Pig Butchering rip-off targets crypto customers with faux buying and selling apps on Apple and Google Play Shops. Disguised as professional platforms, these apps defraud traders, bypassing retailer checks and exploiting unsuspecting customers globally.
A fraud marketing campaign focusing on Apple iOS and Android customers has been found by GroupIB, involving faux buying and selling apps. These apps, discovered on Apple’s App Retailer and Google Play, and on phishing websites, are a part of a Pig Butchering rip-off focusing on cryptocurrency traders in Asia-Pacific, Center East & Africa, and European areas.
Group-IB’s Menace Intelligence, and Fraud Safety analysts first found these faux cell functions in Could 2024 and have been investigating the marketing campaign ever since.
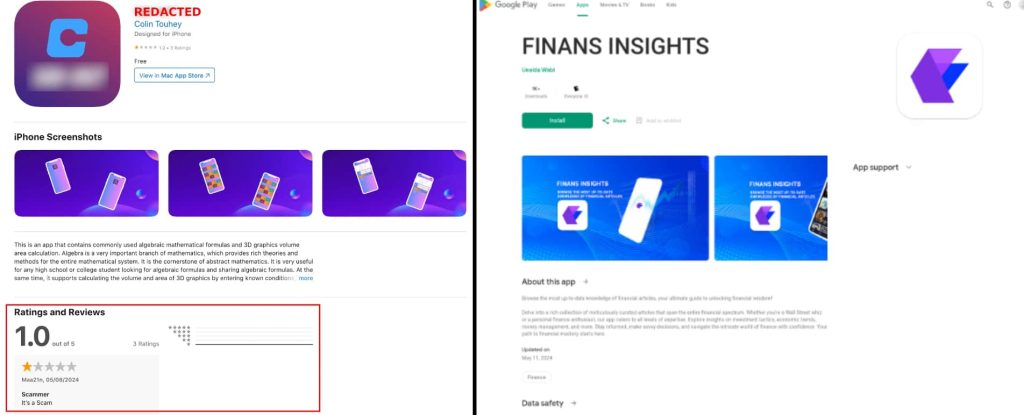
In response to their report shared with Hackread.com forward of publishing on Wednesday, these functions had been developed for Android utilizing a single cross-platform framework. One was distributed via the Google Play retailer, whereas one other focused iOS gadgets.
What’s worse, in contrast to conventional cell trojans, these functions had no typical malicious options and cybercriminals have created a facade of a professional buying and selling platform to defraud victims.
The fraudulent apps verify the present date and time to bypass Apple’s App Retailer checks, launching a faux exercise with mathematical formulation and graphics whether it is sooner than 22 July 2024, 00:00:00. Android samples had been designed to show a fraudulent buying and selling software hosted on the api.fxbrokerscc area, half of a bigger fraudulent infrastructure.
In response to researchers, these faux buying and selling apps and downloader apps mimic professional platforms and should embody options like account settings, transaction historical past, and inventory data. Downloader apps, discovered within the Apple App Retailer or distributed via phishing web sites, immediate victims to put in the fraudulent app.
The malware household used within the pig butchering rip-off is UniShadowTrade, categorised below the UniApp Framework. This identify is given by Group-IB analysts to categorize the fraudulent functions concerned within the rip-off. To your data, the UniApp framework allows builders to create cross-platform functions with a single codebase, making it simpler for scammers to develop and distribute malware.
What Precisely is Pig Butchering?
To your data, Pig butchering is a infamous digital rip-off that entails a meticulous strategy of grooming victims, constructing belief, and in the end defrauding them of their cash.
This specific marketing campaign follows a selected sample: goal identification via social media, grooming and trust-building via social engineering methods, providing a seemingly profitable funding alternative in cryptocurrency or different investments, encouraging a small preliminary funding, and constructing confidence via small earnings.
Scammers strain victims into making massive investments, switch funds they can not withdraw, and disappear. This course of continues till the sufferer is unable to withdraw the funds, inflicting important monetary loss and affecting their monetary stability.
However, scams Pig butchering can have devastating penalties for victims. Understanding scammers’ techniques and taking proactive measures can scale back the danger of falling sufferer to such fraud.
Alert for Android and iOS customers
It’s a proven fact that Google, which owns Android, and Apple, which owns the iOS App Retailer, attempt their greatest to maintain {the marketplace} protected from malware and different cybersecurity threats. Regardless of fixed monitoring, cybercriminals typically slip into these shops with malicious apps, draining the financial institution accounts and crypto wallets of unsuspecting customers.
Simply final week, Google accepted a crypto drainer app on the Play Retailer that stole over $70,000 from Android customers. Alternatively, in February 2024, Apple accepted a faux LastPass Password Supervisor app on its iOS App Retailer. The identical month, Apple accepted a faux Rabby Pockets app that stole thousands and thousands from unsuspecting customers.
Subsequently, be further cautious when downloading an app from any of those shops. Examine their evaluations, seek for the official app on Google, discover their social media platforms, and make sure whether or not the app marketed on app shops is professional or not.
RELATED TOPICS
- Phishing Rip-off Hits European Financial institution Customers on iOS and Android
- Scylla Advert Fraud on iOS, Android Customers Halted by Apple, Google
- Pink Drainer Posed as Journalists, Stole $3M from Twitter Customers
- Hackers Posed as Google Assist to Steal $243 Million in Crypto
- Apple mistakenly accepted malware masked as Adobe Flash Participant