Over 4,000 deserted however nonetheless lively internet backdoors had been hijacked and their communication infrastructure sinkholed after researchers registered expired domains used for commanding them.
A few of the dwell malware (internet shells) was deployed on internet servers of high-profile targets, together with authorities and college programs, able to execute instructions from anybody who device management of the communication domains.
Along with The Shadowserver Basis, researchers at offensive safety outfit WatchTowr Labs prevented these domains and the corresponding victims from falling into the arms of malicious actors.
Discovering hundreds of breached programs
Backdoors are malicious instruments or code planted on a compromised system to permit unauthorized distant entry and management. Risk actors usually use them for persistent entry and to execute on the compromised system instructions that might additional the assault.
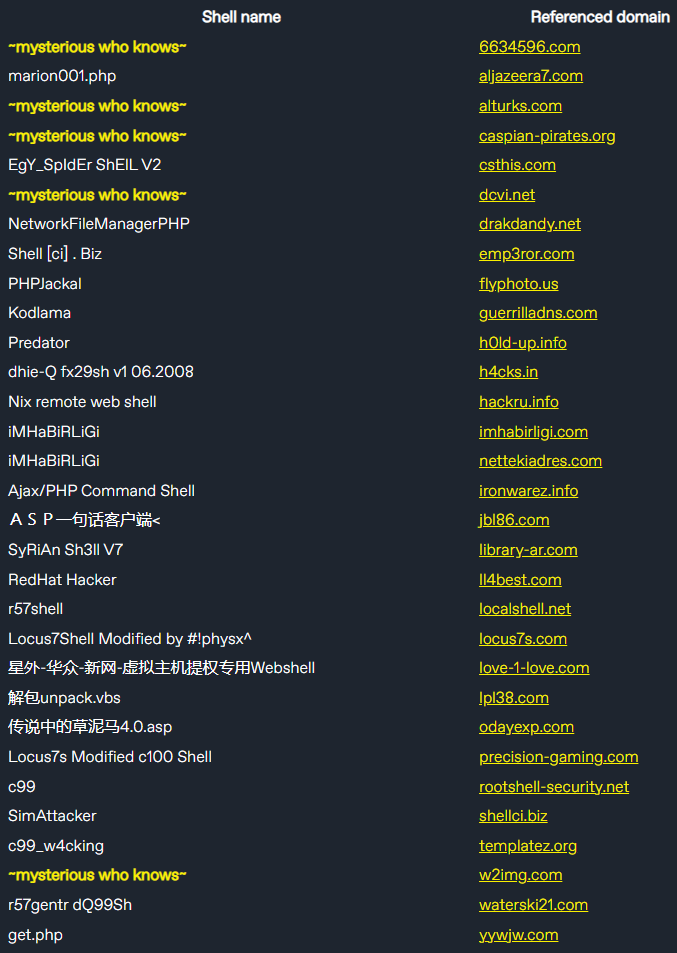
WatchTowr researchers began looking for domains in varied internet shells and bought any that had expired, primarily taking management of the backdoors.
After establishing a logging system, the deserted however nonetheless lively malware began sending requests that allowed the researchers to establish at the very least a few of the victims.
From registering greater than 40 domains, the researchers obtained communication from over 4,000 compromised programs making an attempt to “phone home.”
Supply: WatchTowr
The researchers discovered a number of backdoor varieties, together with the “classic” r57shell, the extra superior c99shell, which presents file administration and brute-forcing capabilities, and the ‘China Chopper’ internet shell that’s typically linked to APT teams.
The report even mentions one backdoor that showcased habits related to the Lazarus Group, though it later clarifies that it was doubtless a reuse of the menace actor’s device by others.
Among the many diverse set of breached machines, WatchTowr discovered a number of programs inside China’s authorities infrastructure, together with courts, a compromised Nigerian authorities judicial system, and programs in Bangladesh’s authorities community.
As well as, contaminated programs had been present in instructional establishments in Thailand, China, and South Korea.
WatchTowr handed over the accountability of managing the hijacked domains to The Shadowserver Basis to make sure that they won’t develop into obtainable for takeover sooner or later. Shadowserver is now sink-holing all visitors despatched from breached programs to its domains.
WatchTowr’s analysis, though not advanced, reveals that expired domains from malware operations may nonetheless serve new cybercriminals, who would additionally get some victims by merely registering the management domains.
