle useful resource wants.
Much like different ransomware gangs focusing on companies, Qilin operates by infiltrating an organization’s networks and extracting knowledge whereas shifting by means of the sufferer’s techniques.
After acquiring admin credentials for the servers and accumulating all delicate knowledge, the attackers deploy the ransomware payloads to encrypt all gadgets related to the community.
They then leverage the stolen knowledge and the encrypted recordsdata to hold out double-extortion assaults, pressuring the focused firms to satisfy their calls for. Thus far, BleepingComputer has seen ransom calls for starting from $25,000 to tens of millions of {dollars}, relying on the sufferer’s measurement.
