Pretend buying and selling apps on Google Play and Apple’s App Retailer lure victims into “pig butchering” scams which have a worldwide attain.
The apps have been faraway from the official Android and iOS shops after accumulating a number of thousand downloads, say researcher at cybersecurity firm Group-IB, who found the fraud.
Pig butchering is the identify of a rip-off the place the sufferer is led to imagine they’re getting excessive funding returns on a pretend buying and selling platform that shows fabricated info. Fraudsters use social engineering to maintain the sufferer depositing funds and stop them from withdrawing the displayed “profit.”
The rip-off is revealed when the sufferer makes an attempt to money their cash, which the fraudsters have already moved to their accounts.
Fraudulent apps in iOS and Android shops
The fraudulent apps, which Group-IB categorizes beneath the “UniShadowTrade” malware household, are constructed utilizing the UniApp framework and had been first noticed in Could.
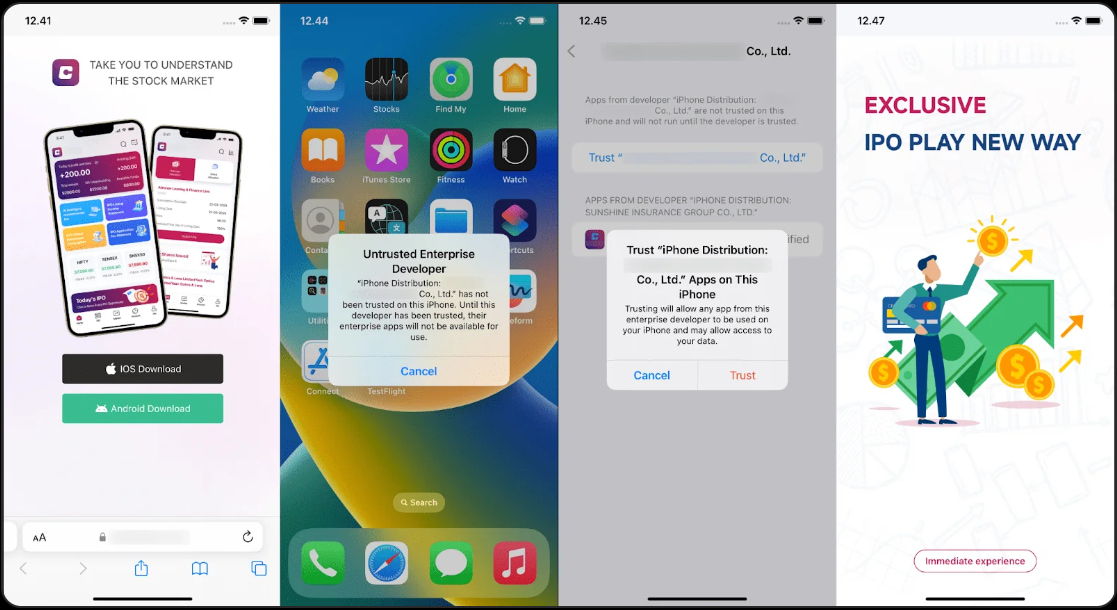
Supply: Group-IB
Their names are SBI-INT (iOS), Finans Insights (Android), Finans Trader6 (Android) and a take a look at the obtain counter for the final two exhibits that they had been downloaded 5,000 instances.
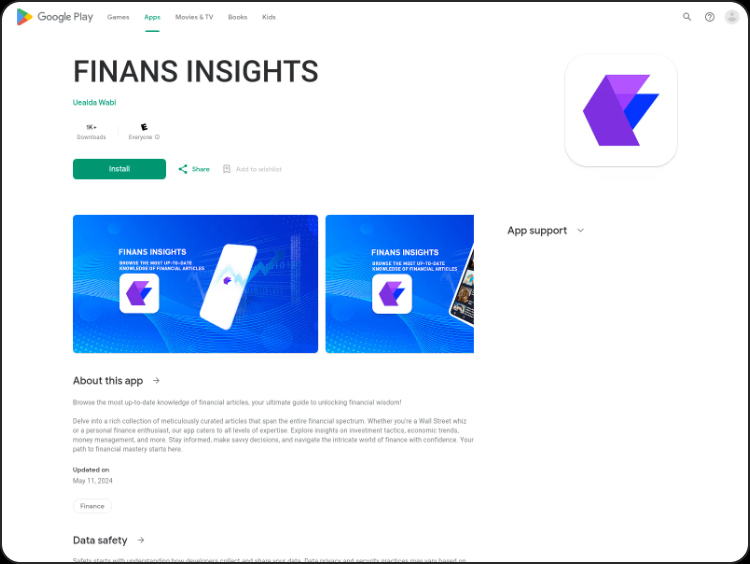
Supply: Group-IB
Group-IB additionally warns that the UniShadow Commerce apps can mimick a wide range of respectable cryptocurrency and buying and selling platforms, offering the next in depth checklist with potential names that might be utilized in impersonation makes an attempt.
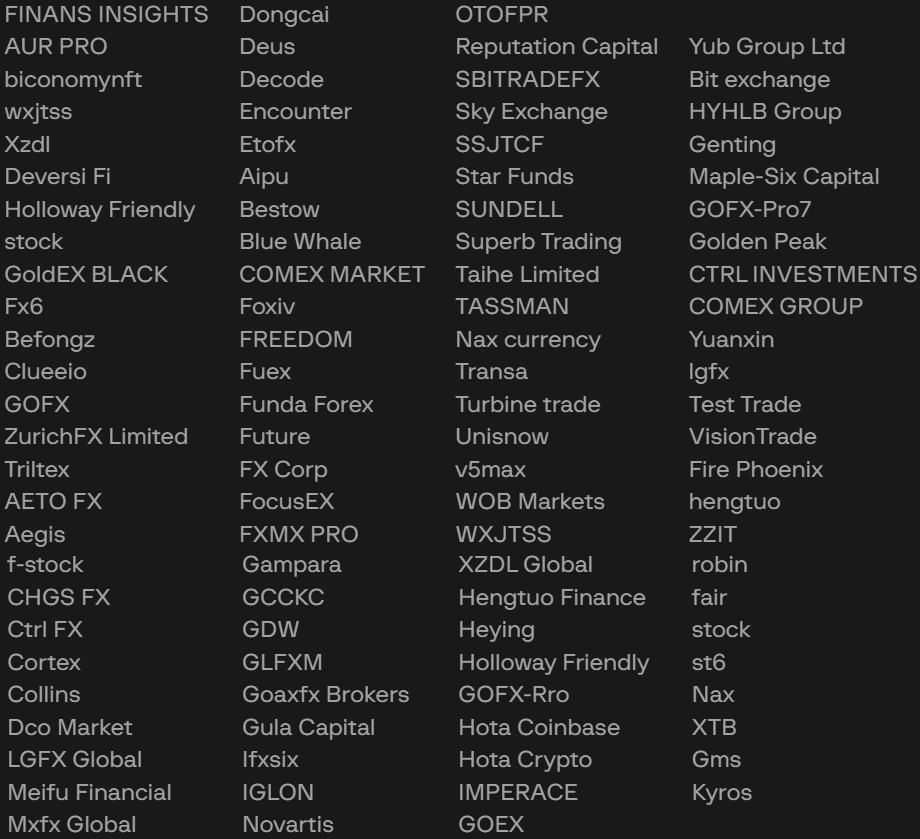
Supply: Group-IB
The researchers report that the apps had been disguised as instruments for “algebraic mathematical formulas and 3D graphics volume area calculations” on iOS, and as monetary information feed aggregators on Android
Nonetheless, after set up they redirected victims to pretend buying and selling platforms accessible solely through invitation codes.
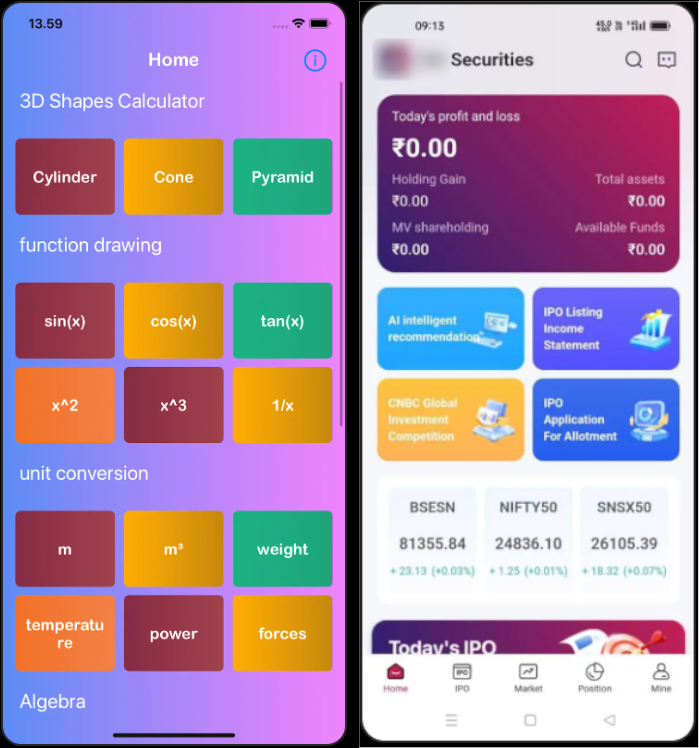
Supply: Group-IB
In keeping with the researchers, the fraudsters groomed their victims in conversations over courting apps and used social engineering to realize their belief.
The apps requested that customers uploaded a number of paperwork, equivalent to nationwide IDs and passports, each so as to add legitimacy to the funding course of and in addition to additional empower the risk actors with delicate info theft.

Supply: Group-IB
After the elimination of the fraudulent apps from the app shops in June, the risk actors moved the distribution operation to phishing web sites, displaying no indicators of stopping.
To remain clear from fraudulent funding schemes, it is strongly recommended to perform a little research earlier than deciding to work with an funding platform, equivalent to checking the background and historical past (monetary data, previous efficiency, status), or whether it is regulated by a regionally or globally-recognized authority.
Customers ought to at the least be cautious of unsolicited messages and URLs promising excessive funding returns, since scams are sometimes promoted this fashion.
