North Korean hackers are infiltrating Western firms utilizing fraudulent IT employees to steal delicate information and extort ransom. Learn to establish these misleading techniques and defend your group from this rising menace. Secureworks reveals the most recent methods employed by the North Korean menace group NICKEL TAPESTRY.
A latest report by cybersecurity agency Secureworks has uncovered a disturbing however not-so-new tactic employed by North Korean hackers. They’re infiltrating Western firms by posing as legit IT employees, stealing delicate information, after which demanding ransom for its return.
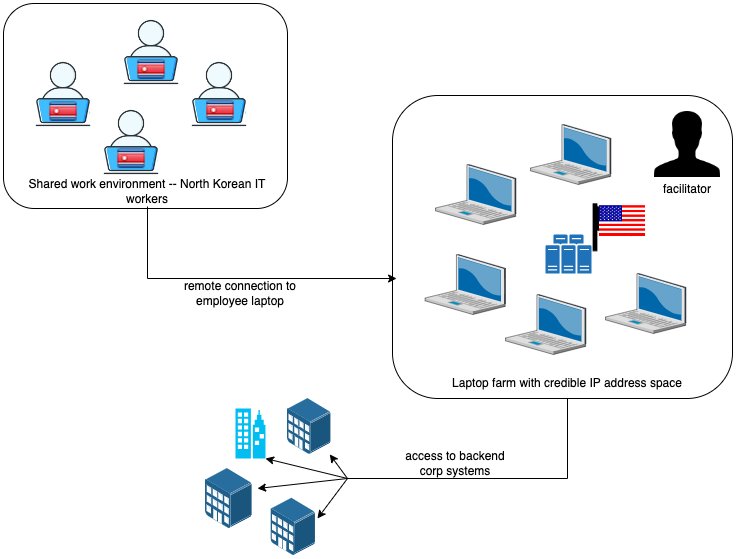
The mastermind behind this scheme is a North Korean hacking group often called Nickel Tapestry. The group operates from “laptop farms,” utilizing stolen or falsified identities to idiot HR departments at firms throughout the US, UK, and Australia. Usually making use of for developer positions, they make the most of quite a lot of techniques to evade and conceal their identities/areas.
As an example, they request adjustments to supply addresses for company laptops, typically rerouting them to laptop computer farms, and typically they categorical a robust desire for utilizing private laptops and digital desktop infrastructure (VDI) setups, a tactic beforehand warned by the FBI. This permits them to remotely entry firm networks with out leaving a hint.
Additionally, they typically exhibit “suspicious financial behaviours” comparable to frequent adjustments to checking account data or using digital cost providers to bypass conventional banking methods.
Moreover, the group makes use of residential proxy addresses and VPNs to masks their precise IP addresses. Additionally they use “Splitcam” software program throughout video calls to simulate video calls, avoiding the necessity to allow their webcams by creating pretend AI clones of themselves.
In a single case, a pretend employee gained entry to an organization’s community, exfiltrated delicate information, after which – after being fired for poor efficiency – demanded a six-figure ransom for its return. This extortion aspect considerably will increase the potential monetary harm brought on by these assaults.
“The emergence of ransom demands marks a notable departure from prior NICKEL TAPESTRY schemes. However, the activity observed prior to the extortion aligns with previous schemes involving North Korean workers,” Secureworks’ Counter Menace Unit analysis crew wrote within the report.
Maybe most annoying is the proof of collaboration between these pretend employees. They could present pretend references for one another, carry out job duties on one another’s behalf, and even talk through e-mail whereas masquerading as totally different people. In a single occasion, researchers consider a single particular person could have adopted a number of personas to additional the rip-off.
You’ve Been Warned!
This IT employee rip-off isn’t new. Related techniques have been noticed since 2018, with fraudulent employees securing positions at Fortune 100 firms and funnelling stolen mental property again to North Korea to doubtlessly fund weapons applications, together with weapons of mass destruction.
In Might 2022, the US authorities warned organizations to watch out for North Korean hackers within the guise of IT freelancers claiming to be non-DPRK (Democratic Individuals’s Republic of Korea) nationals.
In July 2024, North Korean hackers tried one other pretend hiring scheme, this time concentrating on KnowBe4, a outstanding U.S.-based cybersecurity firm. On this case, a hacker posed as an IT employee and managed to safe employment with the corporate. The subsequent step within the assault concerned putting in malware on a company-issued MacBook, desiring to compromise KnowBe4’s methods.
Safety Measures
How can firms defend themselves from this evolving menace? Secureworks recommends thorough background checks and verification of candidate identities. Researchers recommend {that a} candidate’s work traits, comparable to making use of for a full stack developer place, claiming 8-10 years of expertise, and having novice to intermediate English abilities, are the largest crimson flags.
Moreover, uncommon communication hours, various communication kinds, excuses for not enabling cameras throughout interviews, and a name center-like tone ought to set off additional investigation.
RELATED TOPICS
- Feds Bust N. Korean Id Theft Ring Focusing on US Companies
- Hackers used pretend job web site to rip-off jobless US veterans
- Pretend LinkedIn job affords rip-off spreading More_eggs backdoor
- Pretend GitHub Repos Caught Dropping Malware as PoCs AGAIN!
- Worker Duped by AI-Generated CFO in $25.6M Deepfake Rip-off
- Pretend PoC Script Tricked Researchers into Downloading VenomRAT