SUMMARY
- 30,000 Public Workspaces Uncovered: CloudSEK identifies large information leaks from Postman workspaces.
- Delicate Information at Danger: Leaks embrace API keys, tokens, and administrator credentials.
- Main Platforms Affected: GitHub, Slack, and Salesforce among the many impacted providers.
- Key Causes: Misconfigured entry, plaintext storage, and public sharing of collections.
- Mitigation Steps: Use setting variables, rotate tokens, and undertake secret administration instruments.
On December 23, 2024, CloudSEK’s TRIAD workforce recognized important safety vulnerabilities and dangers from the misuse of Postman Workspaces, a preferred cloud-based API improvement and testing platform.
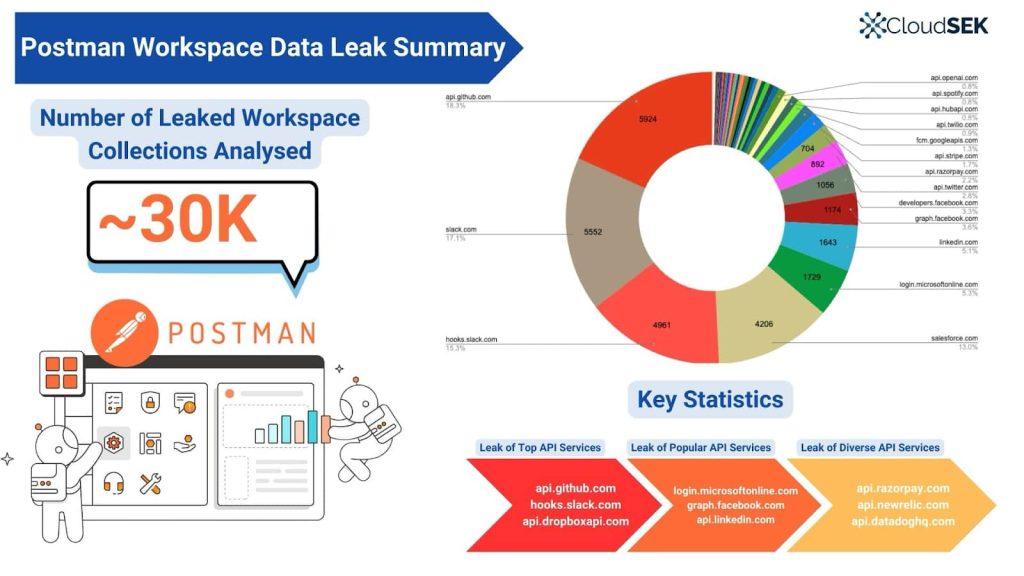
Of their year-long investigation, researchers discovered over 30,000 publicly accessible workspaces leaking delicate details about third-party APIs, together with entry tokens, refresh tokens, and third-party API keys, posing extreme dangers to companies and people alike.
Based on the corporate’s report shared with Hackread.com, leaked information spanned organizations throughout numerous industries, from small companies to giant enterprises, impacting main platforms like GitHub, Slack, and Salesforce. Essential sectors affected included healthcare, athletic attire, and monetary providers, exposing organizations to quite a few threats and safety dangers.
Researchers famous that widespread practices main to those information leaks embrace inadvertent sharing of Postman collections, misconfigured entry controls, syncing with publicly accessible repositories, and storing delicate information in plaintext with out encryption.
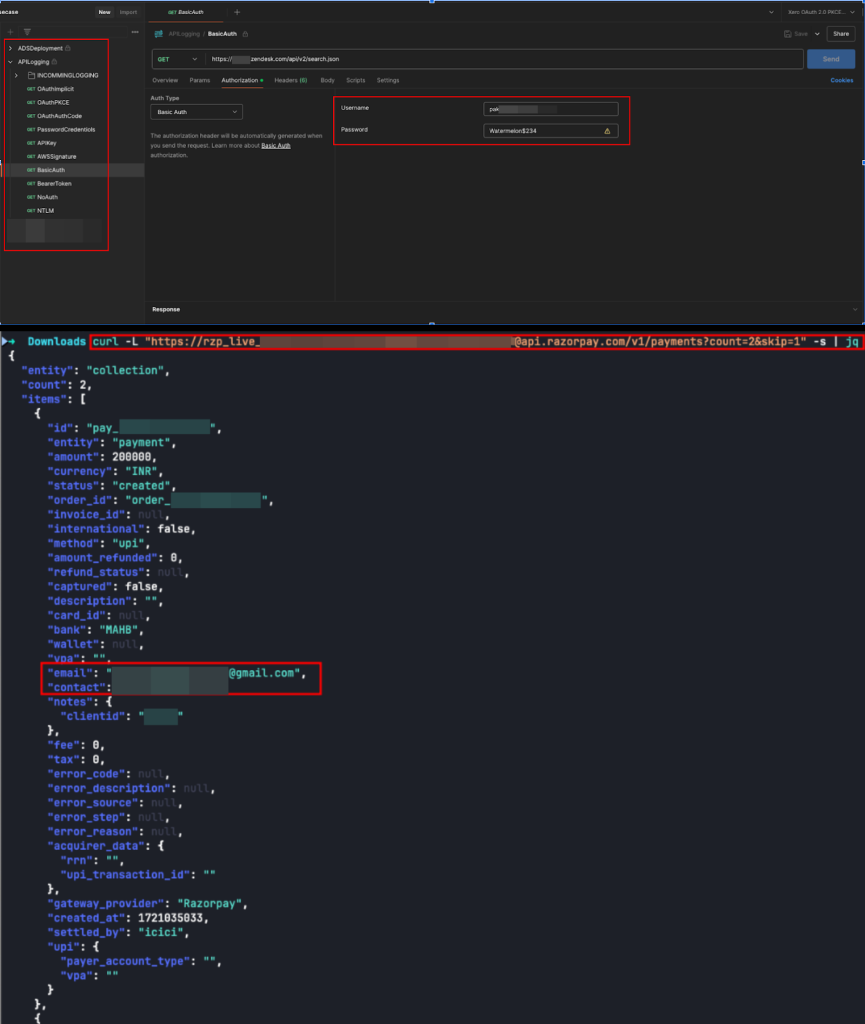
These vulnerabilities can result in extreme penalties. The leaked information, which included administrator credentials, fee processing API keys, and entry to inner programs, can result in monetary and reputational harm for the affected organizations.
Delicate information publicity inside Postman can have vital penalties for each particular person builders and whole organizations. Reportedly, prime API providers like api.github.com, slack.com, and hooks.slack.com have essentially the most uncovered secrets and techniques. Excessive-profile providers like Salesforce.com, login.microsoftonline.com, and graph.fb.com have additionally been uncovered.
A leaked API key or entry token can present attackers with direct entry to important programs and information, probably resulting in information breaches, unauthorized system entry, and elevated phishing and social engineering assaults.
Postman typically shops delicate info like API keys, secrets and techniques, and PII for authentication and communication with APIs. To make sure information security, organizations ought to use setting variables properly, restrict permissions, keep away from long-lived tokens, use exterior secrets and techniques administration, and double-check earlier than sharing any assortment or setting.
CloudSEK responsibly reported most recognized incidents to affected organizations, serving to mitigate dangers. To forestall such exposures, CloudSEK urges organizations to undertake extra dependable safety measures, resembling utilizing setting variables to keep away from hardcoding delicate information, limiting permissions, rotating tokens incessantly, leveraging secrets and techniques administration instruments, and double-checking collections earlier than sharing.
Furthermore, Postman has applied a secret-protection coverage to stop delicate information from being uncovered in public workspaces following the disclosure of those findings. The coverage alerts customers if secrets and techniques are detected, affords resolutions, and facilitates transitions to personal or workforce workspaces.
“Starting this month, we are removing public workspaces with known exposed secrets from the Public API Network. As we roll out this policy change, owners of public workspaces containing secrets will be notified and have the opportunity to remove their exposed secrets before that workspace is removed from the network,” the corporate famous.
RELATED TOPICS
- The Most Widespread API Vulnerabilities
- OwnCloud “graphapi” App Flaw Exposes Delicate Information
- Urlscan.io API Inadvertently Leaked Delicate Information and URLs
- Automotive Business Uncovered to Have Main API Vulnerabilities
- Thousands and thousands impacted as fee API flaws uncovered transaction keys