Google Play, the official retailer for Android, distributed over a interval of 1 12 months greater than 200 malicious purposes, which cumulatively counted almost eight million downloads.
The information was collected between June 2023 and April 2024 by menace intelligence researchers at Zscaler, who recognized and analyzed malware households each on Google Play and different distribution platforms.
The most typical threats the researchers found on the official Android app retailer embody:
- Joker (38.2%): Information-stealer and SMS message grabber that subscribes victims to premium companies
- Adware (35.9%): Apps that devour web bandwidth and battery to load both intrusive foreground advertisements or invisible advertisements within the background, producing fraudulent advert impressions
- Facestealer (14.7%): Fb account credential stealers that overlay phishing kinds on high of authentic social media purposes
- Coper (3.7%): Information-stealer and SMS message interceptor that may additionally carry out keylogging and overlay phishing pages
- Loanly Installer (2.3%)
- Harly (1.4%): Trojan apps that subscribe victims to premium companies
- Anatsa (0.9%): Anatsa (or Teabot) is a banking trojan that targets over 650 purposes of banks worldwide
Earlier this 12 months in Could, the identical researchers alerted of greater than 90 malicious apps on Google Play, with a obtain depend of 5.5 million.
Though Google has safety mechanisms to detect malicious purposes, menace actors nonetheless have some tips to bypass the verification course of. In a report final 12 months, the Google Cloud safety crew described the ‘versioning‘, a way that delivers malware via utility updates or by loading it from servers managed by the attacker.
Whatever the methodology used to ship malware via Google Play, some campaigns are extra profitable than others. Whereas Zscaler’s report centered on Android malware that’s extra frequent, different researchers found campaigns that additionally used Google Play to distribute malware to thousands and thousands.
In a single case, the Necro malware loader for Android was downloaded 11 million instances via simply two apps printed on the official retailer.
In one other case, the Goldoson Android malware was detected in 60 authentic apps that cumulatively had 100 million downloads.
Final 12 months, the SpyLoan was present in apps on Google Play that had been downloaded greater than 12 million instances.
Practically half of the malicious apps that Zscaler ThreatLabz found have been printed on Google Play below instruments, personalization, images, productiveness, and way of life classes.
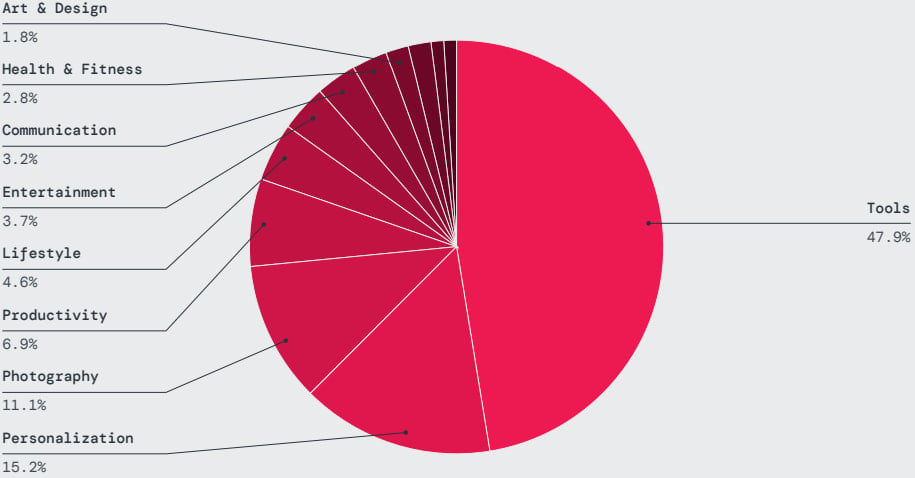
Supply: Zscaler
By way of malware blocks tried this 12 months, Zscaler reviews that the development reveals an general decline, as measured by blocked transactions.
On common, ThreatLabz recorded 1.7 million blocks monthly, with 20 million blocks recorded all through the evaluation interval, the commonest threats being Vultur, Hydra, Ermac, Anatsa, Coper, and Nexus.
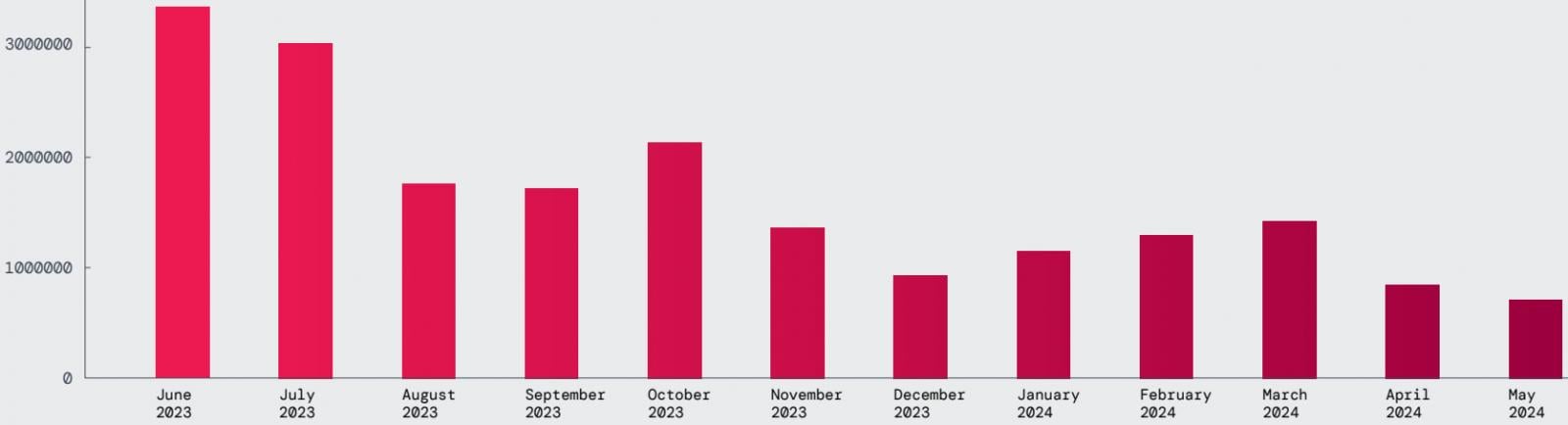
Supply: Zscaler
Zscaler’s cellular threats report additionally reveals a big enhance of adware infections, pushed primarily by SpyLoan, SpinOK, and SpyNote households. Prior to now 12 months, the corporate registered 232,000 blocks of adware exercise.
Essentially the most focused international locations by cellular malware previously 12 months have been India and the USA, adopted by Canada, South Africa, and the Netherlands.
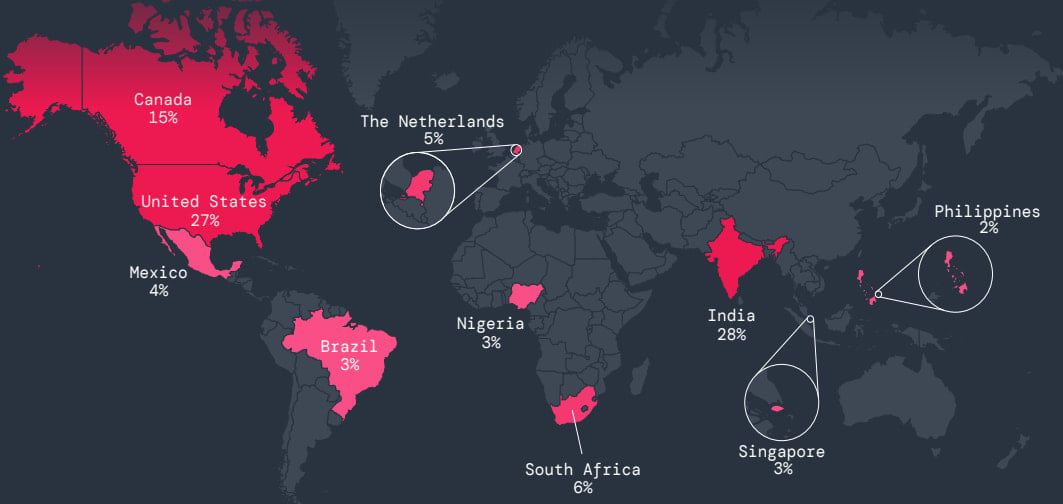
Supply: Zscaler
In accordance with the report, cellular malware focused principally the schooling sector, the place the quantity of blocked transactions elevated by 136.8%. The companies sector recorded a 40.9% enhance, and chemical compounds and mining a 24% enhance. All different sectors confirmed a common decline.
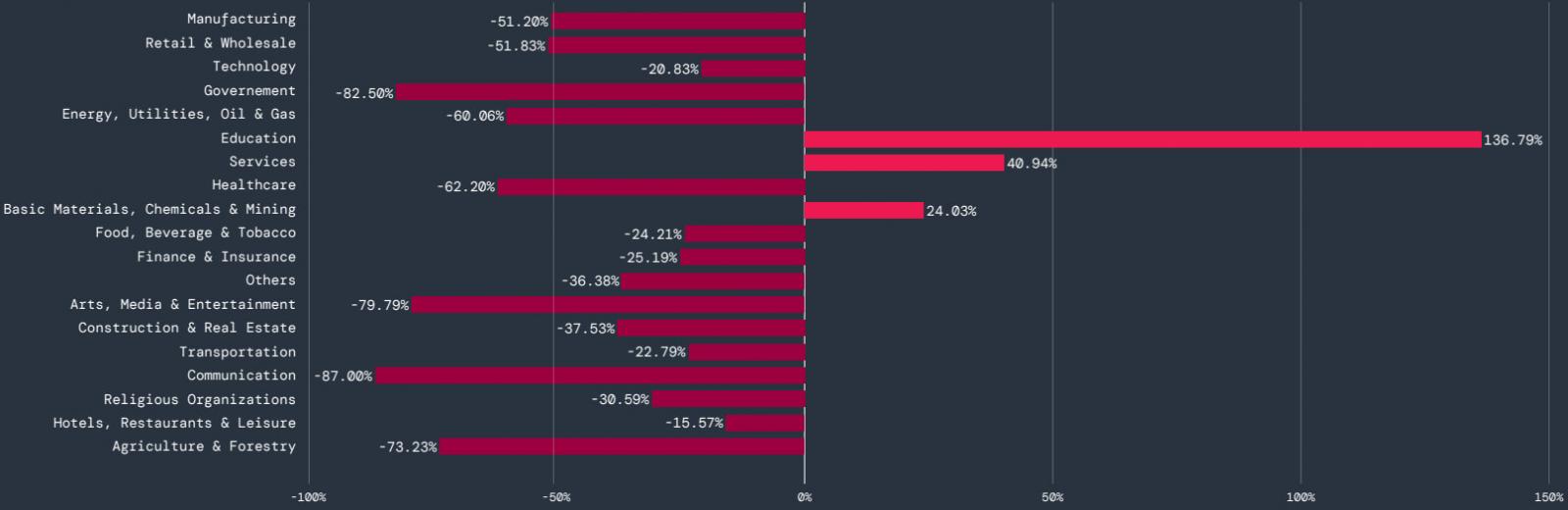
Supply: Zscaler
To attenuate the possibilities of getting contaminated by malware from Google Play, customers are suggested to learn opinions from others to see what issues have been reported and examine the appliance writer.
Customers also needs to examine the permissions requested at set up time and abort the method if the app requires permissions that don’t match its exercise.
.jpg)