Introduction To Checkmarx One
As an increasing number of corporations undertake fashionable utility growth methodologies and purpose to “shift-left,” they’re additionally adopting fashionable utility safety testing (AST) instruments and finest practices like integrating and automating AST instruments into their growth pipelines. However are these corporations guaranteeing that they’re checking for the suitable dangers and dealing with high-fidelity outcomes?
Checkmarx, a pacesetter in Gartner’s AppSec Magic Quadrant for 5 consecutive years, understands the wants of recent growth. In an effort to streamline scanning and assist growth groups safe code with out slowing time to market, we launched Checkmarx One™, probably the most complete utility AST platform available on the market. Checkmarx One brings our industry-leading SAST engine (and lots of others resembling SCA, KICS, and so on.) to your AppSec and growth staff by way of the cloud.
Nonetheless, flexibility and speed-to-scan supply are solely a part of the fashionable AppSec equation. Equally, if no more vital, is offering options to the query above—that is the place key Checkmarx One differentiators, presets and queries, make all of the distinction.
Presets And Queries In Checkmarx One
Earlier than we dig into how precisely Checkmarx One’s presets and queries may also help us tackle the problem of checking for applicable dangers and dealing with high-fidelity outcomes, it is very important perceive the fundamentals of each, together with how they’re used within the SAST engine scan course of:
Preset = assortment of vulnerability queries that outline the scope of the SAST scan
Question = vulnerability rule written in CxQL
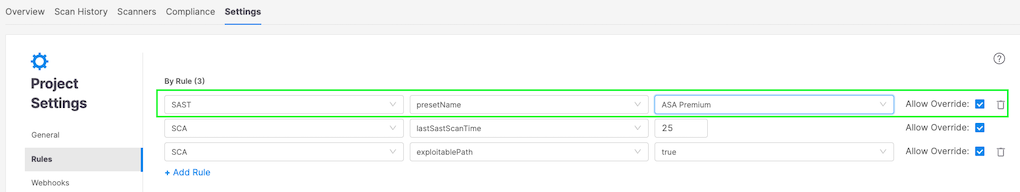
Any SAST engine scan initiated by way of Checkmarx One will need to have a preset outlined on the group, challenge, or scan stage —see under for an instance of a SAST preset being set on challenge creation by way of a presetName rule:
Notice: The total record of predefined presets which are accessible in Checkmarx One might be present in our documentation right here.
Choosing a preset from the drop-down menu, resembling OWASP High 10 – 2021, will restrict that challenge’s scans to solely test for vulnerability queries particular to the highest 10 internet utility safety dangers based on the OWASP (Open Net Utility Safety Mission) compliance pointers for 2021.
After deciding on a preset, every SAST scan typically follows this high-level course of:
- Parse supply code
- Construct AST and DOM
- Construct data-flow graphs (DFG) from code’s supply and sinks
- Execute the scan preset’s queries towards the DFGs
- Return vulnerabilities
As we noticed within the definition supplied for presets, they’re integral to a profitable, actionable SAST scan. Incorrectly setting a scan’s scope may cause scans to run lengthy and inefficiently, however, much more detrimental, have outcomes that present quite a lot of noise and pointless work and confusion to your triaging groups.
Notice: When evaluating AppSec platforms, it is very important confirm that the SAST engine contains some kind of preset performance as many options don’t present one which makes it not possible to restrict consequence “noise.”
Talking of triaging, whereas presets can guarantee the right scan scope, in case your SAST outcomes should not of high-quality and include too many false positives (FP) or false negatives (FN) then your SAST answer runs the chance of turning into ‘shelfware’. That is one other space through which Checkmarx One excels in comparison with competing options, as solely Checkmarx One’s SAST vulnerability queries use a proprietary syntax, CxQL (C# by-product), that permits AppSec groups to simply customise vulnerability queries as wanted to take away false positives and false negatives.
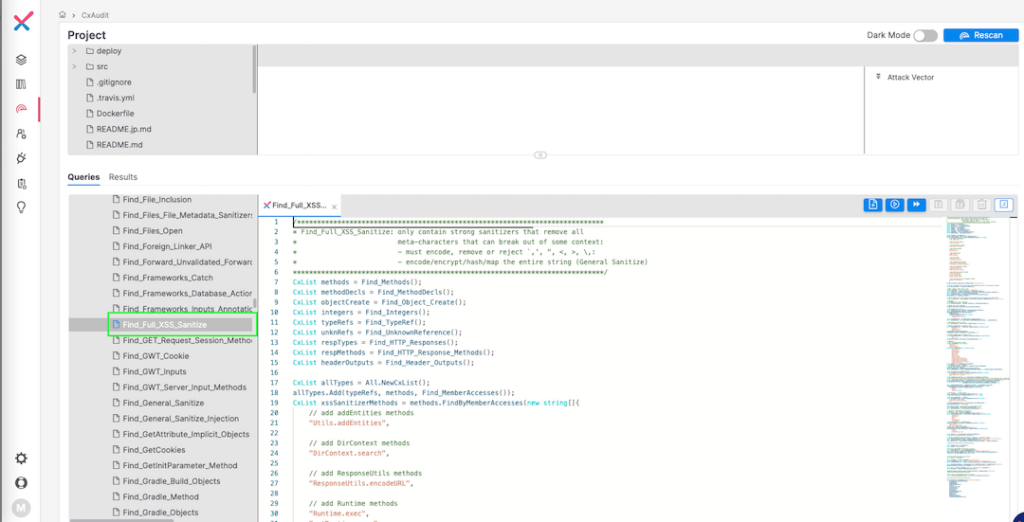
A standard use case that neatly highlights the advantages of customizing queries might be present in cross-site scripting (XSS) vulnerability findings the place a false optimistic could also be occurring attributable to the usage of an in-house sanitizer methodology that’s not included within the Checkmarx One default out-of-the-box question. We will merely add this methodology to the suitable CxQL question and rescan the challenge to take away the FP.
See this screenshot exhibiting the ‘Find_full_XSS_Sanitize’ question by way of Checkmarx One’s CxAudit console:
Now that we perceive the fundamentals and advantages of presets and queries and Checkmarx One, let’s take an in-depth take a look at how we make the most effective use of each.
Preset Choice: Suggestions And Greatest Practices
There are a number of preset choice methods which have proved to achieve success amongst our prospects of all sizes, from SMBs to the biggest Fortune 500 enterprises:
- Solely scan for what might be ‘reasonably remediated’
- Design customized presets based mostly on utility sort and menace modeling
- Begin small and broaden—maturity mannequin strategy
Solely Scan For What Can Be Moderately Remedlated
One of many frequent errors that we see for these each early of their SAST scanning journey and people with mature packages is a misguided however intentional strategy to scanning for all the pieces. A need to get their cash’s value or forestall all doable dangers ends in their preliminary preset alternatives (or lack of choices to decide on a preset with rivals) returning an unworkable quantity of dangers that weighs on all groups concerned. Sadly, this tends to end in main efforts to overview and triage these excessive volumes of findings, just for growth groups to finish up prioritizing and remediating a handful of vulnerabilities.
A greater strategy is to think about what’s most crucial for every challenge/staff to remediate and choose a preset with a scope that permits your groups to moderately tackle and repair these points earlier than the subsequent scan. This may also help forestall frustration at unresolved points and create momentum as groups shut out points.
Choose Presets Primarily based On App Sort And Risk Modeling
Additionally it is extraordinarily vital to make use of your data and understanding of a challenge to decide on presets which make sense based mostly on the applying’s structure and utility sort.
Utility sort can affect the sort of weaknesses an utility could also be prone to. For instance, if there isn’t a front-end internet code within the utility, XSS vulnerabilities, by definition, won’t be current—so it doesn’t make sense to make use of a preset that can attempt to discover XSS weaknesses. Or, if an utility doesn’t talk with a database, SQL injection vulnerabilities won’t be current and don’t should be sought both.
That is the place the usage of predefined presets resembling Android, Apple Safe Coding Information, JSSEC, OWASP Cell High 10 – 2016, OWASP High 10 API, WordPress, and so on. are useful.
Begin Small And Broaden: Maturity Mannequin Method
Beginning small is an effective technique for any buyer, regardless of the scale, useful resource capability, or AppSec maturity. However, it’s notably applicable for growth groups which are new to utility safety testing. Beginning small when deciding on a preset will guarantee groups aren’t overwhelmed or scared away by 1000’s of outcomes. As soon as a staff has sufficiently triaged outcomes discovered with a small, focused preset, the scope of the preset might be widened to search for further sorts of outcomes.
This strategy is most frequently applied by taking a severity-based strategy.
An instance maturity mannequin, using the predefined presets, might seem like the next, with every preset used till all scan findings for that preset are remediated, after which, the challenge advances to make use of the subsequent preset:
- OWASP High 10 – 2021
- Excessive and Medium
- Excessive, Medium, and Low
- ASA Premium
Mission Onboarding: Placing It All Collectively
As famous beforehand, choosing the proper preset is barely half of the battle in offering appropriate and high-fidelity SAST scan outcomes. Every preset features a collection of vulnerability queries, and it’s these queries that in the end determine the dangers inside a scan. The accuracy and robustness of every question is the driving think about whether or not FPs or FNs are current in your SAST scan outcomes and Checkmarx One’s SAST engine is the one AppSec platform with a really versatile question language open to its customers.
We suggest that our prospects, both themselves or using our providers, carry out a course of that we name challenge onboarding first for his or her ‘main business applications’ adopted by decrease precedence functions. Mission onboarding is an optimization course of that features the next:
- Use choice methods to pick out applicable beginning preset
- Carry out preliminary scan
- Triage outcomes to determine TP, FP, and FN
- Modify vulnerability queries to take away any high quality points present in step #3
- Alter/choose new preset if scope adjustment required
- Rescan and repeat course of as vital
This kind of full and dynamic strategy is required because the {industry} adjustments to fashionable utility growth and its push for built-in SAST and different engine scans change into an increasing number of prevalent. Checkmarx One and its SAST engine are one-of-a-kind, and our distinctive use of presets and queries set us aside.
Request A Demo
Attain out to us right this moment to request a demo, or join a Free Trial to see for your self!