The malicious PoorTry kernel-mode Home windows driver utilized by a number of ransomware gangs to show off Endpoint Detection and Response (EDR) options has developed into an EDR wiper, deleting information essential for the operation of safety options and making restoration more durable.
Although Pattern Micro had warned about this performance added on Poortry since Might 2023, Sophos has now confirmed seeing the EDR wiping assaults within the wild.
This evolution of PoorTry from an EDR deactivator to an EDR wiper represents a really aggressive shift in ways by ransomware actors, who now prioritize a extra disruptive setup part to make sure higher outcomes within the encryption stage.
PoorTry, also referred to as ‘BurntCigar,’ was developed in 2021 as a kernel-mode driver to disable EDR and different safety software program.
The package, utilized by a number of ransomware gangs, together with BlackCat, Cuba, and LockBit, first gained consideration when its builders discovered methods to get their malicious drivers signed by means of Microsoft’s attestation signing course of. Different cybercrime teams, reminiscent of Scattered Spider, had been additionally seen using the instrument in breaches centered on credential theft and SIM-swapping assaults.
All through 2022 and 2023, Poortry continued to evolve, optimizing its code and utilizing obfuscation instruments like VMProtect, Themida, and ASMGuard to pack the motive force and its loader (Stonestop) for evasion.
Evolution to a wiper
The newest report by Sophos relies on a RansomHub assault in July 2024 that employed Poortry to delete crucial executable information (EXEs), dynamic hyperlink libraries (DLLs), and different important elements of safety software program.
This ensures that EDR software program can’t be recovered or restarted by defenders, leaving the system fully unprotected within the following encryption part of the assault.
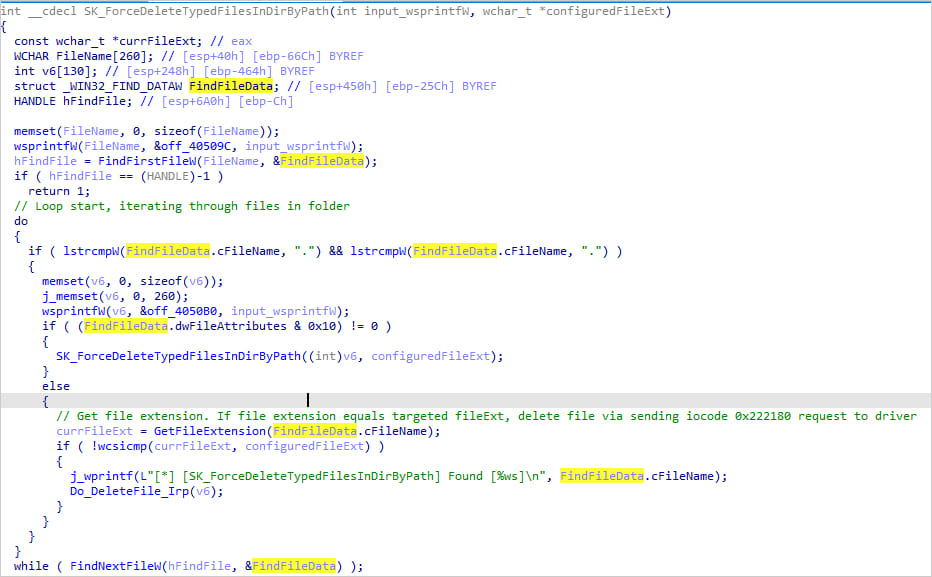
The method begins with the user-mode element of PoorTry, figuring out the safety software program’s set up directories and the crucial information inside these directories.
It then sends requests to the kernel-mode element to systematically terminate security-related processes after which delete their essential information.
Paths to these information are hardcoded onto PoorTry, whereas the user-mode element helps deletion both by file identify or kind, giving it some operational flexibility to cowl a broader vary of EDR merchandise.
supply: Sophos
The malware will be fine-tuned solely to delete information essential to the EDR’s operation, avoiding pointless noise within the dangerous first phases of the assault.
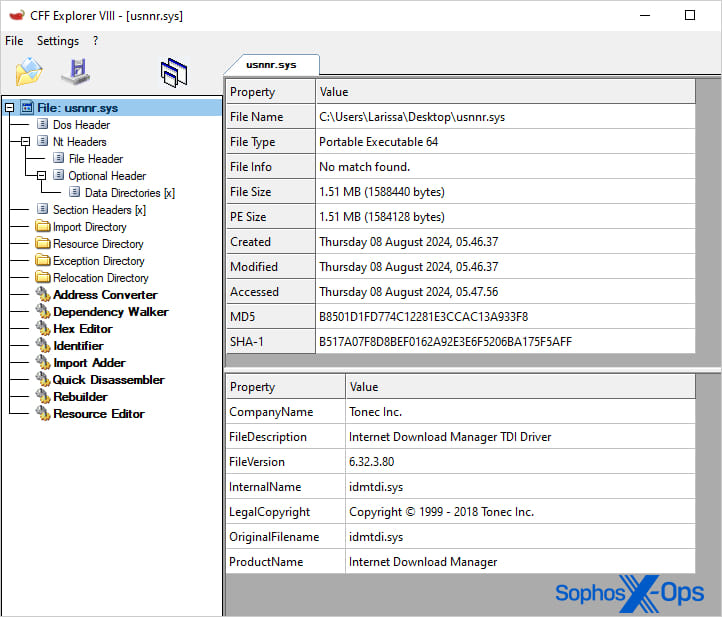
Sophos additionally notes that the most recent Poortry variants make use of signature timestamp manipulation to bypass safety checks on Home windows and use the metadata from different software program like Web Obtain Supervisor by Tonec Inc.
supply: Sophos
The attackers had been seen using a tactic referred to as “certificate roullete,” the place they deploy a number of variants of the identical payload signed with completely different certificates to extend their probabilities that a minimum of one will execute efficiently.
supply: Sophos
Regardless of efforts to trace PoorTry’s evolution and cease its effectiveness, the builders of the instrument have proven a outstanding capacity to adapt to new protection measures.
The EDR wiping performance provides the instrument an edge over defenders responding to assaults however might additionally present new alternatives for detecting the assaults within the pre-encryption part.
