KEY SUMMARY POINTs from the article
- Malicious Packages Recognized: Zebo-0.1.0 and Cometlogger-0.1 are malicious Python packages found on PyPI.
- Delicate Information Theft: These packages steal consumer knowledge by means of keylogging, screenshot capturing, and data exfiltration.
- Persistence Mechanisms: They set up long-term management by creating startup scripts to re-execute on system reboot.
- Obfuscation Methods: Superior obfuscation strategies assist the packages evade detection and safety methods.
- Extensive Affect: These threats compromise builders and platforms reliant on PyPI, posing main privateness and safety dangers.
On November 24, 2024, Fortinet FortiGuard Lab’s AI-based detection system recognized Python malware in two malicious Python packages, Zebo-0.1.0 and Cometlogger-0.1, focusing on unsuspecting customers for his or her knowledge.
These packages can steal delicate data, seize screenshots, log keystrokes, and set up unauthorized management over contaminated methods, researchers famous within the weblog publish shared with Hackread.com.
What’s Zebo-0.1.0?
Zebo-0.1.0 reveals typical malware traits, together with features designed for surveillance, knowledge exfiltration, and unauthorized management, and makes use of libraries like pynput and ImageGrab, together with obfuscation strategies, indicating clear malicious intent.
The script employs obfuscation to cover its true performance, making it tougher for customers or safety methods to know its actions. This obfuscation can bypass safety measures, permitting the malware to run undetected.
Zebo-0.1.0 leverages pynput to log each keystroke made by the consumer and in addition captures screenshots of the desktop, probably violating their privateness. Moreover, the script exfiltrates delicate data, equivalent to keystrokes and screenshots, to a distant server, compromising consumer privateness.
To make sure persistence, the malware creates a Python script and a batch file within the Home windows Startup folder, guaranteeing its re-execution upon system startup, making it tough to take away and growing the chance of long-term injury.
What’s Cometlogger-0.1?
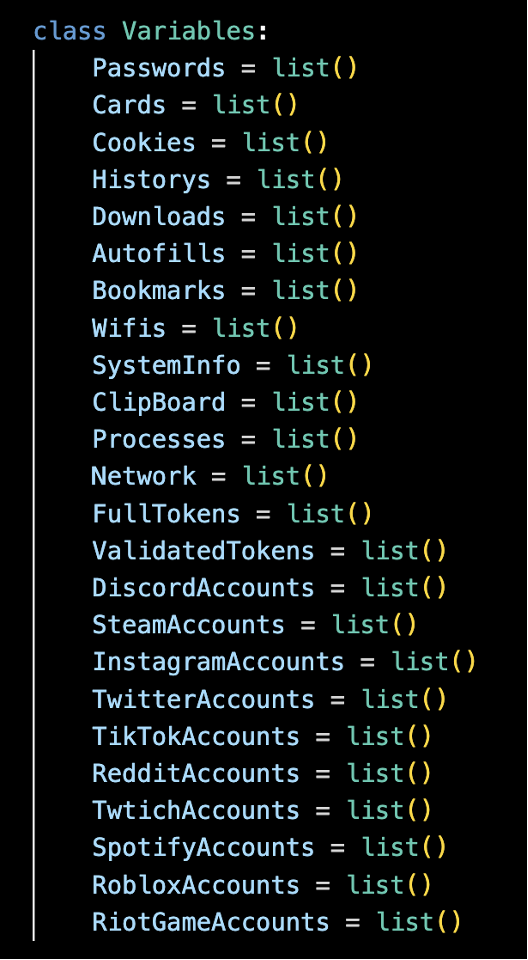
Cometlogger-0.1 maintains a long-term presence on the sufferer’s system and makes use of superior strategies like obfuscation, keylogging, display capturing, and knowledge exfiltration to compromise consumer knowledge. It dynamically requests a “webhook” from the consumer and embeds it into Python information, permitting for potential manipulation by unauthorized customers. This may redirect delicate knowledge to malicious servers or facilitate command-and-control operations.
The script additionally targets varied platforms like Discord, Steam, Instagram, and Twitter, stealing tokens, passwords, and account data. Moreover, it employs anti-VM detection strategies to evade evaluation and incorporates dynamic file modification capabilities, enabling the injection of malicious code.
Each packages are a serious menace to consumer privateness and safety. Zebo-0.1.0 actively collects delicate knowledge and transmits it to distant servers. Cometlogger-0.1, however, focuses on data theft and sustaining a persistent presence on the sufferer’s system. The affected methods embrace all these platforms the place PyPI packages could be put in with a Excessive severity stage, and threatens people or establishments whoever has put in these malicious packages.
The Python Bundle Index (PyPI) has turn into a useful useful resource for builders, providing an enormous repository of reusable code. Nevertheless, this comfort comes with inherent dangers as malicious actors are more and more exploiting it by publishing malicious packages that, when put in, can compromise methods. Socket Safety researchers final month found one other malicious Python bundle referred to as “Fabrice” on PyPI downloaded over 37,000 occasions since its inception in 2021, harvesting AWS credentials from builders for 3 years.
To guard in opposition to these threats, it’s essential to disconnect from the web, isolate the contaminated system, use respected antivirus software program, and reformat the system if mandatory.
RELATED TOPICS
- Why is studying Python necessary in Information Science?
- 6 official Python repositories plagued with cryptomining malware
- PythonAnywhere Cloud Platform Abused for Internet hosting Ransomware
- Python in Risk Intelligence: Analyzing – Mitigating Cyber Threats
- NTLM Credential Theft in Python Apps Threaten Home windows Safety