Lately, Sysdig printed a weblog submit concerning the methods companies can harden their LLM-based AI functions utilizing the OWASP Prime 10 for Massive Language Fashions. So why are we writing about MITRE ATLAS, and the way is that this any totally different from the OWASP Prime 10 for LLMs?
The well-known MITRE ATT&CK challenge is a globally-accessible data base of adversarial ways, strategies, and procedures (TTPs) primarily based on real-world cybersecurity observations. ATLAS is without doubt one of the many matrices managed by the group at MITRE. ATLAS is definitely an acronym which stands for Adversarial Threat Landscape for Artificial-Intelligence Systems. Like MITRE ATT&CK, this can be a globally accessible, residing data base of adversarial TTPs particular to Al-enabled methods, once more, primarily based on real-world assault observations and practical demonstrations from Al pink teaming and safety group exercise.
How does this differ from OWASP Prime 10 for LLMs
Sysdig’s Study Cloud Native web page states that the OWASP Prime 10 challenge is designed as “a prioritized list of the most common threats that should be addressed by developers, data scientists, and security experts who have now been tasked with designing and building applications and plugins which leverage LLM-based AI technologies.” That is nice when imposing greatest practices from the start of software improvement to enhance safety posture and in the end cut back the blast radius related to insecure AI net functions.
Although understanding the assorted real-world adversary behaviors in MITRE ATLAS also can assist in mitigation pathways, it’s most frequently used to allow post-incident risk assessments and different inside pink teaming actions — context the OWASP Prime 10 challenge doesn’t embrace. For instance, as a part of your risk detection and response technique, you’ll be able to create Falco guidelines in Sysdig for “unsecured credentials.” Based on the MITRE ATLAS challenge, the ATLAS Method ID AML.T0055 is matched with the prevailing MITRE ATT&CK Reference ID T1552.
<sturdy>- rule:</sturdy> Discover AWS Credentials
<sturdy> desc:</sturdy> >
Detects makes an attempt to look for personal keys or passwords utilizing the grep or discover command.
<sturdy> situation:</sturdy> >
spawned_process
and ((grep_commands and private_aws_credentials) or
(proc.identify = "find" and proc.args endswith ".aws/credentials"))
<sturdy> output:</sturdy> Detected AWS credentials search exercise (proc_pcmdline=%proc.pcmdline)
<sturdy> precedence:</sturdy> WARNING
<sturdy>tags:</sturdy> [maturity_stable, mitre_credential_access, unsecured_credentials, T1552, <strong>AML.T0055</strong>]Code language: Perl (perl)ATLAS Matrix
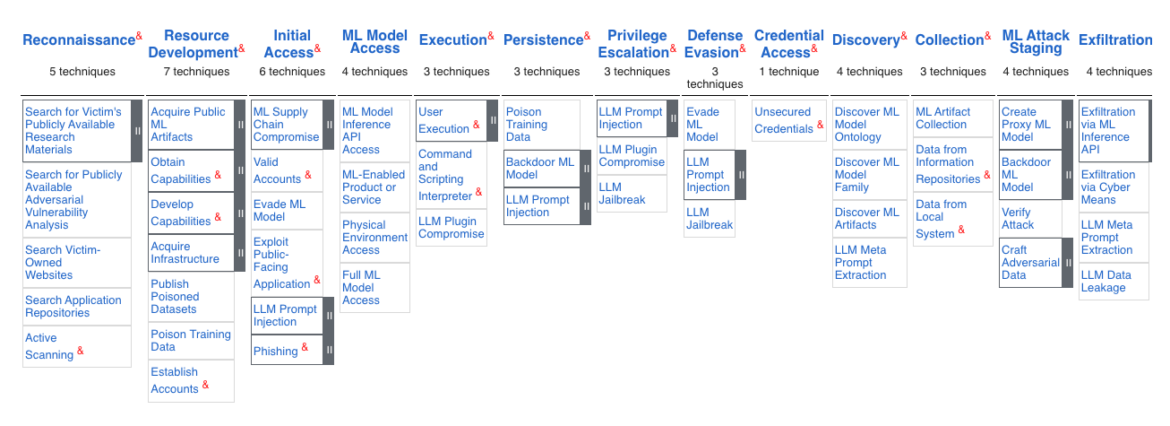
Like different acquainted ATT&CK matrices, the ATLAS matrix exhibits the development of the assault kill chain from left to proper. Normally beginning with Reconnaissance (environmental discovery) and ending with Exfiltration (stealing of delicate PII information) from the group. Since AI workloads differ from conventional net functions, there are new Tactic columns comparable to ML Mannequin Entry and ML Assault Staging which don’t apply to different ATT&CK matrices.
Companies can view the ATLAS matrix highlighted alongside the related Enterprise ATT&CK strategies through the ATLAS Navigator. The ATLAS Navigator will help organizations higher scope their current Linux or Home windows runtime detection guidelines across the uniquely-scoped context of AI workload threats. Additionally, by aligning current detection guidelines with a preferred open-source challenge like MITRE, safety groups can higher enhance risk mitigation with community-contributed insights, whereas additionally eradicating the bias related to distinctive findings from proprietary software program options.
Conclusion
The Sysdig Risk Analysis Group is continually updating the managed Falco Feeds with rule tags to make sure the cloud, Kubernetes and AI workloads are compliant with evolving regulatory necessities. Falco and the Sysdig agent enable customers to add customized labels to handle compliance requirements that could be distinctive to your group, whereas additionally offering the choice of receiving automated rule updates with tags that apply to ways and strategies throughout your complete MITRE ATT&CK framework in addition to safety compliance controls comparable to PCI DSS, NIST, GDPR, DORA, FedRAMP and extra.