Over 25,000 publicly accessible SonicWall SSLVPN units are susceptible to essential severity flaws, with 20,000 utilizing a SonicOS/OSX firmware model that the seller not helps.
These outcomes come from an evaluation carried out by cybersecurity agency Bishop Fox, which was motivated by a sequence of necessary vulnerabilities disclosed this 12 months impacting SonicWall units.
Vulnerabilities affecting SonicWall SSL VPN units have been lately exploited by ransomware teams, together with Fog ransomware and Akira, as they’re a sexy goal for gaining preliminary entry to company networks.
Large assault floor
By leveraging web scanning instruments like Shodan and BinaryEdge and its proprietary fingerprinting methods, Bishop Fox recognized 430,363 publicly uncovered SonicWall firewalls.
Public publicity signifies that the firewall’s administration or SSL VPN interfaces are accessible from the web, presenting a chance for attackers to probe for vulnerabilities, outdated/unpatched firmware, misconfigurations, and brute-force weak passwords.
“The management interface on a firewall should never be publicly exposed, as this presents an unnecessary risk,” explains BishopFox.
“The SSL VPN interface, although designed to provide access to external clients over the internet, should ideally be protected by source IP address restrictions.”
When wanting into the firmware variations used on these units, the researchers found that 6,633 use Sequence 4 and 5, each of which reached the tip of life (EoL) years in the past. One other 14,077 use not supported variations of the now partially supported Sequence 6.
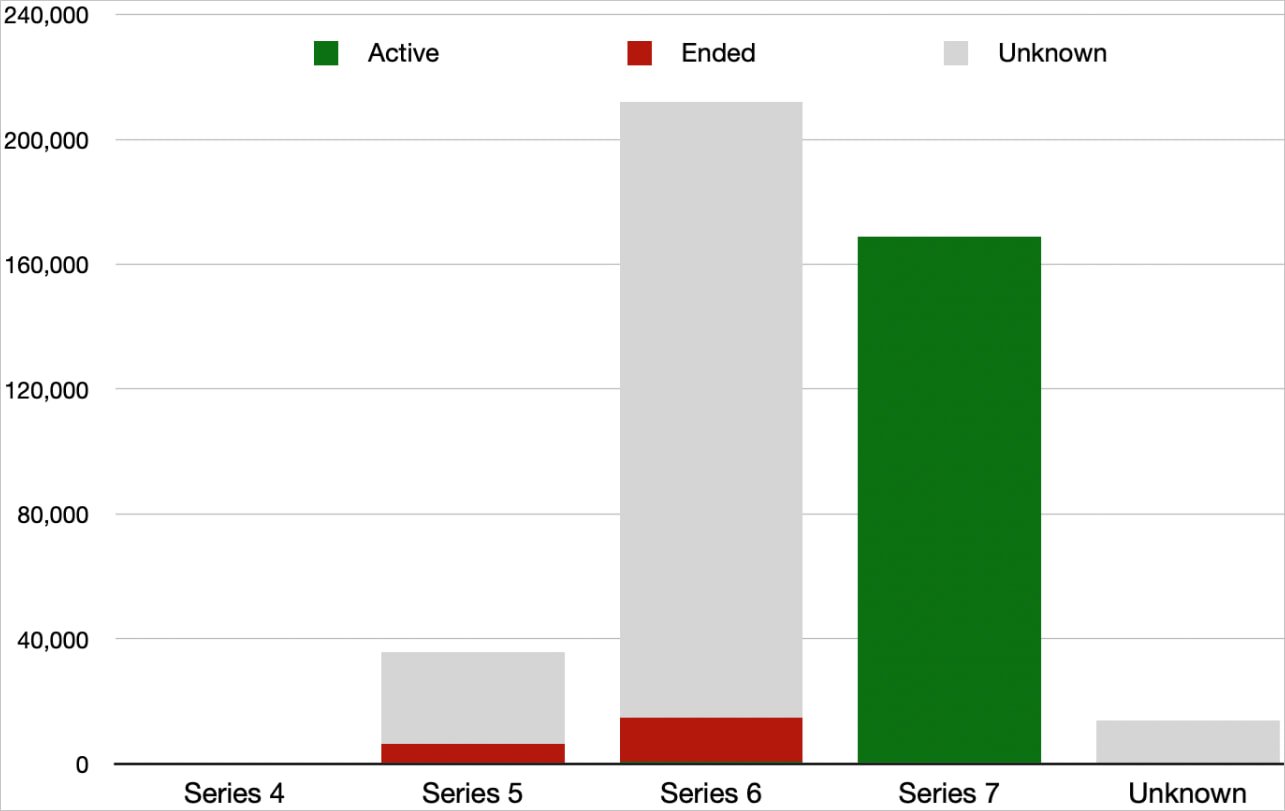
Supply: BishopFox
This leads to 20,710 units working end-of-life firmware being susceptible to many public exploits, however this determine just isn’t consultant of the correct scale of the issue.
BishopFox additionally discovered 13,827 working unknown firmware variations, 197,099 working unsupported Sequence 6 firmware, however for which it was not possible to find out the precise model, and one other 29,254 working an unknown model of Sequence 5 firmware.
When wanting into the scan outcomes utilizing fingerprinting expertise to determine the precise firmware variations and their safety towards identified vulnerabilities, the researchers decided that 25,485 are susceptible to essential severity points and 94,018 to excessive severity flaws.
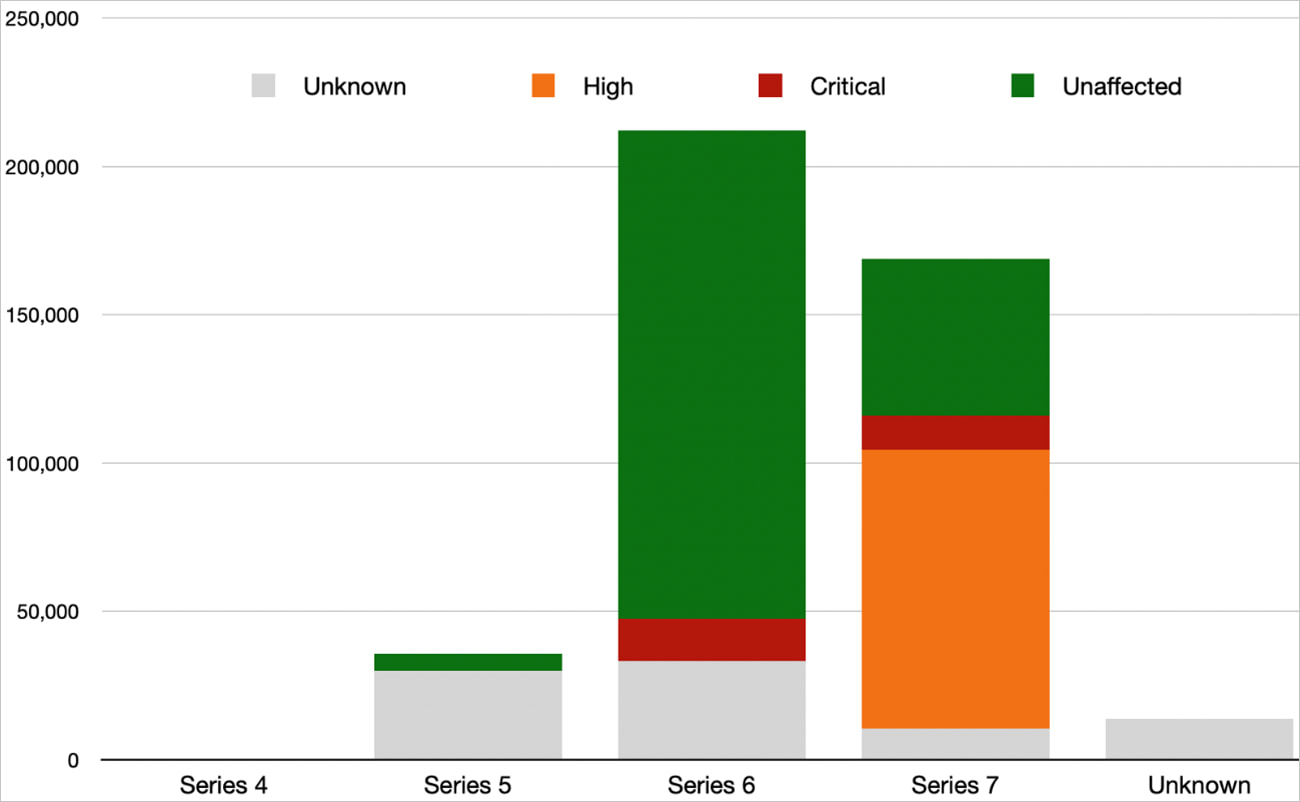
Supply: BishopFox
Many of the units confirmed to be susceptible are on the Sequence 7 firmware however haven’t been up to date to the most recent model, which closes safety gaps.
Whereas the whole of 119,503 susceptible endpoints is an enchancment over the 178,000 discovered susceptible to DoS and RCE assaults in January 2024, it is nonetheless indicative of gradual patch adoption.
