Pure Storage, a number one supplier of cloud storage techniques and companies, confirmed on Monday that attackers breached its Snowflake workspace and gained entry to what the corporate describes as telemetry info.
Whereas the uncovered info additionally included buyer names, usernames, and e-mail addresses, it didn’t include credentials for array entry or some other information saved on buyer techniques.
“Following a thorough investigation, Pure Storage has confirmed and addressed a security incident involving a third party that had temporarily gained unauthorized access to a single Snowflake data analytics workspace,” the storage firm stated.
“The workspace contained telemetry information that Pure uses to provide proactive customer support services. That information includes company names, LDAP usernames, email addresses, and the Purity software release version number.”
Pure took measures to forestall additional unauthorized entry to its Snowflake workspace and has but to seek out proof of malicious exercise on different components of its buyer infrastructure.
“We are currently in contact with customers who similarly have not detected unusual activity targeting their Pure systems,” the corporate added.
Greater than 11,000 clients use Pure Storage’s information storage platform, together with high-profile corporations and organizations like Meta, Ford, JP Morgan, NASA, NTT, AutoNation, Equinix, and Comcast.
At the very least 165 orgs seemingly impacted by Snowflake assaults
In a joint advisory with Mandiant and CrowdStrike, Snowflake revealed that attackers use stolen buyer credentials to focus on accounts missing multi-factor authentication safety.
Mandiant additionally linked the Snowflake assaults to a financially motivated menace actor tracked as UNC5537 since Might 2024.
The malicious actor features entry to Snowflake buyer accounts utilizing buyer credentials stolen in historic infostealer malware infections relationship again to 2020, focusing on lots of of organizations worldwide and extorting victims for monetary acquire.
“The impacted accounts were not configured with multi-factor authentication enabled, meaning successful authentication only required a valid username and password,” Mandiant stated.
“Credentials identified in infostealer malware output were still valid, in some cases years after they were stolen, and had not been rotated or updated. The impacted Snowflake customer instances did not have network allow lists in place to only allow access from trusted locations.”
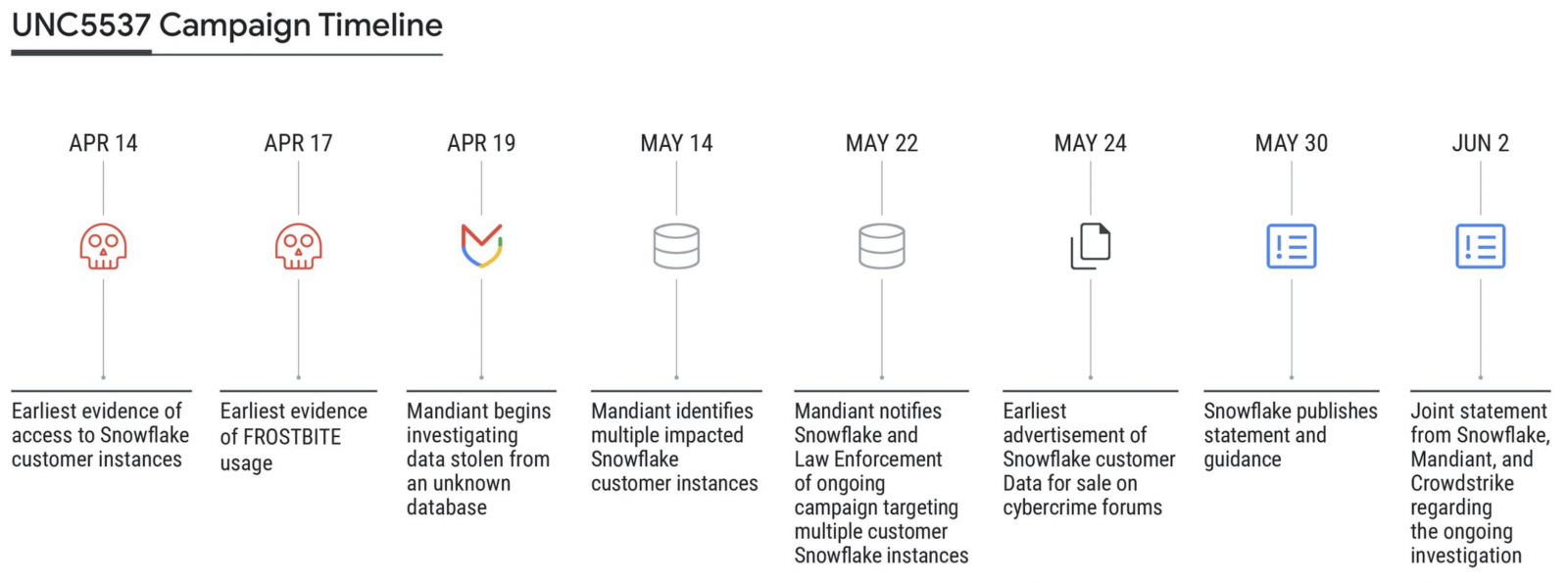
To this point, the cybersecurity firm has recognized lots of of buyer Snowflake credentials uncovered in Vidar, RisePro, Redline, Racoon Stealer, Lumm, and Metastealer infostealer malware assaults.
Snowflake and Mandiant have already notified round 165 organizations doubtlessly uncovered to those ongoing assaults.
Whereas Mandiant has not disclosed a lot details about UNC5537, BleepingComputer has discovered that they’re half of a bigger neighborhood of menace actors who incessantly go to the identical web sites, Telegram and Discord servers, the place they often collaborate on assaults.
Latest breaches at Santander, Ticketmaster, and QuoteWizard/LendingTree have additionally been linked to those ongoing Snowflake assaults. Ticketmaster’s mum or dad firm, Stay Nation, confirmed {that a} information breach affected the ticketing agencyafter its Snowflake account was compromised on Might 20.
A menace actor is now promoting 3TB of information from automotive aftermarket components supplier Advance Auto Components, allegedly together with 380 million buyer profiles and 44 million Loyalty / Fuel card numbers (with buyer particulars), stolen after the corporate’s Snowflake account was breached.
