Lumma Stealer malware makes use of faux CAPTCHA to deceive victims. This information-stealing malware targets delicate knowledge like passwords and cryptocurrency particulars.
The Qualys Menace Analysis Unit (TRU) has found that Lumma Stealer, a malware accessible by way of a Malware-as-a-Service (MaaS) mannequin, has advanced its techniques significantly to deceive customers.
Qualys shared its findings with Hackread.com relating to an lively Lumma Stealer marketing campaign utilizing faux CAPTCHA pages to trick customers into executing a persistent payload. The assault makes use of multi-stage fileless strategies, making it misleading and protracted.
Pretend CAPTCHA Verification
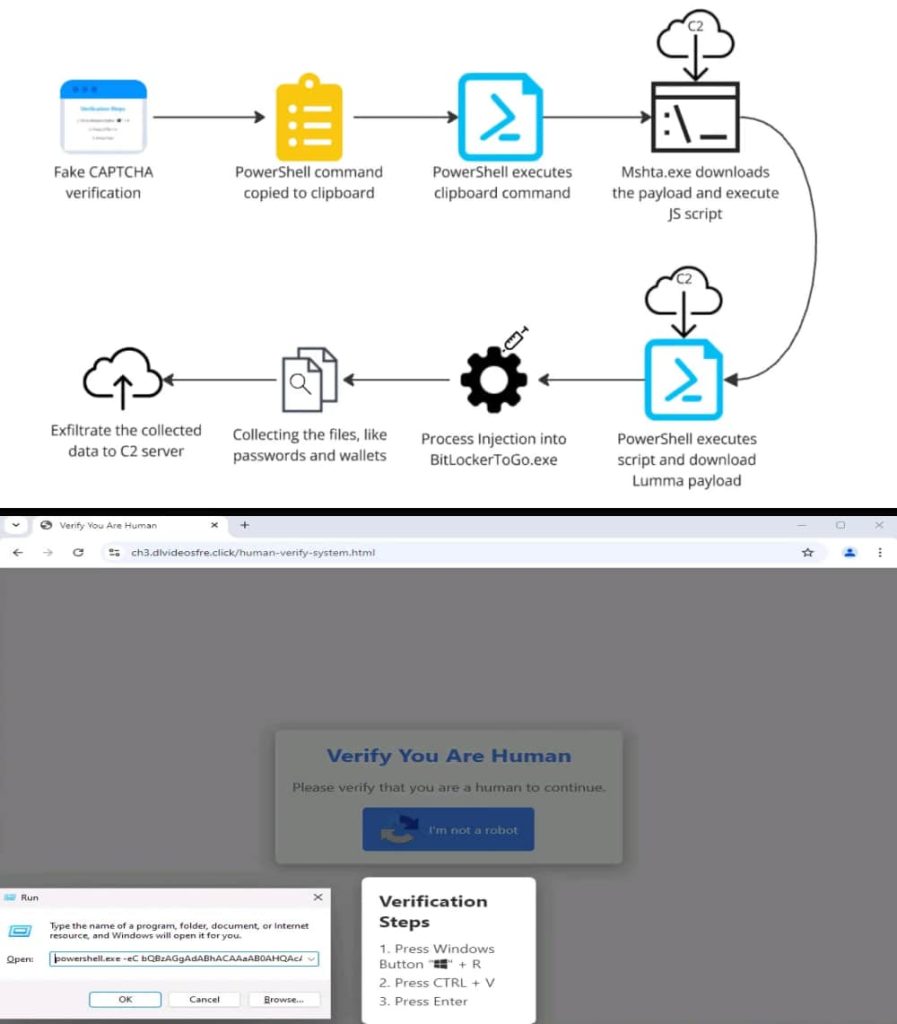
Qualys TRU defined that customers are lured to a faux CAPTCHA verification web page, typically by way of compromised respectable software program or public-facing functions. Clicking the “I’m not a robot” button triggers a malicious PowerShell command, which downloads an preliminary stager (malware downloader) onto the goal machine. The downloaded payload is a crafted PE file with an obfuscated JavaScript code embedded inside it.
What occurs is that clicking the verification button triggers a Base64-encoded PowerShell script obtain. This script leverages the trusted Home windows device “mshta.exe” to obtain a distant payload disguised as a respectable Home windows device named “Dialer.exe.” This downloaded payload is a crafted PE file with an obfuscated JavaScript code embedded inside it.
Curiously, the embedded script makes use of a method referred to as polyglot, the place legitimate HTA content material is hid inside executable recordsdata. When triggered, the script downloads and executes one other obfuscated JavaScript code utilizing PowerShell. This script decrypts a last payload and downloads two archives containing the precise Lumma Stealer executable (Vectirfree.exe).
Data Gathering and Evasion Strategies
Vectirfree.exe employs course of hollowing, a standard malware tactic, to inject its malicious code right into a respectable program like “BitLockerToGo.exe.” The malware drops recordsdata like “Killing.bat” and “Voyuer.pif” within the non permanent listing that checks for and terminates antivirus processes to evade detection.
Within the subsequent stage of the assault, Lumma Stealer searches for delicate recordsdata and knowledge associated to cryptocurrency and passwords. Stolen knowledge is distributed to a command and management (C2) server, sometimes utilizing “.shop” top-level domains, to exfiltrate the stolen knowledge.
Lumma Stealer is a fileless malware that executes instantly from reminiscence with out creating everlasting recordsdata. It targets delicate knowledge like passwords, browser data, and cryptocurrency pockets particulars. By utilizing strategies like polyglot and obfuscated scripts to hinder evaluation, and course of hollowing to cover its malicious exercise inside a respectable course of, the malware presents itself as a persistent menace.
“Our analysis of its infection chain highlighted how the fileless malware exploits common tools like PowerShell and mshta.exe, as well as the critical role of embedded payloads and process injection in its operations,” researchers famous within the report.
By understanding the Lumma Stealer assault course of and implementing sturdy safety measures, organizations can successfully shield themselves towards this evolving menace.
RELATED TOPICS
- Evaluation of High Infostealers: Redline, Vidar and Formbook
- LummaC2 Malware Variant Makes use of Obfuscation to Steal Knowledge
- Pretend League of Legends Obtain Adverts Unfold Lumma Stealer
- Hacked YouTube Channels Unfold Lumma through Cracked Software program
- PDiddySploit Malware Hidden in Information Revealing Deleted Diddy Posts