Over 660,000 uncovered Rsync servers are doubtlessly weak to 6 new vulnerabilities, together with a critical-severity heap-buffer overflow flaw that enables distant code execution on servers.
Rsync is an open-source file synchronization and information transferring instrument valued for its skill to carry out incremental transfers, lowering information switch instances and bandwidth utilization.
It helps native file techniques transfers, distant transfers over safe protocols like SSH, and direct file syncing by way of its personal daemon.
The instrument is utilized extensively by backup techniques like Rclone, DeltaCopy, ChronoSync, public file distribution repositories, and cloud and server administration operations.
The Rsync flaws have been found by Google Cloud and unbiased safety researchers and will be mixed to create highly effective exploitation chains that result in distant system compromise.
“In the most severe CVE, an attacker only requires anonymous read access to a rsync server, such as a public mirror, to execute arbitrary code on the machine the server is running on,” reads the bulletin printed on Openwall.
The six flaws are summarized beneath:
- Heap Buffer Overflow (CVE-2024-12084): Vulnerability arising from improper dealing with of checksum lengths within the Rsync daemon, resulting in out-of-bounds writes within the buffer. It impacts variations 3.2.7 via < 3.4.0 and might allow arbitrary code execution. Mitigation includes compiling with particular flags to disable SHA256 and SHA512 digest assist. (CVSS rating: 9.8)
- Data Leak by way of Uninitialized Stack (CVE-2024-12085): Flaw permitting the leakage of uninitialized stack information when evaluating file checksums. Attackers can manipulate checksum lengths to take advantage of this vulnerability. It impacts all variations beneath 3.4.0, with mitigation achievable by compiling with the -ftrivial-auto-var-init=zero flag to initialize stack contents. (CVSS rating: 7.5)
- Server Leaks Arbitrary Consumer Recordsdata (CVE-2024-12086): Vulnerability permitting a malicious server to enumerate and reconstruct arbitrary shopper recordsdata byte-by-byte utilizing manipulated checksum values throughout file switch. All variations beneath 3.4.0 are affected. (CVSS rating: 6.1)
- Path Traversal by way of –inc-recursive Possibility (CVE-2024-12087): Subject that stems from insufficient symlink verification when utilizing the –inc-recursive possibility. Malicious servers can write recordsdata exterior the meant directories on the shopper. All variations beneath 3.4.0 are weak. (CVSS rating: 6.5)
- Bypass of –safe-links Possibility (CVE-2024-12088): Flaw which happens when Rsync fails to correctly confirm symbolic hyperlink locations containing different hyperlinks. It leads to path traversal and arbitrary file writes exterior designated directories. All variations beneath 3.4.0 are impacted. (CVSS rating: 6.5)
- Symbolic Hyperlink Race Situation (CVE-2024-12747): Vulnerability arising from a race situation in dealing with symbolic hyperlinks. Exploitation could enable attackers to entry delicate recordsdata and escalate privileges. All variations beneath 3.4.0 are affected. (CVSS rating: 5.6)
The CERT Coordination Middle (CERT/CC) issued a bulletin warning concerning the Rsync flaws, marking Crimson Hat, Arch, Gentoo, Ubuntu NixOS, AlmaLinux OS Basis, and the Triton Information Middle as impacted.
Nevertheless, many extra doubtlessly impacted tasks and distributors haven’t responded but.
“When combined, the first two vulnerabilities (heap buffer overflow and information leak) allow a client to execute arbitrary code on a device that has an Rsync server running,” warned CERT/CC.
“The client requires only anonymous read-access to the server, such as public mirrors. Additionally, attackers can take control of a malicious server and read/write arbitrary files of any connected client. Sensitive data, such as SSH keys, can be extracted, and malicious code can be executed by overwriting files such as ~/.bashrc or ~/.popt.”
In its personal bulletin about CVE-2024-12084, RedHat famous that there are not any sensible mitigations, and the flaw is exploitable in Rsync’s default configuration.
“Keep in mind that rsync’s default rsyncd configuration allows anonymous file syncing, which is at risk of this vulnerability,” explains RedHat.
“Otherwise, an attacker will need valid credentials for servers which require authentication.”
All customers are suggested to improve to improve to model 3.4.0 as quickly as potential.
Widespread impression
A Shodan search performed by BleepingComputer reveals that there are over 660,000 IP addresses with uncovered Rsync servers.
Most IP addresses are positioned in China, with 521,000 uncovered, adopted by the US, Hong Kong, Korea, and Germany in a lot smaller numbers.
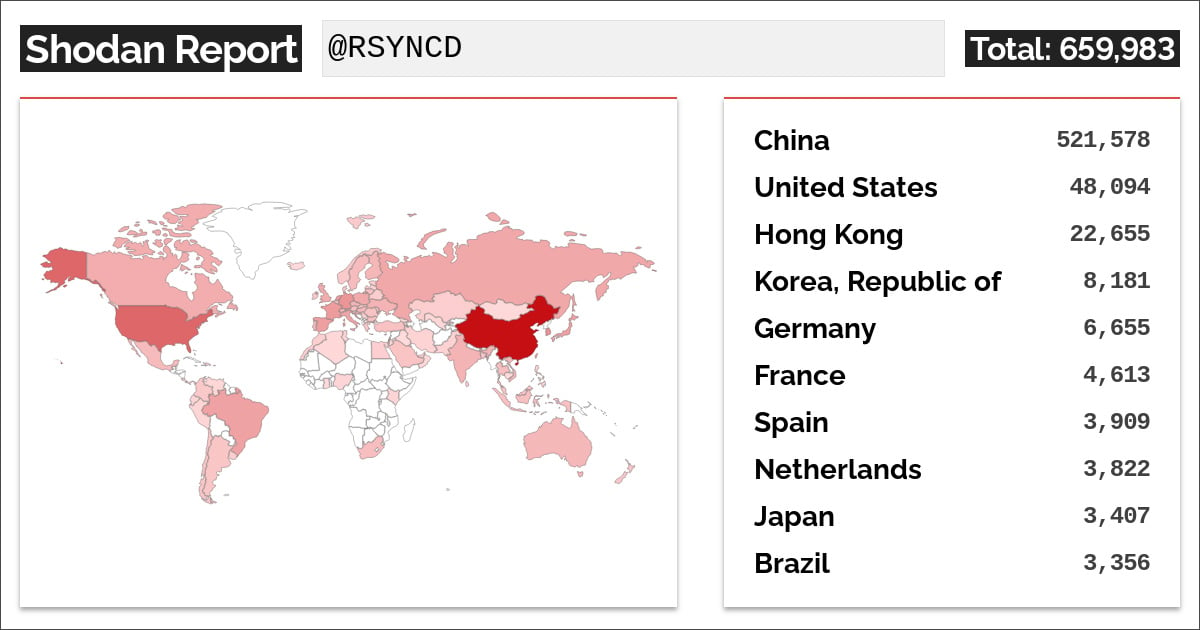
Of those uncovered Rsync servers, 306,517 are operating on the default TCP port 873 and 21,239 are listening on port 8873, generally used for Rsync over SSH tunneling.
Binary Edge additionally reveals a lot of uncovered Rsync servers, however their numbers are decrease, at 424,087.
Whereas there are various uncovered servers, it’s unclear if they’re weak to the newly disclosed vulnerabilities because the attackers would want legitimate credentials or the server should be configured for nameless connections, which we didn’t check.
All Rsync customers are strongly suggested to improve to model 3.4.0 or configure the daemon to require credentials.
For these unable to improve now, you may also block TCP port 873 on the perimeter so servers are usually not remotely accessible.
