Trellix analysis exposes the hazards of faux antivirus web sites disguised as professional safety software program however harbouring malware. Discover ways to determine these scams and shield your self from threats like identification theft and ransomware assaults.
Think about looking out on-line for an antivirus program to guard your laptop, solely to bump into an internet site that infects your system with data stealers. That is the misleading tactic employed by pretend antivirus (AV) websites, a rising menace detailed in Trellix’s analysis titled “A Catalog of Hazardous AV Sites – A Tale of Malware Hosting.”
Deception Disguised as Safety
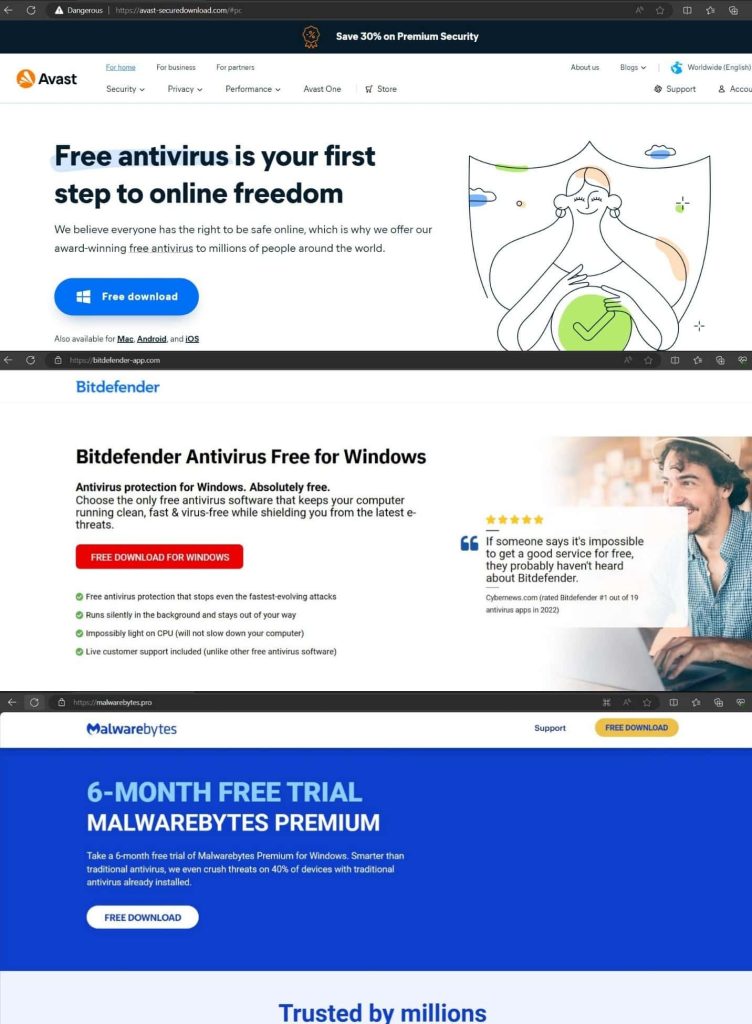
In April 2024, Trellix Superior Analysis Middle workforce members found a number of pretend antivirus websites internet hosting subtle malicious recordsdata like APK, EXE, and Inno setup installers. These websites are used to distribute SpyNote trojan, Lumma malware, and StealC malware. The malware hosts embrace avast-securedownload.com, bitdefender-app.com, and malwarebytes.professional.
Avast-securedownload.com:
It hosts a classy APK known as Avast.apk that delivers SpyNote Trojan, which may set up and delete packages, learn name logs, SMS, contacts, storage knowledge, telephone state, and extra. It additionally has a recorder, contact exercise tracker, and replace capabilities.
Bitdefender-app.com:
This web site delivers a zipper file with an EXE named “setup-win-x86-x64.exe.zip” with a discreet TLS callback operate. It delivers Lumma malware, focusing on delicate data like PC title, username, HWID, display decision, CPU, put in reminiscence, operating course of, login knowledge, historical past, cookies, tokens, and person profile data.
Malwarebytes.professional:
The web site delivers RAR recordsdata containing professional DLLs, Inno Setup, and StealC infostealing malware. The contents are compressed in gzip and transferred to the attacker’s C2 server. The stolen data contains account tokens, Steam tokens, saved card particulars, system profiles, Telegram logins, operating course of names, put in browser lists, and customary system data.
Malicious Binaries
In accordance with Trellix’s weblog submit, researchers additionally found a binary known as AMCoreDat.exe, which facilitates the deployment of stealer malware. The attacker makes use of a classy technique to obfuscate the payload, stealing sufferer data, together with PC title, username, searching historical past, cookies, tokens, and so forth., and sends it to a C2 server.
Doable Risks
Unaware customers, looking for to safeguard their gadgets, get simply tricked into downloading malicious software program disguised as antivirus applications as a result of these websites seem skilled, full with logos, pretend testimonials, and urgency-inducing language about potential threats.
The results of falling sufferer to those scams may be extreme, together with identification theft, monetary loss, delicate knowledge breaches, ransomware assaults and probably hefty ransom calls for.
Researchers suspect these web site addresses are distributed by malicious promoting and search engine marketing poisoning methods. To mitigate dangers, it is strongly recommended to observe safety measures like utilizing robust cybersecurity options, avoiding pirated software program, and verifying software program legitimacy together with your end-point supplier.
RELATED TOPICS
- Malicious Android Apps Masked as Anti-virus Software program
- Pretend In style Software program Advertisements Ship MadMxShell Backdoor
- Pretend Skype, Zoom, Google Meet Websites Unfold A number of RATs
- Hackers steal supply code of prime anti-virus companies to promote on-line
- Pretend LastPass Password Supervisor App Lurks on iOS App Retailer