Roughly 9 p.c of examined firmware pictures use non-production cryptographic keys which are publicly identified or leaked in knowledge breaches, leaving many Safe Boot units weak to UEFI bootkit malware assaults.
Referred to as ‘PKfail,’ and now tracked as CVE-2024-8105, the availability chain assault is attributable to take a look at Safe Boot grasp key (Platform Key “PK”), which pc distributors had been supposed to exchange with their very own securely generated keys.
Although these keys had been marked as “DO NOT TRUST,” they had been nonetheless utilized by quite a few pc producers, together with Acer, Dell, Fujitsu, Gigabyte, HP, Intel, Lenovo, Phoenix, and Supermicro.
The problem was found by Binarly in late July 2024, which warned about using untrusted take a look at keys, many already leaked on GitHub and different places, on over eight hundred shopper and enterprise system fashions.
PKfail might enable menace actors to bypass Safe Boot protections and plant undetectable UEFI malware on weak methods, leaving customers no solution to defend and even uncover the compromise.
PKfail impression and response
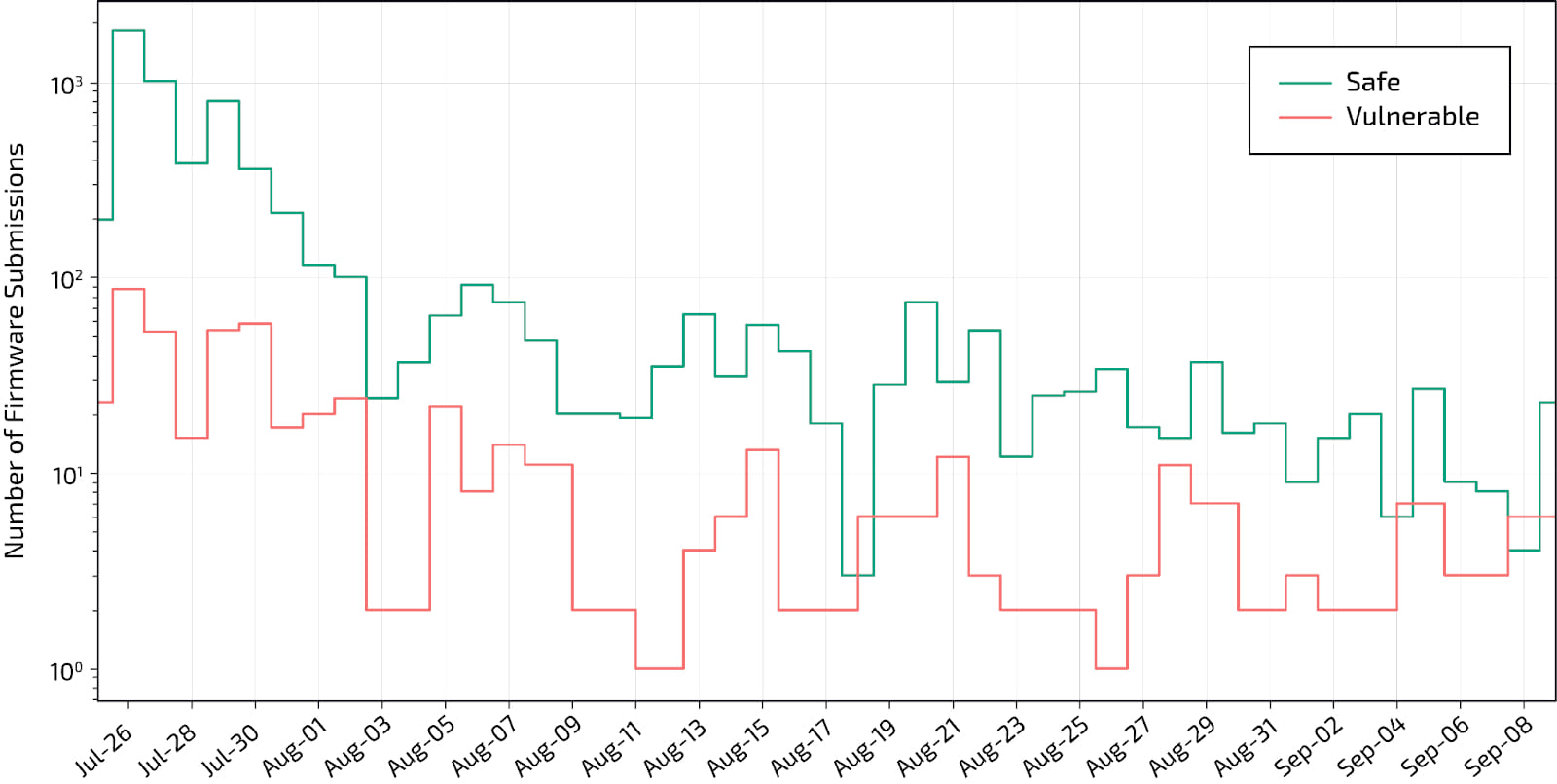
As a part of their analysis, Binarly launched a “PKfail scanner,” which distributors can use to add their firmware pictures to see in the event that they’re utilizing a take a look at key.
Since its launch, the scanner has discovered 791 weak firmware submissions out of 10,095, in accordance with the newest metrics.
“Based on our data, we found PKfail and non-production keys on medical devices, desktops, laptops, gaming consoles, enterprise servers, ATMs, POS terminals, and some weird places like voting machines.” reads the new report by Binarly.
The vast majority of the weak submissions are keys from AMI (American Megatrends Inc.), adopted by Insyde (61), Phoenix (4), and one submission from Supermicro.
Supply: Binarly
For the Insyde keys, which had been generated in 2011, Binarly says that the firmware picture submissions reveal they’re nonetheless utilized in trendy units. Beforehand, it was assumed that they had been solely to be present in legacy methods.
The group has additionally confirmed that PKfail impacts specialised units from Hardkernel, Beelink, and Minisforum, so the flaw’s impression is broader than first estimated.
Binarly feedback that vendor response to PKfail has typically been proactive and swift, although not everybody rapidly revealed advisories in regards to the safety threat. Bulletins on PKfail are presently accessible by Dell, Fujitsu, Supermicro, Gigabyte, Intel, and Phoenix.
A number of distributors have already launched patches or firmware updates to take away weak Platform Keys or exchange them with production-ready cryptographic supplies, and customers can get these by updating their BIOS.
In case your system is now not supported and is unlikely to obtain safety updates for PKfail, it’s endorsed that bodily entry to it’s restricted and that it’s remoted from extra essential components of the community.
